Meritshot Tutorials
- Home
- »
- IoT Hacking in Cyber Security
Cyber Security Tutorial
-
What is cybersecurity?What is cybersecurity?
-
Introduction to LinuxIntroduction to Linux
-
Text Processing using GREP, SED, and AWKText Processing using GREP, SED, and AWK
-
Introduction to Ethical HackingIntroduction to Ethical Hacking
-
Footprinting and ReconnaissanceFootprinting and Reconnaissance
-
Scanning NetworksScanning Networks
-
Enumeration in Cyber SecurityEnumeration in Cyber Security
-
Vulnerability AnalysisVulnerability Analysis
-
System HackingSystem Hacking
-
Malware ThreatsMalware Threats
-
SniffingSniffing
-
Social EngineeringSocial Engineering
-
Denial-of-ServiceDenial-of-Service
-
Evading IDS, Firewalls, and HoneypotsEvading IDS, Firewalls, and Honeypots
-
Hacking Web ServersHacking Web Servers
-
Hacking Web ApplicationsHacking Web Applications
-
SQL InjectionSQL Injection
-
Hacking Wireless NetworksHacking Wireless Networks
-
Hacking Web ApplicationsHacking Web Applications
-
IoT HackingIoT Hacking
-
Cloud ComputingCloud Computing
-
CryptographyCryptography
IoT Hacking in Cyber Security
What is IoT hacking?
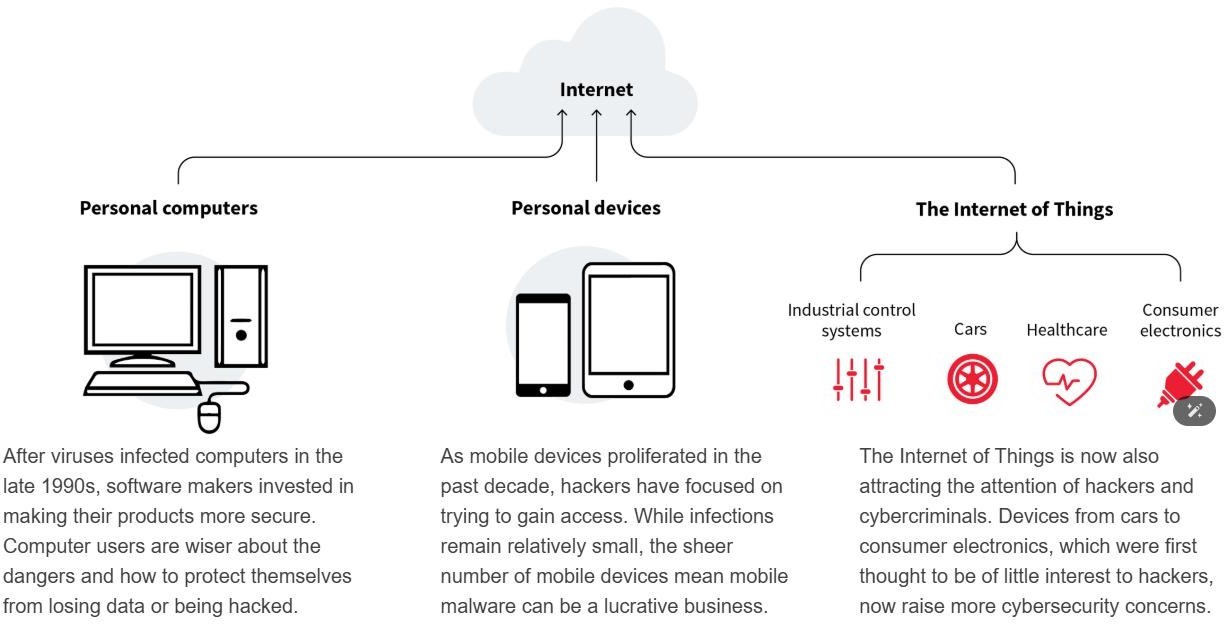
IoT hacking refers to the unauthorized access or manipulation of internet-connected devices, ranging from simple household items like smart thermostats to complex systems in industrial or healthcare sectors. These devices are often vulnerable due to weak security features, making them attractive targets for cybercriminals. Attackers may exploit vulnerabilities like default passwords or unpatched software to compromise devices. IoT encompasses a wide range of connected objects, from household appliances to industrial sensors, and as the number of devices increases, so does the risk. Poor security practices contribute to these devices being hijacked, sometimes forming botnets for malicious use.
