
Phishing: The Deceptive Hook Case Study
They said it was a legitimate email.clicked the link and lost everything."
A Deep Dive into Phishing
Abstract
In today’s digital landscape, phishing has become one of the most prevalent cyber threats, targeting individuals and organizations alike. Phishing is a deceptive technique where attackers impersonate legitimate entities to trick users into revealing sensitive information such as usernames, passwords, banking details, and personal identification data. These attacks commonly occur through fraudulent emails, fake websites, malicious links, text messages, and phone calls, exploiting human trust and social engineering tactics.
With the increasing reliance on online transactions, businesses and individuals face growing risks of financial fraud, data breaches, identity theft, and reputational damage. Cybercriminals continuously refine their tactics, using methods such as spear phishing (targeted attacks), vishing (voice phishing), smishing (SMS phishing), and Business Email Compromise (BEC) scams to bypass traditional security measures. These sophisticated attacks make detection challenging, as they often mimic trusted sources convincingly.
To combat phishing, various detection and prevention strategies are crucial. Techniques such as multi-factor authentication (MFA), email filtering, domain analysis, URL scanning, and cybersecurity awareness training play a vital role in reducing the success rate of phishing attacks. Strengthening cybersecurity infrastructure through proactive threat intelligence, continuous monitoring, and advanced security frameworks helps mitigate risks associated with phishing.
Building a strong cybersecurity culture is essential in preventing these attacks. Organizations and individuals must stay vigilant, adopt best practices, and utilize advanced security tools to protect their sensitive data. By enhancing awareness, implementing robust security protocols, and leveraging technology-driven solutions, the risks posed by phishing can be significantly minimized.
Keywords: Phishing, Cybersecurity, Social Engineering, Identity Theft, Online Fraud, Data Breach, Malware, Phishing Prevention, Cyber Threats, Multi-Factor Authentication (MFA), Spear Phishing, Smishing, Vishing, Business Email Compromise (BEC), Cybersecurity Awareness.
Introduction
The rapid growth of digitalization has transformed everyday life, making internet usage an essential part of personal and professional activities. From social media interactions to online banking and e-commerce transactions, individuals rely heavily on digital platforms for communication, financial management, and entertainment. However, as people share personal information, upload media, and conduct financial transactions online, cybercriminals exploit vulnerabilities to carry out malicious activities.
One of the most dangerous cyber threats today is phishing—a deceptive practice where attackers impersonate legitimate entities to trick individuals into revealing sensitive data such as usernames, passwords, banking details, and credit card information. These fraudulent schemes commonly involve emails, fake websites, text messages, and phone calls that appear to originate from trustworthy sources like banks, online marketplaces, or government agencies.
Phishing attacks often employ social engineering tactics to manipulate victims into taking harmful actions, such as clicking on malicious links, downloading malware, or entering confidential information on fraudulent websites. Cybercriminals use various phishing methods, including email spoofing, fake login pages, and misleading messages, to deceive users.
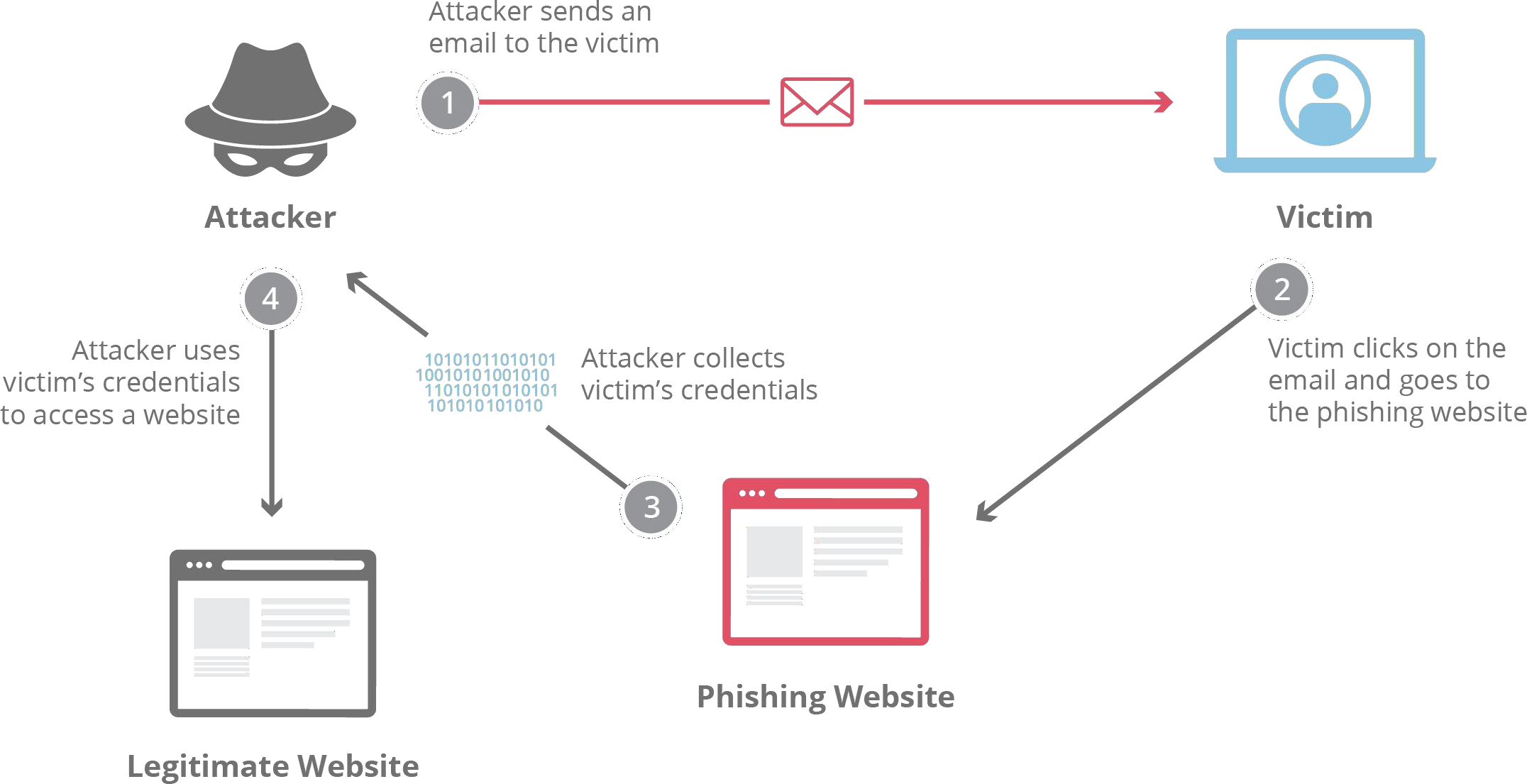
The process of a phishing attack typically follows these steps:
- The attacker sends a deceptive email or message to the victim, appearing to be from a trusted source.
