Meritshot Tutorials
- Home
- »
- Sniffing in Cyber Security
Cyber Security Tutorial
-
What is cybersecurity?What is cybersecurity?
-
Introduction to LinuxIntroduction to Linux
-
Text Processing using GREP, SED, and AWKText Processing using GREP, SED, and AWK
-
Introduction to Ethical HackingIntroduction to Ethical Hacking
-
Footprinting and ReconnaissanceFootprinting and Reconnaissance
-
Scanning NetworksScanning Networks
-
Enumeration in Cyber SecurityEnumeration in Cyber Security
-
Vulnerability AnalysisVulnerability Analysis
-
System HackingSystem Hacking
-
Malware ThreatsMalware Threats
-
SniffingSniffing
-
Social EngineeringSocial Engineering
-
Denial-of-ServiceDenial-of-Service
-
Evading IDS, Firewalls, and HoneypotsEvading IDS, Firewalls, and Honeypots
-
Hacking Web ServersHacking Web Servers
-
Hacking Web ApplicationsHacking Web Applications
-
SQL InjectionSQL Injection
-
Hacking Wireless NetworksHacking Wireless Networks
-
Hacking Web ApplicationsHacking Web Applications
-
Hacking Mobile PlatformsHacking Mobile Platforms
-
IoT HackingIoT Hacking
-
Cloud ComputingCloud Computing
-
CryptographyCryptography
Sniffing
Packet sniffing is a method of detecting and assessing packet data sent over a network. It can be used by administrators for network monitoring and security. However, packet sniffing tools can also be used by hackers to spy or steal confidential data.
The packet sniffing process is achieved by analyzing data packets sent through Transmission Control Protocol/Internet Protocol (TCP/IP) — the protocol that connects devices to wired or wireless networks. These data packets can include different types of traffic sent across a network, such as login details and passwords, as well as technical data like IP addresses.
IT professionals use packet sniffers for network troubleshooting by checking for harmful data packets. They also gain insights around bandwidth usage — for example, revealing which applications are the most intensive — to detect hidden issues affecting network performance.
Network administrators can also use packet sniffers to “sniff” websites that are being visited, the type of content being consumed, and communications like email.
Is packet sniffing legal?0
Packet sniffing is legal for the purposes of network management and when used only on the part of the network for which the person or organization conducting the sniffing is responsible. Packet sniffing is illegal when access to data packets is unauthorized. Hackers use packet sniffing to monitor and steal data, which is also an illegal use of packet sniffing.
Types of sniffing
Active Sniffing
Sniffing in the switch is active sniffing. A switch is a point to point network device. The switch regulates the flow of data between its ports by actively monitoring the MAC address on each port, which helps it pass data only to its intended target. In order to capture the traffic between target sniffers has to actively inject traffic into the LAN to enable sniffing of the traffic. This can be done in various ways.
Passive Sniffing
This is the process of sniffing through the hub. Any traffic that is passing through the non-switched or unbridged network segment can be seen by all machines on that segment. Sniffers operate at the data link layer of the network. Any data sent across the LAN is actually sent to each and every machine connected to the LAN. This is called passive since sniffers placed by the attackers passively wait for the data to be sent and capture them.
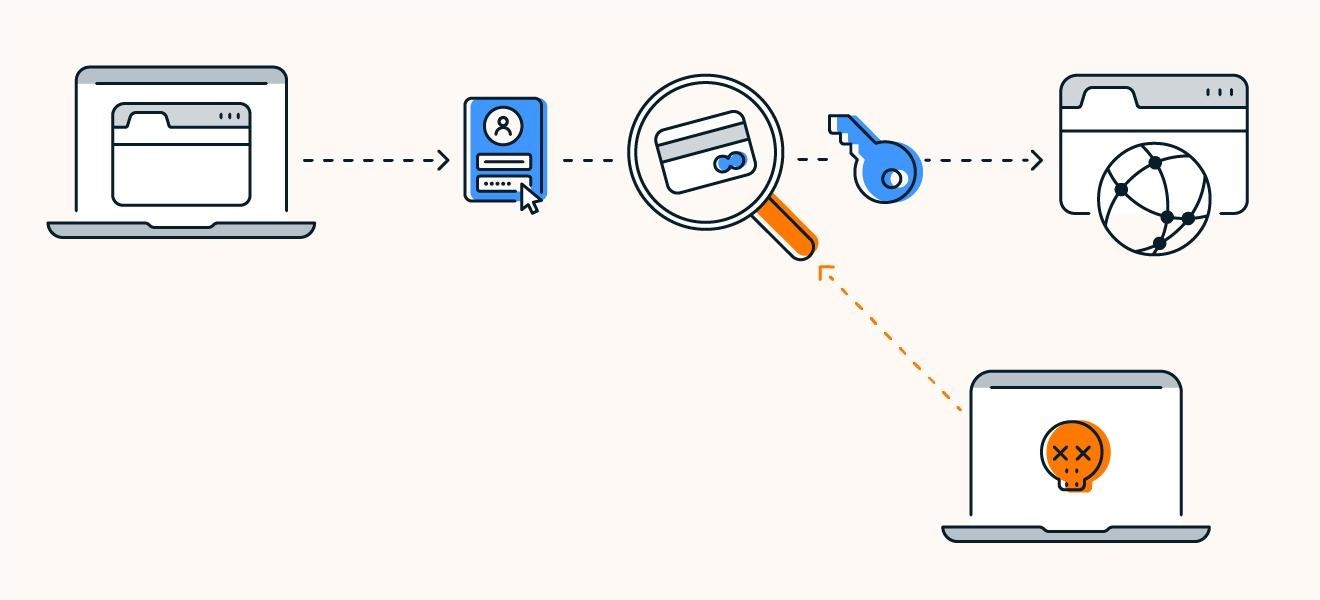
How does packet sniffing work?