Three Basic Components
The Internet of Things (IoT) is composed of three basic components that work together to enable connected devices to collect, share, and process data. These components are sensing technology, IoT gateways, and the cloud. Let’s explore each of these in detail:
- Sensing Technology
Sensing technology refers to the devices and sensors that collect data from the physical environment. These sensors are the “eyes and ears” of the IoT system. They detect and measure specific physical parameters and convert them into digital data that can be transmitted to other devices for processing.
Key Aspects of Sensing Technology:
Types of Sensors: There are various types of sensors used in IoT, depending on the application. Some common examples include:
- Temperature Sensors: Used in smart homes for climate control or in industrial settings to monitor machinery temperatures.
- Proximity Sensors: Used for detecting the presence of objects or people, often used in security systems.
- Motion Sensors: Common in security applications and smart lighting
- Pressure Sensors: Used in industrial applications, like monitoring pressure in pipes or tanks.
- Humidity Sensors: Used in agriculture and weather
- Light Sensors: Used in smart lighting systems for automatic adjustment of
- Data Collection: Sensors collect real-time data from the environment, such as temperature, motion, location, humidity, etc.
- Edge Processing: In some cases, sensors are equipped with small processors to perform basic computations locally before sending data to other parts of the
These sensors are integral to IoT, as they gather the data that drives insights and decision-making.
2. IoT Gateways
An IoT gateway acts as an intermediary between the IoT devices (like sensors) and the cloud or other systems. It is a device or software that connects the local IoT devices to the internet, enabling data transmission from the edge (sensing technology) to the cloud or other remote processing systems. It performs several essential functions to make IoT networks more efficient, secure, and scalable.
Key Functions of IoT Gateways:
- Data Aggregation and Filtering: IoT gateways aggregate data from multiple IoT devices or sensors, filtering out unnecessary or redundant information before transmission. This reduces bandwidth usage and ensures only relevant data is sent to the cloud or server.
- Protocol Conversion: IoT devices use a variety of communication protocols (e.g., Zigbee, Bluetooth, Wi-Fi, ). IoT gateways often convert these protocols to make data communication more seamless and standardized, allowing devices with different communication standards to interact.
- Edge Computing: Some IoT gateways have local processing capabilities, allowing them to analyze data at the edge rather than sending all data to the cloud. This reduces latency and can make real-time decisions faster, which is essential for time-sensitive applications like industrial control systems.
- Security: Gateways help secure the data transmitted from the IoT devices to the cloud. They can offer encryption, access control, and even firewalls to prevent unauthorized access to the network.
Gateways are crucial because they enable efficient, secure, and seamless communication between the devices and the cloud, and help manage data flow.
3. The Cloud
The cloud is where the vast majority of the data from IoT devices is processed, stored, and analyzed. It refers to the distributed network of servers, data storage, and computational resources that are accessible via the internet. In the context of IoT, the cloud provides the infrastructure and tools for storing massive amounts of data, running analytics, and enabling advanced applications such as machine learning and artificial intelligence.
Key Functions of the Cloud in IoT:
- Data Storage: The cloud provides virtually limitless storage for the large amounts of data generated by IoT This can include sensor readings, device statuses, and user-generated data.
- Data Processing and Analysis: The cloud performs heavy computation, data processing, and For instance, it can run algorithms to derive insights, detect anomalies, or predict future trends based on the data received from IoT devices.
- Real-time Monitoring: Many IoT applications, such as smart homes or industrial systems, rely on the cloud for real-time monitoring and alerts. The cloud enables users to view and interact with the data collected from IoT devices through web- based dashboards or mobile applications.
- Data Integration: The cloud can integrate data from multiple IoT devices, systems, and This allows businesses or users to access a unified view of all their connected devices and systems, regardless of the manufacturer or platform.
- Scalability: The cloud offers immense scalability, meaning as the number of IoT devices grows, the cloud infrastructure can scale to accommodate the increased data storage and computational demands without requiring physical infrastructure
The cloud is the backbone of most IoT systems, providing the necessary infrastructure for data storage, processing, and analytics.
How These Components Work Together:
- Sensing Technology collects the data from the environment and converts it into a digital format.
- The IoT Gateway processes this data locally, filters it, and sends it to the
- In the Cloud, data is stored, processed, and analyzed, providing insights, monitoring, and control of the IoT devices.