- The victim clicks on the malicious link or opens an infected
- The fake website collects the victim’s credentials or installs malware on their
- The attacker uses the stolen credentials to gain unauthorized access to sensitive accounts or systems.
With the increasing sophistication of phishing techniques, individuals and organizations must adopt robust cybersecurity measures to prevent such attacks. Raising awareness, implementing multi-factor authentication (MFA), and using advanced security tools are crucial in minimizing risks associated with phishing. Understanding the evolving nature of these threats is essential to safeguard personal and organizational data from cybercriminals.
TYPES OF PHISHING ATTACK
- Deceptive Phishing
- The most common type of phishing, where attackers impersonate legitimate companies to steal personal information or credentials.
- Example: You receive an email that appears to be from PayPal, telling you that your account is at risk and requesting that you click a link to verify your account. The link leads to a fake PayPal page that collects your login
2. Spear Phishing
- A highly targeted form of phishing where the attacker customizes their message based on personal information about the victim, often gathered from social media.
- Example: A hacker sends an email pretending to be from your boss, asking you to approve a payment or transfer funds. The email looks convincing because it references internal projects or meetings only someone close to your boss would know about.
3. Whaling
- Targets high-profile individuals, such as CEOs or government officials, with highly personalized and sophisticated phishing attempts.
- Example: The CEO receives an email that appears to be from a trusted vendor, requesting an urgent transfer of funds to close a business deal. The email is carefully crafted, often using personal or sensitive details, making it appear
4. Clone Phishing
- The attacker replicates a legitimate email that the victim has previously received and replaces any legitimate links or attachments with malicious
- Example: You get an email that looks like a previous message from your bank about account maintenance. However, the link in the email leads to a fraudulent page that captures your login details.
5. Vishing (Voice Phishing)
- Involves phone calls, where attackers impersonate legitimate organizations (e.g., banks) to steal sensitive information over the phone.
- Example: You receive a phone call from someone claiming to be from your bank, warning you about suspicious activity in your account. They ask for your account number and PIN to verify your identity, but it’s actually an attempt to steal your details.
6. Smishing (SMS Phishing)
- Phishing attacks conducted via text messages, where attackers send links or prompts to victims to gain sensitive information.
- Example: You receive a text message claiming to be from your mobile provider, telling you that your account is locked and you need to click a link to unlock it. The link takes you to a fake login page designed to steal your
7. Pop-up Phishing
- A pop-up message appears on the victim’s browser, prompting them to enter personal details or download malicious software.
- Example: While browsing, a pop-up appears telling you that your system is infected and offering a free download of a virus Clicking on it installs malware on your system instead of cleaning it.
8. HTTPS Phishing
- The attacker creates a fake website with HTTPS encryption to give the impression of security, luring the victim to input sensitive data.
- Example: You receive an email from a “bank” with a link to “login” to your account. The website uses HTTPS and looks like the real bank’s site, but once you enter your credentials, they are stolen.
9. Evil Twin Phishing
- A fake Wi-Fi network is created to trick users into connecting to it, allowing the attacker to capture their data and credentials.
- Example: You’re at a coffee shop, and there’s a Wi-Fi network called “Free_Internet.” You connect to it, thinking it’s the coffee shop’s free Wi-Fi,
but it’s actually an evil twin set up by attackers to monitor your activity and steal your data.
10. Pharming
- Malicious software or DNS poisoning redirects users to fake websites, even when they type in the correct URL.
- Example: A hacker infects your computer with malware that changes your DNS settings. When you type in “amazon.com,” the browser redirects you to a fake website that looks like Amazon and steals your login credentials.
11. Watering Hole Phishing
- The attacker compromises websites frequented by a specific group (e.g., industry professionals) and infects visitors’ computers with malware.