Packet sniffers can be a piece of hardware or software that work by observing data moving between networked computers and between those devices and the internet. Sniffers are sometimes referred to as packet analyzers or network analyzers.
Typically, networks send and receive data as packets — segments of broken down information — to make it quicker and easier to manage. Then, the information is reassembled from the packets once the transfer is complete.
Devices connected to a specific network hub observe all data packets moving through the network and simply disregard any packets that aren’t intended for that destination. A packet sniffer is not configured in the same way and instead can receive all packets.
Some larger networks are “switched” — meaning they use a network switch to forward specific data only to the designated device, rather than to all network devices. Sniffing on a switched network requires additional protocols to ensure the packet sniffer can be monitored.
There are two main types of packet sniffing in cybersecurity:
- Hardware packet sniffing uses a physical device that plugs directly into a network interface — that is, the connection point between your computer and a network. This method is favored by IT experts who want to access specific parts of a network.
- Software packet sniffing uses a program to capture all traffic sent across the network. This type is much more popular today than hardware packet
Users can also decide whether they wish for all data packets to be captured and analyzed at a later date (known as unfiltered packet sniffing) or opt to capture only data packets that meet specific criteria (known as filtered packet sniffing).
Examples of packet sniffing attacks
➢ Heartland Payment Systems data breach (2009) An American payments processing company, Heartland Payment Systems was attacked with malware that allowed the sensitive financial information of their customers to be sniffed as the data crossed the network. The breach cost the company $12.6 million.
➢ Flame (2012) Flame is a sophisticated type of malware that includes a sniffer. The packet
sniffer has captured vast amounts of confidential data, including screenshots and audio files from countries in the Middle East. Flame is thought to be a form of state-sponsored espionage or cyber warfare, though the exact origin remains unknown.
➢ APT28 attack on hotel guests (2017) A Russian hacking group known as APT28, or “Fancy Bear,” used Wi-Fi sniffing to steal usernames, passwords, and other data from hotel guests in Europe and the Middle East. The attack also used malware and EternalBlue, which exploited vulnerabilities in More recently, in 2021, APT28 was also found to spread malware through unpatched vulnerabilities in Cisco routers.
What is the best defense against packet sniffing?
Here are several ways that can help protect your network from unwanted packet sniffing:
- Keep software updated. Regularly update your software and operating systems to patch vulnerabilities and prevent them from being exploited by different types of hackers.
- Use extra login security. Create strong passwords and enable additional authentication tools, such as two-factor authentication for extra layers of
- Use caution when opening emails from unrecognized addresses. Don’t click strange attachments or links, because they could be part of a phishing campaign that leads to a packet sniffing attack.
- Connect to the internet with a VPN. Using a Virtual Private Network (VPN) while browsing the web sends your data through an encrypted tunnel, shielding your online activity. This is particularly important when accessing public Wi-Fi, which usually has weaker protections that may increase the risk of a packet sniffing attack.
- Only visit secure websites. Ensure the sites you visit are secured with the HTTPS protocol, as sites with the HTTP protocol offer less
These days, most browsers flag unsecured websites in the address bar before you visit.
Sniffing Tools
BetterCAP − BetterCAP is a powerful, flexible and portable tool created to perform various types of MITM attacks against a network, manipulate HTTP, HTTPS and TCP traffic in real-time, sniff for credentials, and much more.
Ettercap − Ettercap is a comprehensive suite for man-in-the-middle attacks. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols and includes many features for network and host analysis.
Wireshark − It is one of the most widely known and used packet sniffers. It offers a tremendous number of features designed to assist in the dissection and analysis of traffic. Tcpdump − It is a well-known command-line packet analyzer. It provides the ability to intercept and observe TCP/IP and other packets during transmission over the network. Available at www.tcpdump.org.
WinDump − A Windows port of the popular Linux packet sniffer tcpdump, which is a command-line tool that is perfect for displaying header information.
OmniPeek − Manufactured by WildPackets, OmniPeek is a commercial product that is the evolution of the product EtherPeek.
Dsniff − A suite of tools designed to perform sniffing with different protocols with the intent of intercepting and revealing passwords. Dsniff is designed for Unix and Linux platforms and does not have a full equivalent on the Windows platform.
EtherApe − It is a Linux/Unix tool designed to display graphically a system’s incoming and outgoing connections.
MSN Sniffer − It is a sniffing utility specifically designed for sniffing traffic generated by the MSN Messenger application.
NetWitness NextGen − It includes a hardware-based sniffer, along with other features, designed to monitor and analyze all traffic on a network. This tool is used by the FBI and other law enforcement agencies.