The three basic components of IoT –Sensing Technology, IoT Gateways, and The Cloud – work in tandem to enable the collection, transmission, and analysis of data. Together, they form the backbone of the vast network of connected devices that power the Internet of Things.
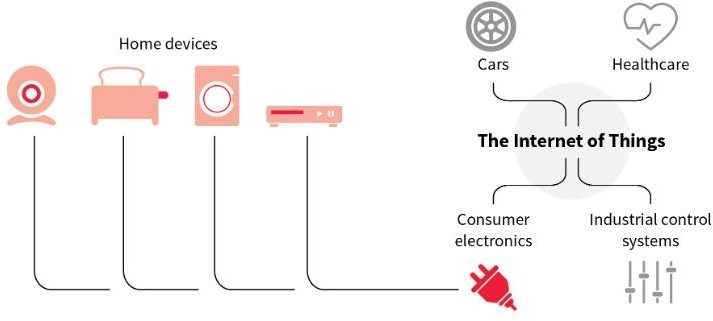
Security flaws
Hackers exploit the weak security and 24-hour connectivity of the consumer devices, like toasters, washers and webcams, to recruit them into botnets, which are used to launch attacks on other targets. While the devices themselves have only limited
computing power and memory, they can still be harnessed together to create a formidable army of robot devices.
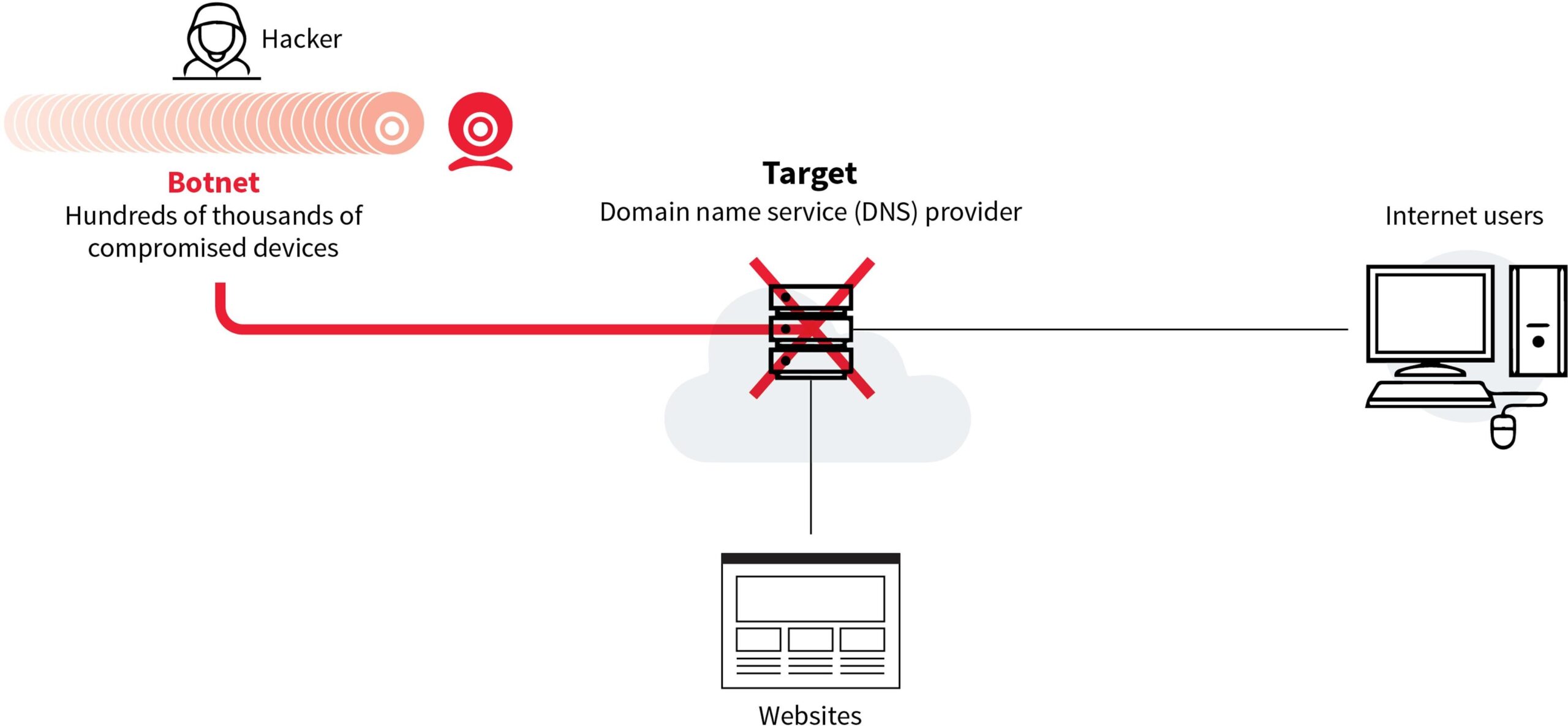
Launching a DDoS attack
Hackers do this by automatically scanning the internet for devices protected by default or easily crackable passwords which they can recruit to their botnet. The hacker can then leverage the botnet to launch attacks on other devices, in what is called a distributed denial of service attack, or DDoS, which attempts to knock a website offline by flooding its DNS provider with traffic.
