Network Security

“Network security is defined as the activity created to protect the integrity of your network and data”
Any action intended to safeguard the integrity and usefulness of your data and network is known as network security. In other words, Network security is defined as the activity created to protect the integrity of your network and data.
Network security is the practice of protecting a computer network from unauthorized access, misuse, or attacks. It involves using tools, technologies, and policies to ensure that data traveling over the network is safe and secure, keeping sensitive information away from hackers and other threats.
Types Of Network Security
- Firewall Protection: Firewalls monitor and control incoming and outgoing network traffic based on predetermined security rules, acting as a barrier between trusted and untrusted networks.
- Encryption: Encrypting data ensures that sensitive information is only accessible to authorized parties, protecting it during transmission and storage.
- Intrusion Detection and Prevention Systems (IDPS): These systems identify and respond to potential threats by monitoring network traffic for suspicious act
Threats.
- Malware: Viruses, worms, ransomware, and spyware, which may enter the system and damage it or steal sensitive data.
- Distributed Denial-of-Service (DDoS) Attacks: Sending large amounts of traffic to a network or server in order to disrupt services.
- Unauthorized Access: The access of systems or data by intruders without permission, often through exploits or weak authentication.
- Phishing: Deception that involves tricking users into revealing sensitive information, such as passwords or financial details.
- Man-in-the-Middle (MitM) Attacks: Intercepting and changing communications between two parties without their knowledge.
Importance of implementing robust network security measures
The consequences of poor network security can be very severe, ranging from data breaches and financial losses to reputational damage and legal implications. There are several reasons why strong network security measures are important. It protects sensitive and personal information from theft or unauthorized access, thus ensuring data protection. Robust measures also ensure business continuity by keeping networks and systems operational and resilient against attacks. Besides, a robust network security is an assurance of the fulfillment of regulatory compliance of standards like GDPR, HIPAA, or PCI-DSS and avoid the legal and financial repercussions. Showing the commitment to security allows the organization to earn trust from customers, partners, and stakeholders. These also help prevent the financial impact of cyberattacks that can result in fines, downtime, and recovery costs.
References
Network Security Essentials: Applications and Standards (6th Edition). Network Security: Overview and Best Practices.
Top 5 Network Security Practices for Beginners
1. Us e Firewalls and Keep Them Updated
Firewalls are your first defense against threats. Set strict rules, update them often, and consider using both hardware and software versions.
2. Segment Your Network
Break your network into smaller sections to limit access and contain threats. Use VLANs or access controls to keep sensitive data separate.
3. Watch Your Network Traffic
Keep an eye out for unusual activity. Use tools like IDS/IPS, set alerts for strange patterns, and review logs regularly.
4. Keep Software and Firmware Updated
Don’t let outdated systems be an easy target. Enable automatic updates or check manually to fix vulnerabilities promptly.
5. Train Your Users
Teach users to spot phishing and use strong passwords. Encourage them to report anything suspicious and follow clear security rules.

Case Study: Equifax Breach (2017)
The 2017 Equifax breach is a stark reminder of how critical cybersecurity is for protecting sensitive data. Hackers exploited a known software vulnerability in Apache Struts that Equifax failed to patch in time. This lapse allowed attackers to access personal information of 147 million people, including Social Security numbers, birthdates, and addresses.