- Example: Hackers compromise a website that you frequently When you visit the site, it delivers a malicious payload to your computer, stealing your personal information.
13. Business Email Compromise (BEC)
- Attackers impersonate a high-level employee or business partner to trick employees into transferring money or sensitive data.
- Example: A hacker impersonates the CEO of a company and sends an email to the finance team, requesting an urgent wire transfer to a specified The request appears legitimate because the hacker uses familiar email addresses or slight variations of the real one.
14. Man-in-the-Middle Phishing
- The attacker intercepts communication between the victim and a legitimate service (like a bank), capturing login credentials and other sensitive
- Example: While connected to a public Wi-Fi network, a hacker intercepts your communication with a website and injects fake login forms into the data flow. This redirects your credentials to the hacker’s server instead of the legitimate website.
17. Social Media Phishing
- Attackers use social media platforms to impersonate trusted contacts and manipulate victims into revealing personal information.
- Example: You receive a message from someone on social media claiming to be a friend, asking you to click on a link. The link leads to a fake login page where your social media credentials are stolen.
18. Fake Job Offer Phishing
- Scammers send fake job offers or recruitment emails, asking for personal details or payment for supposed background checks or application
- Example: You receive an email from a company offering you a job opportunity, with an attached document for you to The attachment contains a Trojan horse that infects your system when opened.
How Phishing Works:
Phishing is a deceptive cyber attack that tricks individuals into revealing sensitive information by impersonating a trusted source. Attackers use various communication methods, such as emails, social media, SMS, and even phone calls, to manipulate victims into providing personal or financial details.
1. Gathering Information
Phishers often collect publicly available data from social media platforms like LinkedIn, Facebook, or Twitter to make their attacks more convincing. By obtaining details such as names, job positions, email addresses, and interests, they craft messages that appear familiar and trustworthy.
2. Creating a Fake Message
Once attackers have enough information, they design messages that mimic a known contact, such as a company, coworker, or service provider. These messages usually create a sense of urgency, warning of account suspensions, security breaches, or offering exclusive deals to prompt immediate action.
3. Malicious Links and Attachments
Victims are targeted through links leading to fraudulent websites or attachments that contain malware. These fake websites look identical to legitimate platforms, tricking users into entering login credentials, credit card details, or other sensitive information. If an attachment is opened, malware can be installed on the victim’s device, giving attackers access to personal files or system controls.
4. Exploiting AI for Realistic Attacks