Why hackers target IoT devices
Hackers have various objectives when targeting IoT devices:
1.Data Theft
Many IoT devices collect sensitive personal or organizational data, such as location, health information, or usage patterns. Hackers can steal this data for:
- Identity Theft: Using stolen personal information to commit
- Corporate Espionage: Gaining access to proprietary business data, such as confidential communications or research.
- Dark Web Sales: Selling stolen data to other criminals on the dark
2. Surveillance and Spying
Devices equipped with cameras or microphones, such as smart security systems, can be compromised to:
- Monitor individuals or organizations: Hackers may hijack these devices to covertly observe activities, gather intelligence, or even blackmail individuals by collecting private information or footage.
3. Creating Botnets
Compromised IoT devices are often used in large-scale cyberattacks:
- Botnet Formation: A botnet is a network of infected devices that hackers can control remotely to carry out malicious activities.
- DDoS Attacks: IoT devices are often used in Distributed Denial of Service (DDoS) attacks, where the botnet overwhelms a target server, website, or service with traffic, causing it to crash.
4. Resource Hijacking
Hackers can repurpose IoT devices for computational tasks, such as:
- Cryptocurrency Mining: Using compromised IoT devices to mine cryptocurrencies like Bitcoin without the owner’s knowledge, causing the devices to use excessive power and bandwidth.
- Distributed Computing Tasks: Using the device to participate in large-scale distributed tasks (e.g., data processing or cracking passwords).
5. Ransomware and Sabotage
Hackers may use ransomware or malware to disrupt IoT devices:
- Ransomware Attacks: Devices are locked or rendered inoperable until the victim pays a ransom.
- Sabotage in Critical Infrastructure: In industrial settings, attackers can gain control over IoT-enabled systems (e.g., smart grids, healthcare devices) and cause physical damage or operational disruptions.
6. Disrupting Operations
In business or industrial environments, hacking IoT devices can severely impact operations:
- Operational Disruptions: Attackers can compromise devices to halt production, manipulate processes, or even damage equipment, leading to lost productivity, safety risks, or financial losses.
Common Methods of IoT Hacking
As IoT devices become more integrated into everyday life, understanding how they can be compromised is vital. Below are some common hacking methods that target IoT devices:
1. Brute Force Attacks
In brute force attacks, hackers attempt to gain unauthorized access by guessing login credentials through trial and error. This method targets IoT devices that often use weak or default passwords. Automated software makes multiple attempts quickly, exploiting the lack of account lockout policies that typically prevent such attacks.
2. Man-in-the-Middle (MitM) Attacks
MitM attacks occur when hackers intercept and manipulate communications between two devices. Common forms of MitM attacks in IoT include:
- Packet Sniffing: Hackers capture and analyze data packets traveling across unsecured networks.
- IP Spoofing: The attacker impersonates a trusted device to intercept
- Session Hijacking: The attacker steals session cookies to gain unauthorized
MitM attacks are particularly dangerous for IoT devices involved in sensitive applications, like health monitoring systems or security devices.
3. Malware Attacks
Malware attacks involve introducing harmful software (e.g., viruses, worms, ransomware) into IoT devices. Once infected, the device can be:
- Used for data theft.
- Participating in Distributed Denial of Service (DDoS)
- Encrypted with ransomware, demanding payment to restore
Malware can enter through unsecured networks, malicious attachments, or vulnerabilities in device software.
4. Unsecured Network Connections
Many IoT devices rely on unsecured networks, such as unencrypted Wi-Fi connections, which can leave them vulnerable to hacking. Issues include:
- Plaintext Data Transmission: Data transmitted over unsecured networks is often sent without encryption, making it easy for hackers to capture and analyze.