How the breach Occurred
Equifax is one of the top three consumer credit reporting agencies. On September 8, 2017, Equifax released a statement that it had been a victim of a cyberattack resulting in a massive data breach (Fruhlinger, 2019; Rajna, 2018). The world was shocked to learn that in this data breach, some 148 million US citizens’ sensitive personal data were compromised including names, dates of birth, Social Security numbers, and driver’s license numbers (Marinos & Clements, 2018). In addition to personal information, some 209,000 credit card numbers were also stolen (Perez, 2017). The severity and scope of the Equifax data breach were unprecedented at the time. Though they had previously been larger breaches, the sensitivity and criticality of the personal identifying information in the financial information in this breach created a problem whose magnitude could barely be calculated at the time. One of the issues that exacerbated the Equifax data breach was the fact that Equifax’s main product is essentially derived from a database containing many of the US population’s ,The data stored by Equifax contains each person’s personal credit history, which includes personal identifying information, known addresses, and account numbers. Further, the system is not an opt in system, as the data is gathered from businesses rather than the individuals listed in the database. When a person borrows money, lending institutions report the information about payment history, balances, and other key information items. When someone wants to borrow money, the new lender checks this information to assess the borrowers credit risk, which is used to make a lending decision


Preventive Measures:
Preventing breaches like Equifax’s involves timely software updates, robust patch management, and regular vulnerability assessments to close security gaps. Using firewalls, encrypting sensitive data, and segmenting networks can limit