Cybercriminals increasingly use AI tools to generate phishing emails that appear more authentic. Unlike traditional scams that may have poor grammar or suspicious sender details, AI-driven phishing messages closely resemble legitimate communications, making detection more difficult.
5. Voice Phishing (Vishing)
Beyond emails and messages, attackers also use phone calls to impersonate trusted figures, such as managers or IT support. AI-generated voices can replicate familiar individuals, further deceiving victims into sharing passwords or authorizing financial transactions.
6. Execution and Data Theft
Once the victim interacts with the phishing attempt—whether by clicking a link, downloading a file, or sharing confidential details—the attacker gains access to the stolen data. This information can then be used for identity theft, financial fraud, or unauthorized system access.
Phishing remains one of the most effective cyber threats due to its reliance on human psychology rather than technical vulnerabilities. Awareness and caution are crucial in recognizing and avoiding such attacks.
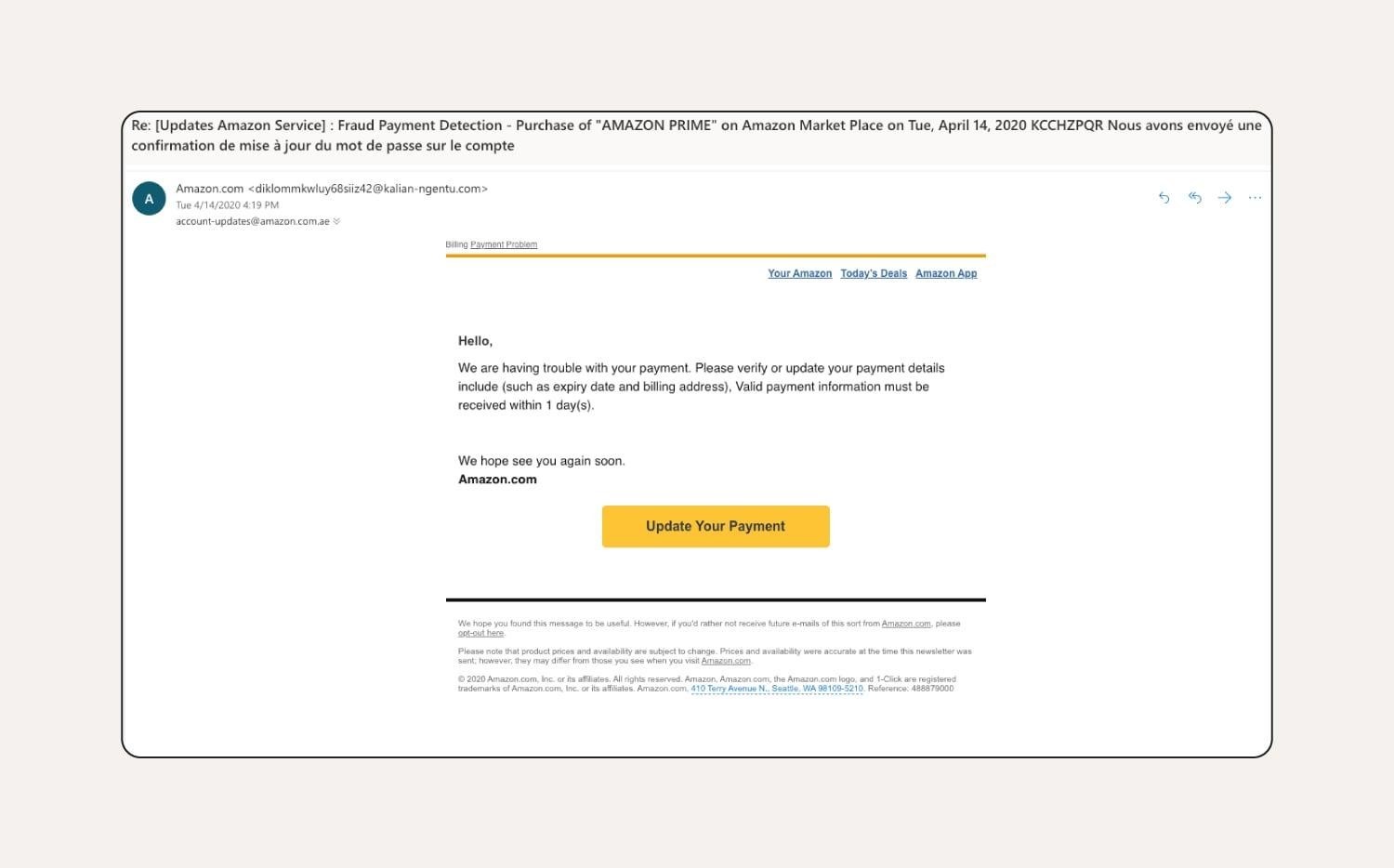
Phishing Activity Trends:
As per Anti Phishing Work Group report (APWG) submitted on the first and second quarter of 2024. The APWG observed almost five million phishing attacks over the course of 2023, which was a record year. In the first quarter of 2024, APWG observed 963,994 phishing attacks. This was the lowest quarterly total since 4Q 2021, and far below the 1,624,144 attacks seen in Q1 2023, which was the record-high quarter in APWG’s historical observations. Overall, the number of attacks per month has been stable from June 2023 through March 2024. The number of reports received was down, but the number of unique email campaigns was up 64 percent over Q4 2024, suggesting that phishers were diversifying their email subject lines in order to bypass email filtering. Recently there have also been fewer brand names reported to the APWG.
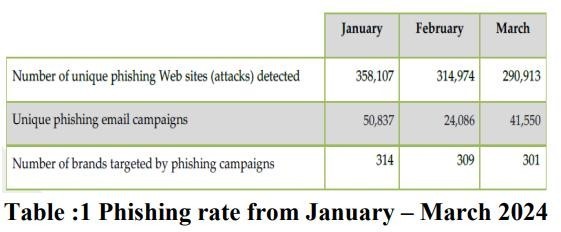
In above Table APWG gives the rate of phishing attack from Jan-March 2024 . The most targeted phishing attack detected in the website , the second most targeted platform is E-mail and third target is top brands company in the world .
Most-Targeted Industry Sectors – 1st Quarter 2024
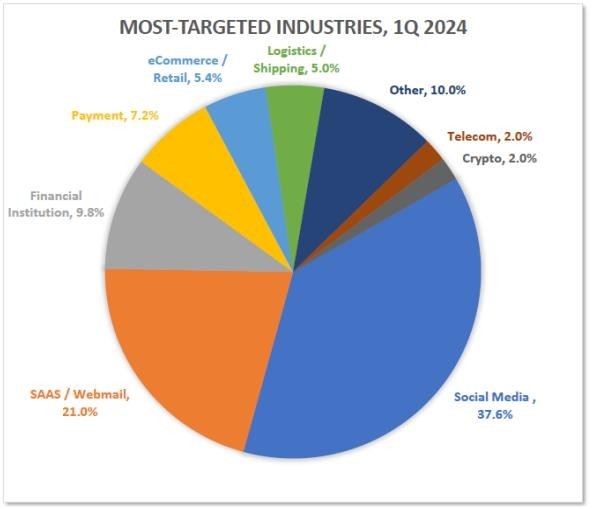
Targeted industry sectors
Above figure shows the chart for most targeted industry in the world . from above figure we can identify that the most targeted paltform for phishng activity is social media after that webmail come in the second attcak category .
Phone-Based Phishing:
Phone-Based Phishing, 1st Quarter 2024 APWG founding member OpSec Security found that the number of phone numbers used to perpetrate fraudulent activities has exploded over the last three years. Phone numbers used for fraud represented more than 20 percent of all fraud-related assets that OpSec identified in Q1 2024. OpsSec tallies fraud assets including fraudulent URLs (such as phishing URLs), phone numbers used in frauds, and email accounts used to perpetrate frauds (including those used for BEC attacks, job advertisement frauds, etc.).