- Outdated Encryption: Some devices use weak or outdated encryption protocols, increasing the likelihood of a successful attack.
- Lack of Network Segregation: If IoT devices are not isolated from more secure parts of the network, they can serve as entry points for hackers to access sensitive data or systems.
5. Communication Methods
IoT devices communicate in various ways, each with its vulnerabilities:
- Device-to-Device Communication: Direct communication between two devices, which can be intercepted if not properly encrypted.
- Device-to-Cloud Communication: Devices sending data directly to the cloud, which can be targeted if cloud security is weak.
- Device-to-Gateway Communication: Devices communicate through a centralized If the gateway is compromised, multiple devices can be affected.
- Back-End Data Sharing: Devices interacting with cloud servers or application servers can expose sensitive data to attacks if proper security measures aren’t in
6. Edge and Fog Computing Vulnerabilities
- Edge Computing involves processing data locally on the device, reducing reliance on cloud However, if these devices are compromised, the attack can spread rapidly.
- Fog Computing pushes data processing closer to the network’s edge, which can increase efficiency but also open up new attack surfaces if local security is
Why IoT Security is Crucial
The variety of IoT devices and their connectivity modes make them attractive targets for hackers. Exploiting the vulnerabilities in these devices, whether through brute force, MitM attacks, or malware, can lead to significant risks such as data breaches, surveillance, botnet creation, and financial loss.
Key IoT Security Measures
- Secure Communication Protocols: Ensuring encryption for data transmitted between devices, gateways, and the cloud.
- Strong Authentication: Using multi-factor authentication (MFA) and strong password policies to defend against brute force attacks.
- Network Segmentation: Isolating IoT devices on separate networks to prevent an attack from spreading to more secure areas.
- Regular Software Updates: Patching vulnerabilities in IoT device firmware and software to prevent malware infections.
- Security Audits: Regularly testing devices and networks for
IoT Technology Protocols Short-Range Wireless:
- Bluetooth Low-Energy (BLE): A power-efficient version of Bluetooth designed for low-energy communication between devices over short distances (up to 100 meters).
- Light-Fidelity (Li-Fi): A wireless communication technology using visible light to transmit data, offering high-speed internet in environments like offices and
- Near Field Communication (NFC): A short-range wireless technology for data exchange over distances of up to 10 cm, commonly used in contactless payments and access control.
- QR Codes & Barcodes: Scannable visual codes that store data, used for product identification and tracking in IoT applications.
- Radio-frequency Identification (RFID): A technology that uses electromagnetic fields to identify and track tags attached to objects, widely used in inventory management and asset tracking.
- Wi-Fi / Direct: A wireless technology used for internet access and peer-to-peer communication between devices without the need for a router.
- Z-Wave: A low-energy, short-range wireless protocol designed for home automation devices like smart thermostats, lights, and locks.
- Zigbee: A wireless standard for IoT, designed for low-power, short-range communication in home automation, smart energy, and healthcare
Medium-Range Wireless:
- Ha-Low: A low-power, wide-area network protocol optimized for IoT applications with low data rates, used in applications like agriculture and smart
- LTE-Advanced: A high-speed wireless communication standard offering enhanced mobile broadband and greater capacity for IoT devices over medium
Long-Range Wireless:
- Low-Power Wide-Area Networking (LPWAN): A protocol designed for long- range, low-power communication between IoT devices, typically used for smart cities and agriculture.
- LoRaWAN: A low-power, wide-area networking protocol used for long-range communication in IoT applications like smart metering and tracking.
- Sigfox: A global network for low-power, wide-area communication, ideal for IoT applications requiring infrequent transmission of small amounts of data.
- Very Small Aperture Terminal (VSAT): Satellite-based communication technology used for providing global IoT connectivity, especially in remote or rural areas.
- Cellular: Mobile network technology (e.g., 4G, 5G) that provides wide-area coverage and supports high-speed data transfer for IoT devices.
Wired Communications:
- Ethernet: A widely used wired networking technology that supports high-speed communication, commonly used for connecting IoT devices in industrial or office
- Power-Line Communication (PLC): A technology that uses existing electrical wiring to transmit data, providing a cost-effective solution for home and building
- Multimedia over Coax Alliance (MoCA): A wired communication standard that uses coaxial cables for high-speed data transfer, often used in home entertainment and smart home networks.