access and contain potential threats. Additionally, implementing user training programs and intrusion detection systems ensures proactive threat detection and mitigation.
Cheat Sheet: Secure Network Configurations
Firewall Rules
- Start with a “Deny All” policy: By default, block Only allow what’s absolutely necessary.
- Only open what you need: Keep your firewall rules tight—only open ports like 80 (HTTP), 443 (HTTPS), and maybe 22 (SSH).
- Shut down unused ports: If a service isn’t in use, turn off its The fewer open doors, the better.
- Whitelist trusted IPs: If you know which IPs should have access, limit incoming traffic to just
2. Port Management
- Close unnecessary ports: Regularly scan your systems and close any ports that don’t need to be
- Use non-standard ports when possible: For added security, pick non-standard ports for critical services, so they’re harder to find.
- Keep an eye on open ports: Make it a habit to check for any unexpected open ports or changes in your networ
3. Access Controls
- Least privilege is key: Users should only have access to what they absolutely need for their
- Use Multi-Factor Authentication (MFA): It’s one of the best ways to protect sensitive accounts and systems.
- Organize with roles: Group users by their job roles and give them access based on those
- Limit login attempts: Lock accounts after a few failed login attempts to protect against brute- force attacks.
4. Logging and Monitoring
- Turn on logging everywhere: Make sure to log activities on all critical systems, including firewalls, routers, and servers.
- Centralize your logs: Use a tool to gather and analyze logs in one place for better
- Review logs regularly: Take time to check logs for suspicious activity or signs of a
- Keep logs for the long term: Retain logs for a while so you can investigate any incidents if they arise
Practical Assesment:
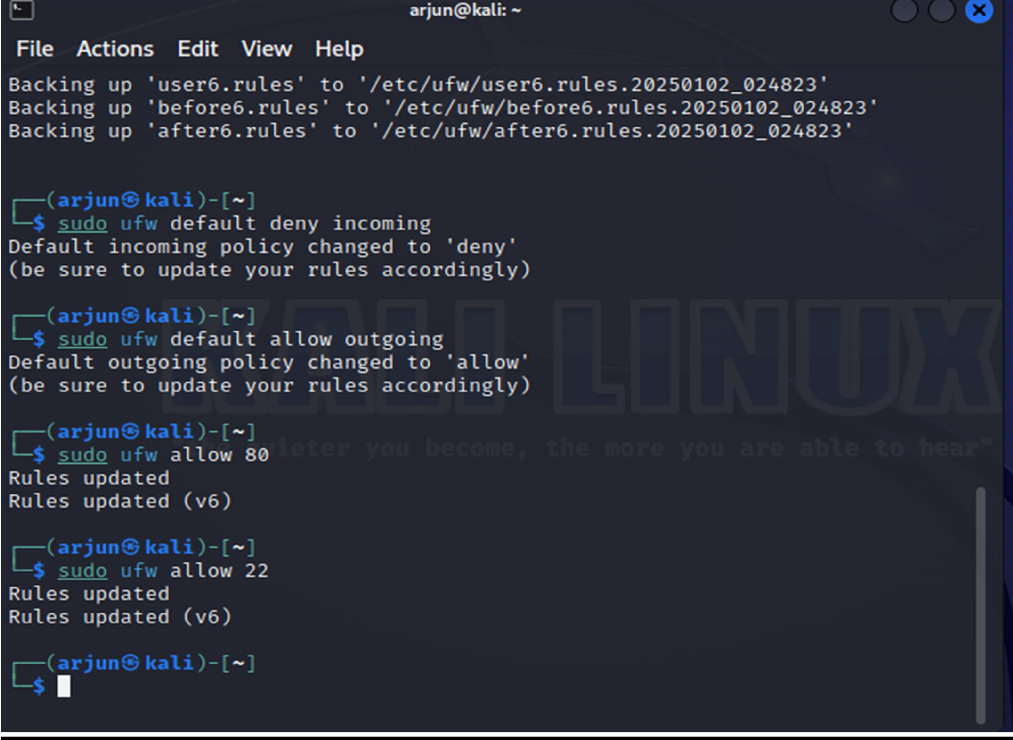
1.Installing the firewall