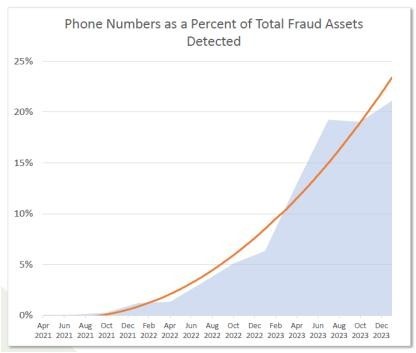
Phone based of phishing attack
Phone-based fraud is carried out through various methods, including voice phishing (vishing) and SMS-based phishing (smishing). In vishing, scammers make fraudulent phone calls to potential victims, while in smishing, they send text messages containing malicious links to phishing websites.
A particularly prevalent form of phone-based phishing is hybrid phishing. In this scam, the victim receives a fake purchase receipt via email, often for a few hundred dollars, urging them to call a customer support number within a short timeframe to dispute the charge. This tactic plays on urgency, a common social engineering
strategy. When the victim calls, the scammer attempts to collect sensitive personal or financial information or convinces them to transfer money or gift cards.
Matthew Harris, Senior Product Manager for Fraud at OpSec, noted that vishing and smishing began rising significantly in early 2021. This shift likely occurred as scammers moved away from lower-profit fraud methods to more lucrative schemes. Traditional email phishing is becoming less effective due to improved filtering technologies, making it harder for scammers to reach potential victims’ inboxes. In contrast, phone scams face fewer barriers—calls go directly to the recipient, and scammers can easily spoof caller IDs. Moreover, live conversations allow scammers to build trust, manipulate emotions, and deceive victims more effectively.
Business Email Compromise (BEC) Trends in Q1 2024
Payroll diversion remained a common tactic, accounting for 10.5% of BEC attacks. Both advance fee fraud and payroll diversion scams often trick victims into transferring funds to the scammer via wire transfer.
Fortra’s analysis revealed that the average amount requested in BEC wire transfer scams during Q1 2024 was $84,059—an increase of nearly 50% from the previous quarter’s $56,195. However, the overall number of wire transfer BEC attacks declined by 60%, suggesting that cybercriminals focused on fewer but higher-value scams.
John Wilson, Senior Fellow for Threat Research at Fortra, reported that nearly 60% of malicious emails targeting corporate inboxes in Q1 2024 aimed to steal login credentials, while 40% relied on response-based scams. Less than 0.5% attempted to deliver malware, highlighting that corporate email filters continue to struggle in detecting credential phishing and response-based attacks.
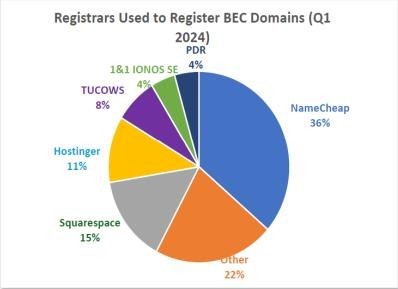
BEC based phishing attack
Hybrid vishing, which we rarely saw before 2023, made up 5.6 percent of Fortra’s engagements in the first quarter of 2024,” said Wilson.The hybrid vishing attacks we track typically begin as an email indicating the recipient has been charged for a product or service. The messages instruct the recipient to call a phone number if they wish to cancel their order and obtain a refund. Norton/LifeLock was the most popular brand used as a lure in these attacks, mentioned in 32 percent of the hybrid vishing messages we encountered in Q1 2024. McAfee was the second most popular lure, making up 29 percent of the Q1 attack messages. This was followed by Geek Squad (21%) and PayPal (17%).
Phishing rate from APR- Jun 2024.
Phishing Activity Trends Report – Q2 2024
During the second quarter of 2024, reported phishing incidents dropped to 877,536. This decline may be partly due to challenges in reporting, as email service providers have made it harder for users to submit phishing complaints to organizations like the Anti-Phishing Working Group (APWG), law enforcement, and other cybersecurity entities.
Despite this dip, phishing activity has remained relatively stable over the past year. A recent global study conducted by Interisle Consulting analyzed phishing trends from May 2023 to April 2024. The study, which compiled reports from APWG’s eCrime Exchange, OpenPhish, Spamhaus, and PhishTank, found a year-over-year increase of 50,000 phishing attacks, bringing the total to nearly 1.9 million. Additionally, APWG member OpSec Security observed a 10% rise in URL-based fraud in Q2 2024 compared to Q1 2024.
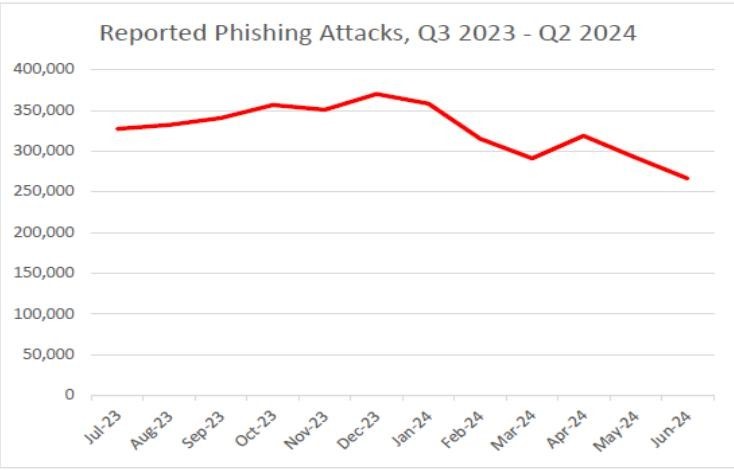
Most Targeted Industry Sectors – Q2 2024
In the second quarter of 2024, social media platforms remained the most targeted sector, accounting for 32.9% of all phishing attempts, according to OpSec Security. Meanwhile, phishing attacks targeting financial institutions such as banks held steady at 10%, a notable decrease from 24.9% in Q3 2023 and 14% in Q4 2023. Online payment services, including platforms like PayPal, Venmo, and Stripe, were also frequently targeted, making up 7.5% of all phishing attempts.