IoT Operating Systems
RIOT OS: An open-source, real-time operating system designed for embedded systems, actuator boards, and sensors. It is energy-efficient, making it ideal for low- power IoT devices.
ARM Mbed OS: A low-power operating system optimized for ARM-based devices, commonly used in wearables and other small, battery-powered IoT devices. It supports connectivity and security features.
RealSense OS X: A specialized operating system by Intel, designed primarily for depth-sensing applications such as cameras and sensors used in robotics and augmented reality (AR) systems.
Nucleus RTOS: A real-time operating system used in industries like aerospace, medical devices, and industrial applications. It offers high reliability and deterministic performance.
Brillo: An Android-based operating system developed by Google for IoT devices like thermostats, smart appliances, and connected home devices. It focuses on ease of integration with cloud services.
Contiki: A lightweight, open-source operating system designed for low-power devices. It is widely used in applications like street lighting and sound monitoring due to its efficient resource usage.
Zephyr: A scalable, open-source RTOS for low-power devices with limited resources. It supports a wide variety of IoT applications and is highly customizable for resource- constrained environments.
Ubuntu Core: A stripped-down version of the Ubuntu OS optimized for IoT devices, particularly in robotics and drones. It is designed for secure, large-scale deployments and uses “snappy” technology for easy updates.
Integrity RTOS: A high-performance, real-time operating system used in safety- critical environments like aerospace, medical, defense, and automotive industries, known for its security and reliability.
Apache Mynewt: An operating system built for Bluetooth Low Energy (BLE) devices. It is suitable for applications such as wearables and connected sensors that require low-power communication.
OWASP Top 10 IoT Vulnerabilities (2014):
- Insecure Web Interface: Issues like weak credentials, account enumeration, and lack of account lockout allow unauthorized access through web interfaces.
- Insufficient Authentication/Authorization: Flaws occur when internal network assumptions fail, leaving interfaces exposed to unauthorized access.
- Insecure Network Services: Devices can be vulnerable to attacks like buffer overflow and DoS if network services are insecure or unnecessary.
- Lack of Transport Encryption/Integrity Verification: Sensitive data is vulnerable when transmitted without encryption or integrity checks.
- Privacy Concerns: Devices collect personal data that may be accessed or shared insecurely, risking user privacy.
- Insecure Cloud Interface: Weak cloud interface credentials allow attackers to easily compromise devices linked to the cloud.
- Insecure Mobile Interface: Mobile interfaces with weak security, such as easy- to-guess credentials, expose devices to attacks.
- Insufficient Security Configurability: Devices with non-modifiable security settings may leave default configurations and passwords vulnerable.
- Insecure Software/Firmware: Devices that cannot be updated or lack update checks remain vulnerable to exploits.
- Poor Physical Security: Due to the nature of IoT devices, physical theft can allow attackers to bypass security.
OWASP Top 10 IoT Vulnerabilities (2018):
- Weak, Guessable, or Hardcoded Passwords: Devices with easily guessable or hardcoded passwords are prone to unauthorized access.
- Insecure Network Services: Exposing unnecessary or insecure services on devices increases the risk of remote control or data compromise.
- Insecure Ecosystem Interfaces: Insecure APIs, cloud, or mobile interfaces allow attackers to compromise device security or related components.
- Lack of Secure Update Mechanism: Devices lacking secure update protocols risk running outdated, vulnerable software.
- Use of Insecure or Outdated Components: Outdated or insecure software components or hardware from untrusted sources can lead to device
- Insufficient Privacy Protection: Devices that improperly handle personal data may lead to privacy breaches.
- Insecure Data Transfer and Storage: Lack of encryption or access control over sensitive data makes it vulnerable during storage, transfer, or processing.
- Lack of Device Management: Devices without robust management features like monitoring, updates, and decommissioning increase long-term risk.
- Insecure Default Settings: Devices shipped with insecure defaults, such as weak passwords, make it easy for attackers to gain control.
- Lack of Physical Hardening: Without physical security measures, attackers can extract sensitive data or take control of devices locally.
Common IoT Attack Areas:
- Device Memory Containing Credentials: Storing unprotected credentials in device memory increases the risk of credential theft.
- Device/Ecosystem Access Control: Flawed access controls can let unauthorized users manipulate device behavior or data.
- Device Physical Interfaces/Firmware Extraction: Attackers may extract firmware or gain access through physical interfaces.