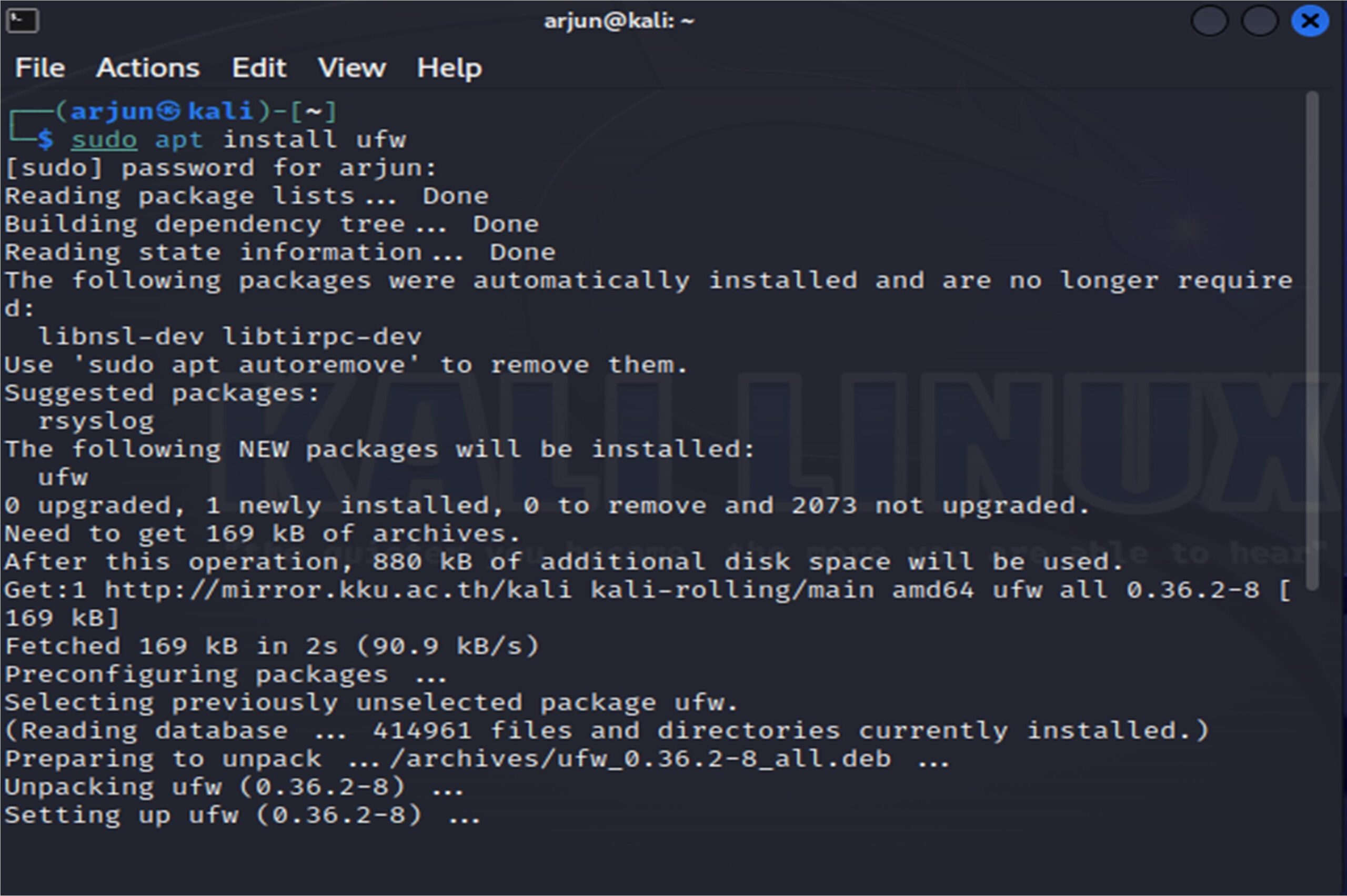
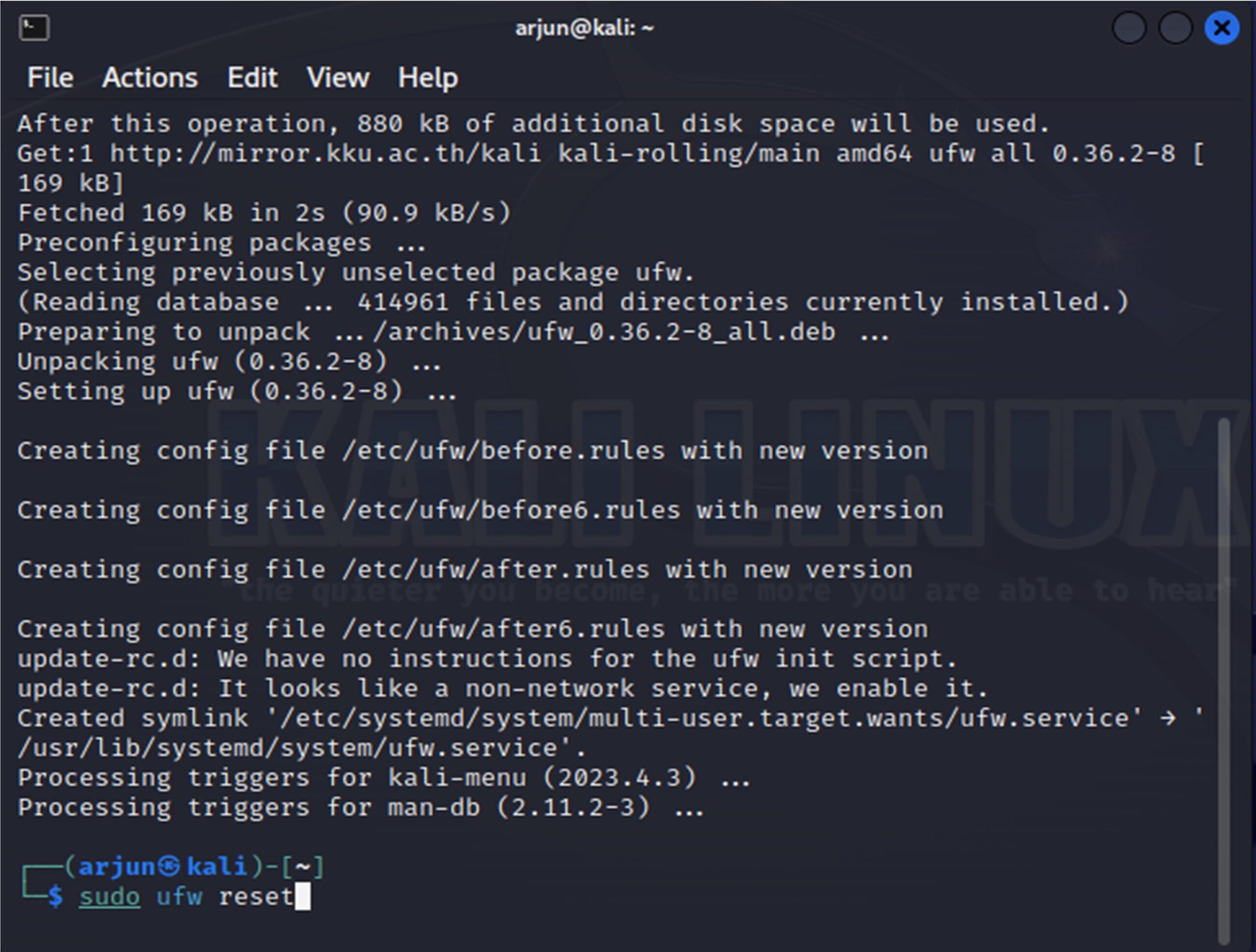
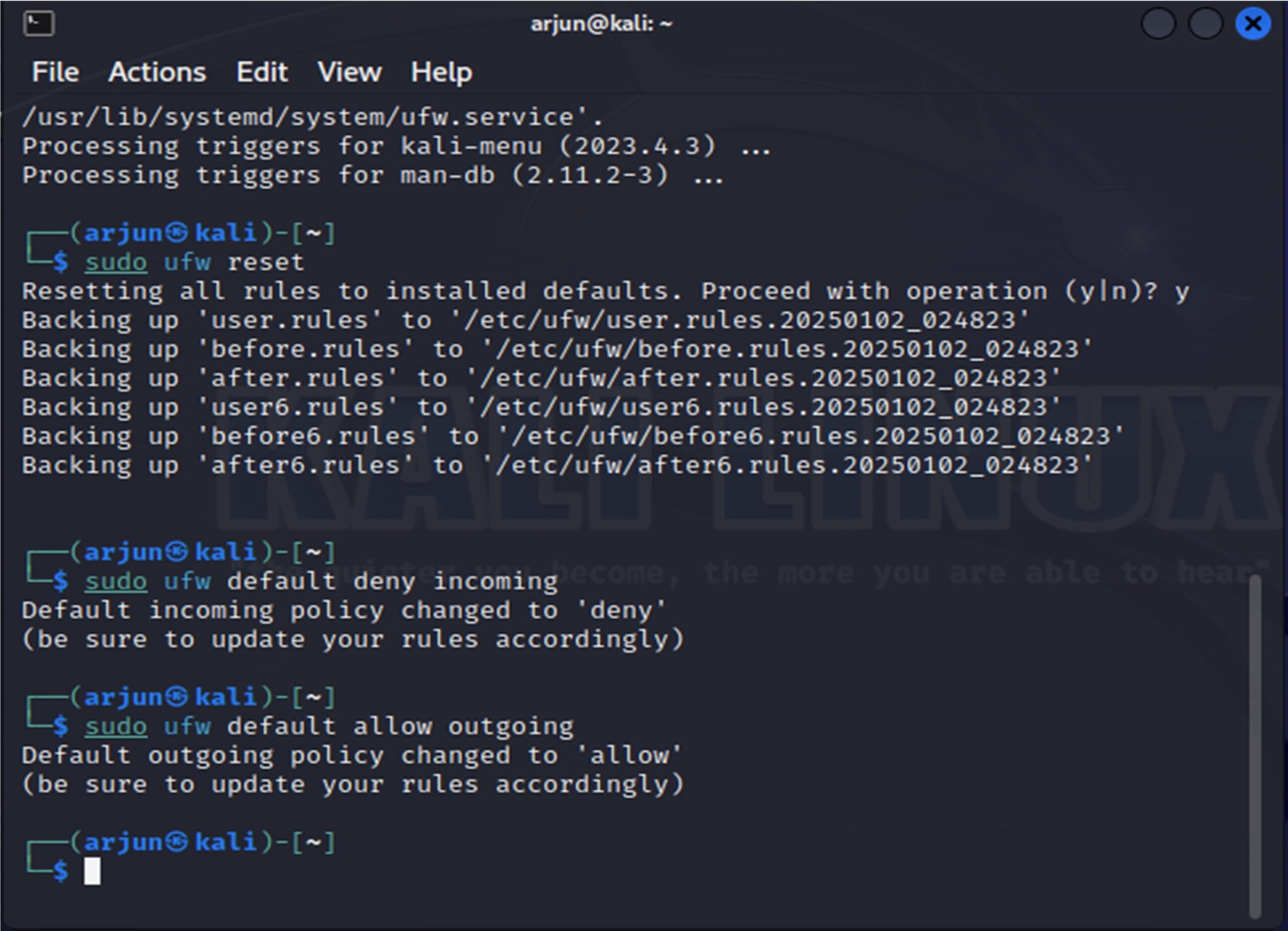
2. Reset it
3. Deny the incoming traffics and allow outgoing
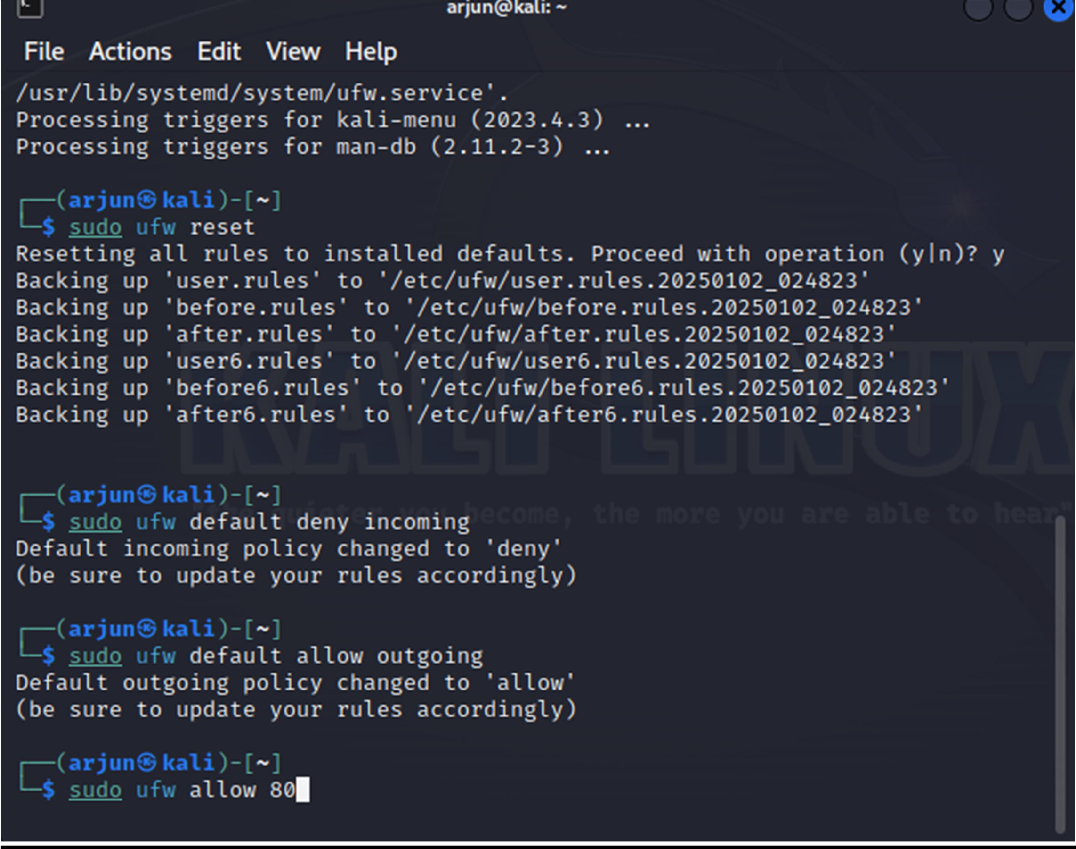
4. Allow port 80 that is http port
5. Allow traffic on port 22 SSH Port
6. Now check the status
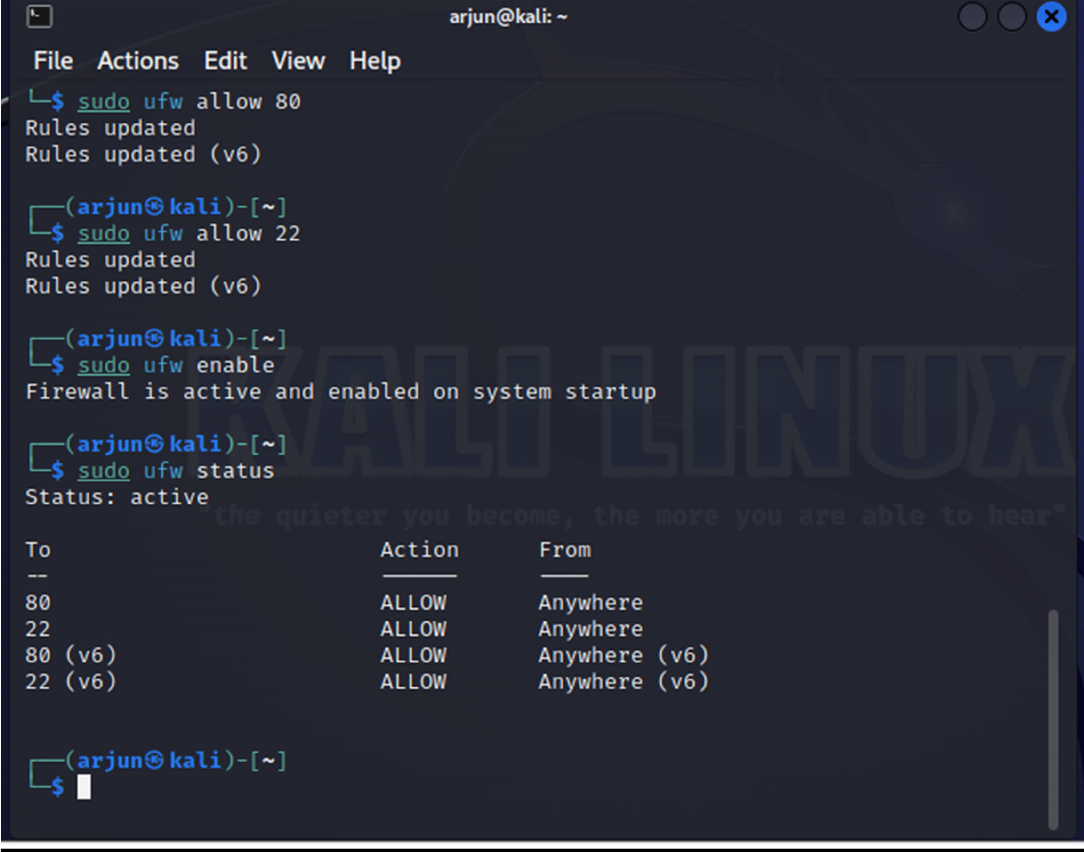
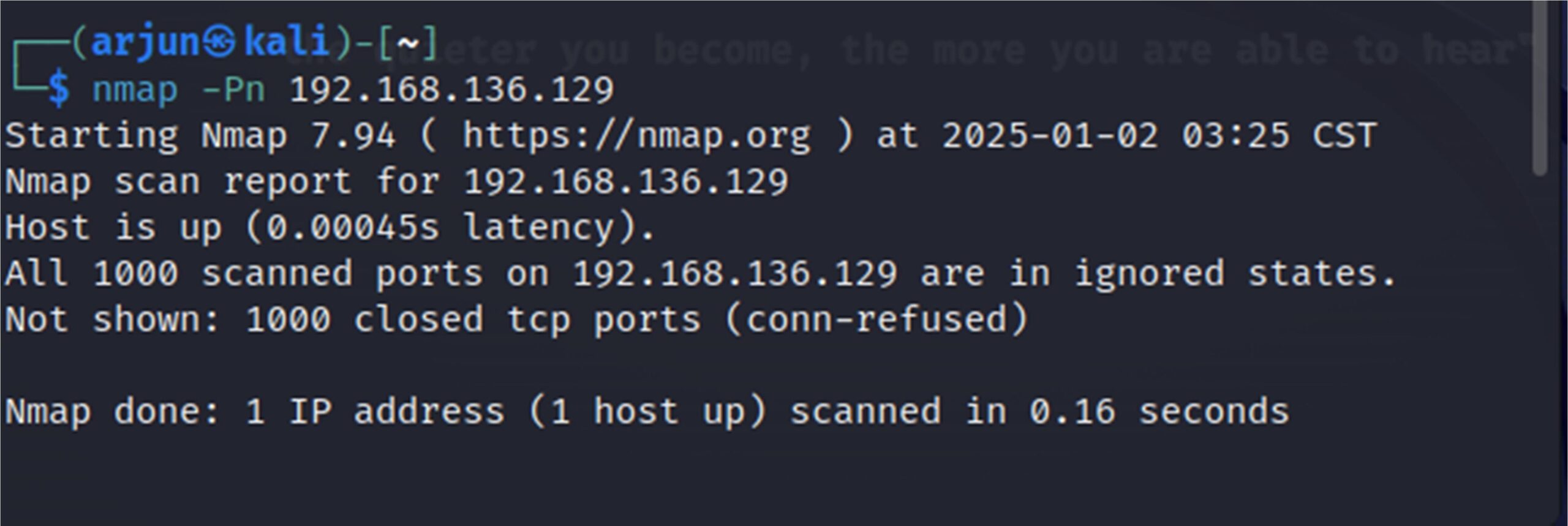
Practical Assesment 2 :Perform a Simple Port Scan
1.Performing a simple port scan
2. Performing the nmap sV scan to know more about the target ip
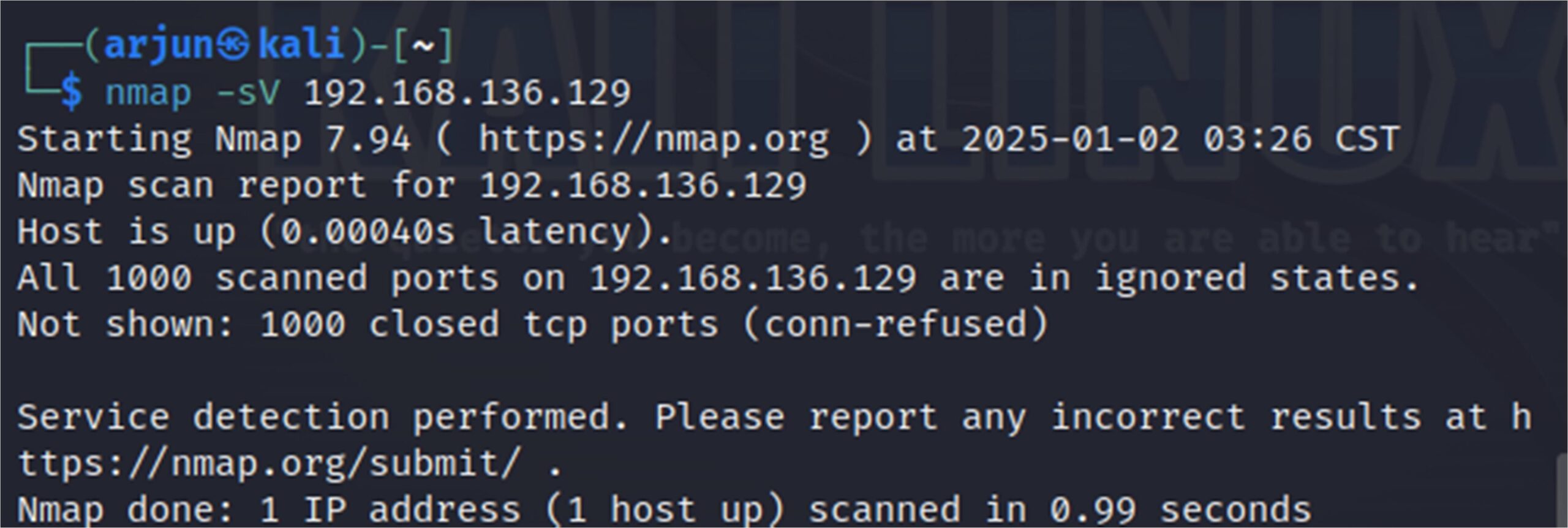
Couldn’t find any potential vulnerabilities in the target ip