Matthew Harris, Senior Product Manager for Fraud at OpSec, highlighted a shift in phishing trends. He noted that cybercriminals are increasingly focusing on lower- security websites, including social media platforms like Facebook and LinkedIn, as well as SaaS and webmail services such as Microsoft Outlook and Netflix. One reason for this shift is the growing use of advanced email filtering technologies, which make it harder for phishing emails to reach users’ inboxes.
Additionally, banks and financial institutions have strengthened their security measures, often requiring two-factor authentication (2FA) for online transactions. Since phishing via traditional email scams has become less effective, cybercriminals are turning to phone-based tactics. These include:
- Voice phishing (vishing): Scammers call potential victims and attempt to extract sensitive information.
- SMS phishing (smishing): Fraudsters send text messages containing links to phishing sites, tricking users into revealing personal data.
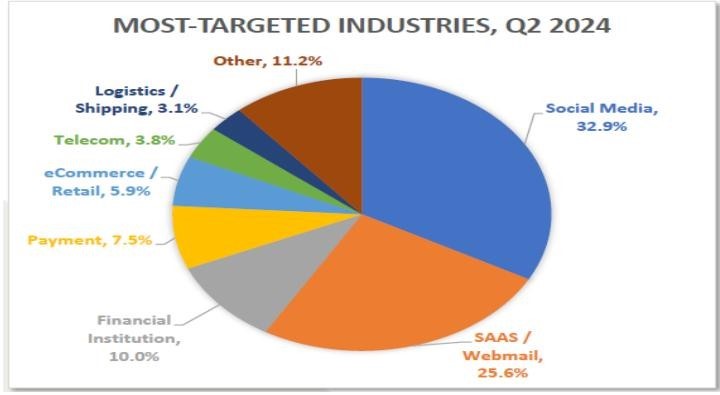
Most targeted indutry in Q2 2024
Business Email Compromise (BEC) – Q2 2024
Fortra, a member of the Anti-Phishing Working Group (APWG), monitors Business Email Compromise (BEC), a form of cyber fraud where attackers impersonate trusted individuals—such as employees, vendors, or executives—to deceive victims into transferring funds or sharing confidential information. According to the FBI’s Internet Crime Complaint Center (IC3), BEC scams led to financial losses of $2.9 billion in the U.S. in 2023.
During the second quarter of 2024, Fortra analyzed thousands of BEC attempts and found that the average amount requested in wire transfer scams was $89,520. This reflects a 6.5% increase from the previous quarter’s average of $84,059. However, the overall number of wire transfer BEC attempts declined by 8.4% compared to Q1 2024.
The findings indicate that cybercriminals have not significantly altered their strategies but continue to refine their approach to maximize financial gains. As BEC scams remain a major cyber threat, organizations must implement strong email security measures to mitigate risks.
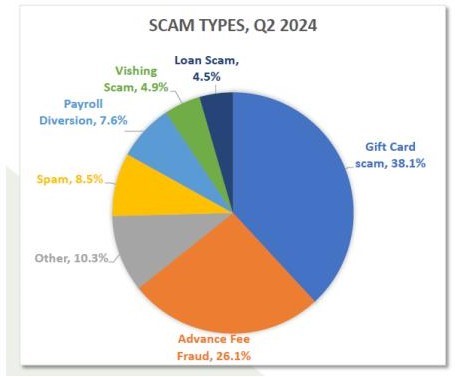
Scam report in Q2
Gift card scams remained the most prevalent form of fraud in the second quarter of 2024, accounting for 38.1% of all attacks tracked by Fortra. Advance fee fraud was the second most common scam, making up 26.1% of incidents, while payroll diversion schemes represented 7.6% of cases.
A notable trend in Q2 2024 was the rise of hybrid vishing, which accounted for 4.9% of tracked scams. This tactic typically begins with an email falsely claiming that the recipient has been charged for a product or service. The email instructs the recipient to call a provided phone number to cancel the charge and request a refund.
According to John Wilson, Senior Fellow in Threat Research at Fortra, Norton/LifeLock was the most frequently impersonated brand in hybrid vishing scams, appearing in 39% of phishing messages. Geek Squad was the second most- used lure at 25%, followed by PayPal (22%) and McAfee (6%).
In addition to phishing tactics, cybercriminals relied on specific domain strategies to conduct Business Email Compromise (BEC) attacks. Fortra’s analysis revealed that 72% of BEC attacks in Q2 2024 were carried out using free webmail domains, a figure nearly identical to the 73% recorded in Q1. The remaining 28% of attacks involved either newly registered malicious domains or compromised legitimate email accounts.