- Device Web Interface: Vulnerabilities in the web interface can allow attackers to take control of the device remotely.
- Device Firmware: Insecure firmware can be exploited, especially if it’s outdated or not signed properly.
- Device Network Services: Weaknesses in network services can make the device vulnerable to network-based attacks.
- Devices Administrative Interface(s): Improper configuration or exposure of the admin interface can give attackers full control.
- Unencrypted Local Data Storage: Devices storing sensitive data in unencrypted form are vulnerable to physical theft or data leaks.
- Cloud Interface(s): Cloud interfaces with weak security allow attackers to compromise devices connected to the cloud.
- Device Update Mechanism(s): Unsecured update mechanisms can let attackers deliver malicious updates to the device.
- Insecure APIs (Vendor & Third-party): Vulnerable APIs can expose devices and their ecosystems to compromise.
- Mobile Application: Weak security in the mobile app interface can allow attackers to interact with devices maliciously.
- Confidentiality and Integrity Issues: Insufficient security measures can lead to confidentiality breaches or unauthorized data modifications.
- Network Traffic: Unencrypted or poorly secured network traffic can be intercepted or manipulated.
IoT Threats:
- DDoS Attack: IoT devices can be used in Distributed Denial of Service (DDoS) attacks, overwhelming services with traffic.
- HVAC System Attacks: Cyberattacks on HVAC systems can disrupt operations and cause damage or data theft.
- Rolling Code Attack: Attackers intercept and reuse codes to steal vehicles by exploiting weaknesses in key fob systems.
- BlueBorne Attack: Bluetooth-based attacks exploit vulnerabilities in devices with Bluetooth capabilities.
- Jamming Attack: Attackers block communication signals between IoT devices, disrupting their functionality.
- Remote Access via Backdoors: Devices with backdoors can be remotely accessed by attackers to take control.
- Remote Access via Unsecured Protocols: Protocols like TELNET can allow attackers to access devices remotely without secure authentication.
- Sybil Attack: Attackers impersonate multiple devices or users to create fake traffic or manipulate system behaviors.
- Rootkits/Exploit Kits: Attackers use these tools to gain control over IoT devices, often avoiding detection.
- Ransomware: Malicious software locks IoT systems and demands payment for
IoT Hacking Methodology:
- Information Gathering: This step involves collecting data about the target devices using tools like Shodan or Google.
- Vulnerability Scanning: Scanning for vulnerabilities in devices using tools like Nmap or vulnerability scanners like RIoT.
- Launching Attacks: Exploiting vulnerabilities using tools such as RFCrack or HackRF to gain control of devices.
- Gaining Access: Once vulnerabilities are identified, attackers use them to gain unauthorized access.
- Maintaining Access: Attackers establish persistence on the device to maintain control over time.
Countermeasures to Secure IoT Devices:
- Firmware Updates: Regularly updating device firmware reduces the risk of known exploits.
- Block All Unnecessary Ports: Disable unused ports to reduce the attack surface of devices.
- Disable Insecure Access Protocols: Turning off insecure protocols like TELNET prevents unauthorized access.
- Only Use Encrypted Communication Protocols: Ensuring all communications are encrypted helps protect sensitive data.
- Use Strong Passwords: Strong, complex passwords mitigate the risk of unauthorized access.
- Encrypt All Data: Protecting data at rest, in transit, and during processing ensures confidentiality.
- Use Account Lockout: Account lockout mechanisms prevent brute-force attacks on login interfaces.
- Configuration Management: Regularly monitoring device configurations ensures compliance with security standards.
- Use Multi-factor Authentication: Adding an extra layer of security reduces the chances of unauthorized access.
- Disable UPnP: Disabling Universal Plug and Play (UPnP) prevents automatic exposure of services to external networks.
IoT Hacking involves unauthorized access to IoT devices, often due to weak security measures like default passwords and outdated software. Attackers exploit vulnerabilities for data theft, surveillance, botnets, resource hijacking, and disruption.
Key IoT Components:
- Sensing Technology – Devices/sensors collecting
- IoT Gateways – Bridge between devices and the
- The Cloud – For data storage and
Common Threats: Brute force, malware, and man-in-the-middle attacks.
Security Measures: Strong authentication, secure protocols, regular updates, network segmentation, and audits.
- With IoT’s growth, understanding risks and adopting robust security practices is essential to protect sensitive data and ensure operational safety.