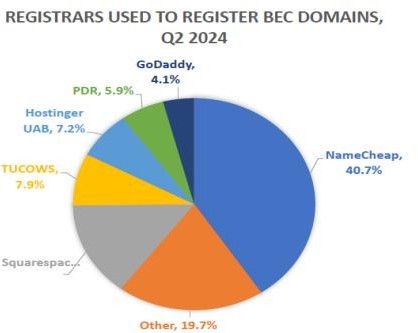
BEC Domain attack
In the second quarter of 2024, Google’s Gmail emerged as the most commonly used free webmail service for Business Email Compromise (BEC) scams, accounting for 72.4% of webmail-based BEC attacks. Microsoft’s webmail services, such as Outlook, were used in 16.3% of these attacks, far surpassing other free webmail providers.
Fortra also highlighted that 35% of payroll diversion attempts sought to reroute victims’ salaries to accounts at Green Dot, a financial services company. GoBank, also owned by Green Dot, ranked as the third most commonly targeted financial institution for payroll diversions. This pattern suggests that Green Dot may not be adequately performing its customer verification duties, potentially violating the Know Your Customer (KYC) requirements outlined by FINRA Rule 2090.
As fraudsters continue to exploit webmail services and financial institutions, organizations must strengthen their defenses and improve verification processes to prevent such attacks.
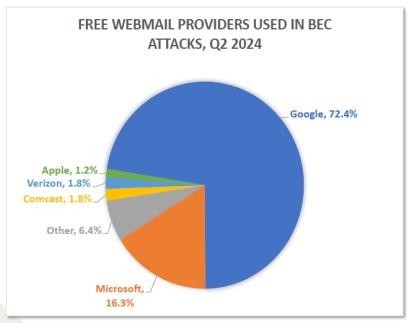
Most targeted Webmail attack
Prevention of Phishing Attacks
Phishing attacks are deceptive cyber threats designed to steal personal and financial information through spam emails, pop-ups, or fraudulent messages. Once an attacker gains access to sensitive data, they can misuse it for identity theft, financial fraud, or other malicious activities. Since phishing is one of the most cunning forms of cyber deception, it is crucial to understand preventive measures to safeguard personal and organizational security.
1. Guard Against Suspicious Emails and Spam
Many phishing attacks originate from unknown or suspicious senders, requesting sensitive details under the pretense of verification or security checks. To prevent falling for such scams:
- Avoid responding to unexpected requests for personal or financial information via email.
- Mark phishing emails as spam and report
- Use email filters to detect and block suspicious
2. Verify Secure Websites Before Entering Information
When conducting online transactions or sharing confidential information, always check if the website is secure:
- Look for “https://” in the URL instead of “http://.” The “s” stands for secure communication.
- Verify the presence of a lock icon in the address bar before entering any
- Avoid clicking on pop-up forms requesting personal
3. Avoid Clicking on Suspicious Links or Attachments
Phishing emails often contain malicious links and attachments designed to install malware or direct users to fraudulent sites. To stay protected:
- Do not click on links from unknown Hover over them to preview the destination.
- Avoid downloading attachments unless you are expecting them and trust the
- Confirm with the sender directly if you receive an unexpected email with an
4. Implement Strong Security Policies in Organizations
Businesses and large organizations must establish strict security measures to reduce the risk of phishing attacks:
- Implement guidelines on handling suspicious emails and
- Train employees on cybersecurity best
- Enforce multi-factor authentication (MFA) for accessing sensitive
5. Conduct Security Awareness Training
One of the most effective ways to prevent phishing is by educating employees and users about common phishing techniques. Organizations should:
- Train staff to recognize phishing emails and fake
- Conduct simulated phishing attacks to test employees’
- Provide regular security updates to reinforce best
6. Essential Tips to Protect Against Phishing Emails
- Never share passwords via IT departments will never ask for them.
- Be cautious with attachments—they may contain If you receive an unexpected attachment, verify with the sender before opening it.
- Avoid entering personal details in pop-up windows, as they may be fake forms designed to steal data.
- Check for spelling and grammar mistakes in Many phishing messages contain errors that legitimate companies would not allow.
- Use security software with email filtering and real-time threat
Detection of Phishing Attacks
The internet is a vast resource that enables people to access information, conduct transactions, and communicate globally. However, various online platforms such as Facebook, Twitter, Gmail, Dropbox, PayPal, eBay, and banking portals have fraudulent counterparts designed to deceive users. These deceptive sites, known as “phish,” closely resemble legitimate websites to steal sensitive information such as login credentials, financial data, or personal details. Detecting phishing attacks is crucial in preventing cyber fraud, and several methods can help identify and avoid these threats.
1. Use Custom DNS Services
Custom DNS resolution services provide an added layer of security by filtering malicious websites. Typically, when a user accesses a website, the system queries a DNS resolver to obtain its IP address. While standard ISP-provided DNS servers only resolve website names, independent DNS services offer enhanced security by blocking access to known phishing or malware-infected sites. Using secure DNS providers ensures that users do not unintentionally visit harmful websites.
2. Utilize Your Browser’s Phishing Protection
Modern web browsers include built-in phishing detection tools that automatically check if a visited website is potentially dangerous. These browsers maintain updated phishing lists and warn users when they attempt to access fraudulent sites. To maximize security, always ensure browser settings are configured to enable phishing protection and regularly update your browser.
3. Verify Links Before Clicking
Phishing attempts often involve misleading links embedded in emails, text messages, or pop-up ads. Users should be cautious and verify links before clicking by:
- Hovering over links to preview the actual
- Using online tools that analyze website credibility and detect suspicious
- Avoiding shortened URLs from unknown sources, as they may redirect to malicious sites.
4. Rely on Personal Awareness and Analysis
Personal vigilance plays a crucial role in detecting phishing scams. Users should:
- Examine email headers for inconsistencies in sender
- Be skeptical of urgent messages requesting sensitive
- Avoid providing personal data unless certain of the recipient’s
5. Look for Secure Website Indicators
Legitimate websites use secure connections to encrypt user data. Indicators of a secure website include:
- HTTPS protocol instead of HTTP in the
- A padlock icon in the browser’s address bar, confirming a valid security
- Consistency in website appearance, as fraudulent sites may have design flaws or outdated content.
6. Check for URL Manipulation
Cybercriminals often manipulate URLs to resemble well-known websites. Some common signs of phishing URLs include:
- Misspelled domains (e.g., “paypa1.com” instead of “paypal.com”).
- Extra characters or hyphens added to mimic real
- Subdomains that impersonate legitimate companies (e.g., “secure-bank- example.com”).
Recognizing Phishing Emails
Phishing emails are crafted to appear as legitimate communications from trusted companies. These messages may contain corporate logos and branding to deceive recipients. However, certain red flags indicate a phishing attempt:
- Suspicious URLs or domain names: The email might contain links with typos or unusual characters.
- Non-corporate sender addresses: Official emails from banks or service providers do not come from generic domains like @gmail.com or @yahoo.com.
- Urgent or fear-inducing language: Scammers use psychological tactics to pressure users into acting quickly.
- Requests for sensitive information: Legitimate companies never ask for passwords or financial details via email.
- Grammatical or spelling errors: Poorly written messages often indicate fraudulent activity.
Common Phishing Tactics
Scammers frequently update their methods to trick users. Some of the most common phishing tactics include:
Fake security alerts: Claiming unauthorized access or suspicious login attempts.
False account issues: Requesting verification due to a supposed problem with payment details.
Fake invoices: Sending unexpected payment requests.
Malicious attachments: Including infected files disguised as documents or receipts.
Fake offers: Promising government refunds or fake rewards.
Identifying and Preventing Phishing Phone Calls Understanding Phishing Phone Calls
Phishing phone calls are deceptive attempts by scammers to steal personal and financial information. These calls often impersonate legitimate businesses, financial institutions, or government agencies to manipulate the recipient into providing sensitive details. Scammers use psychological tactics to create urgency and pressure victims into making quick decisions.
Common Signs of a Phishing Phone Call
Being aware of the red flags can help in identifying phishing calls. Here are some warning signs:
- Claims that you have been “specially selected” for an
- Promises of a free reward upon
- Notifications about winning a lottery or a valuable
- Offers of high-return, low-risk
- Pressure to make immediate
- Statements like “You trust me, right?”
- Discouragement from verifying their
- Requests for payment of fees via credit card for handling or
How to Protect Yourself from Phishing Calls
To prevent falling victim to these scams, follow these precautions:
- Avoid engaging with unknown Genuine companies allow you time to research them.
- Verify unfamiliar businesses through consumer protection agencies or the Better Business Bureau.
- Request full details of the caller, including their name, company, phone number, and address.
- Do not pay for “free prizes”—this is illegal in many
- Never share sensitive information such as banking details, credit card numbers, Social Security numbers, or birthdates over the phone.
- Be wary of callers offering to help recover lost funds for an upfront fee, as this is another form of fraud.
Steps to Take If You Receive a Suspicious Call
If you suspect a phishing call, take these actions:
- Search the phone number Many scam calls are reported on websites such as 800notes.com and callercenter.com.
- Do not feel pressured to respond Scammers rely on urgency to manipulate victims.
- Keep your personal and financial details Do not confirm or share sensitive information.
- Request written details before making any
- Be cautious of callers claiming they can recover lost funds for a
- Report aggressive or threatening calls to authorities, even if you have already sent money. Scammers often target previous victims again.
Conclusion
Phishing continues to be a significant security challenge for both individuals and organizations. While there are various mitigation strategies available, proactive anti- phishing training plays a critical role in building a comprehensive defense against these attacks. This case study has examined the factors contributing to phishing, the trends in phishing attacks, and effective prevention techniques.
Based on the findings, we highlight that current anti-phishing tools and methods often fail to address all the critical elements necessary for comprehensive protection. Key aspects of an effective anti-phishing program should include automation, individualization, and continuous optimization of training parameters. These factors are essential because some parameters, as highlighted in existing research, are either inconclusive or contradictory, suggesting a need for further investigation and refinement.
Moreover, an anti-phishing solution must foster collaboration within the community. This could involve sharing threat intelligence, such as email templates or co-designed training materials, to strengthen collective defense efforts. Despite the advanced capabilities of current anti-phishing tools, they often cover only a limited range of necessary factors, making it essential to develop more comprehensive solutions that can significantly reduce phishing susceptibility among users.
Additionally, creating dedicated platforms like a Cyber Lab for improved detection techniques could contribute to better phishing prevention strategies. Such platforms can facilitate the identification of new threats and encourage collaboration among experts to develop solutions.
In conclusion, increasing awareness of phishing techniques and strengthening defenses will enhance overall security. Proactive training, continuous refinement of tools, and collaboration across the community are key to building a more resilient and secure environment for all users.





