Meritshot Tutorials
- Home
- »
- Hacking Web Servers in Cyber Security
Cyber Security Tutorial
-
What is cybersecurity?What is cybersecurity?
-
Introduction to LinuxIntroduction to Linux
-
Text Processing using GREP, SED, and AWKText Processing using GREP, SED, and AWK
-
Introduction to Ethical HackingIntroduction to Ethical Hacking
-
Footprinting and ReconnaissanceFootprinting and Reconnaissance
-
Scanning NetworksScanning Networks
-
Enumeration in Cyber SecurityEnumeration in Cyber Security
-
Vulnerability AnalysisVulnerability Analysis
-
System HackingSystem Hacking
-
Malware ThreatsMalware Threats
-
SniffingSniffing
-
Social EngineeringSocial Engineering
-
Denial-of-ServiceDenial-of-Service
-
Evading IDS, Firewalls, and HoneypotsEvading IDS, Firewalls, and Honeypots
-
Hacking Web ServersHacking Web Servers
-
Hacking Web ApplicationsHacking Web Applications
-
SQL InjectionSQL Injection
-
Hacking Wireless NetworksHacking Wireless Networks
-
Hacking Web ApplicationsHacking Web Applications
-
Hacking Mobile PlatformsHacking Mobile Platforms
-
IoT HackingIoT Hacking
-
Cloud ComputingCloud Computing
-
CryptographyCryptography
Hacking Web Servers
What is a Web Server?
A web server is a system, either software or hardware, that serves content and services over the internet. It enables users to access websites or applications by handling requests from web browsers or other clients and responding with the appropriate resources.
Web servers use protocols like HTTP (Hypertext Transfer Protocol) or its secure counterpart HTTPS to facilitate communication between clients (such as web browsers) and the server. When you type a website’s address into your browser, the web server processes your request, retrieves the necessary files (e.g., HTML, CSS, JavaScript), and sends them back to your browser to display the webpage.
Functions:
Store and Deliver Content:
- Web servers store website files like HTML, CSS, JavaScript, images, and
- They deliver these files to users’ browsers when
Process Requests:
- When a user enters a website URL, the web server:
- Resolves the domain name into an IP
- Locates the requested
- Processes server-side operations (if required, g., retrieving data from a database).
- Sends the resource back to the user’s
Enable Web Applications:
- Besides static websites, web servers can host dynamic applications, interacting with databases and APIs to provide functionality like login, search, and e-
Key Concepts of Web Servers
Document Root: This is the main directory on the server from which web files are served. It contains all the files that can be accessed via the web, such as HTML, CSS, JavaScript, images, and multimedia files.
Example:
- /var/www/html (Linux/Apache)
- C:\inetpub\wwwroot (Windows/IIS)
Purpose: Files in the document root can be accessed by users through their browsers.
Server Root: This directory contains all the server’s configuration files, executable files, and logs. It is distinct from the document root and is not accessible via the web.
- Important: Unlike the document root, this directory is NOT exposed to the web. It ensures the security of sensitive files.
Virtual Document Tree: This is a structure that allows the server to serve files from different locations, especially when the original storage becomes full. It can be set up on different disks or even different machines.
Used when:
- Original storage is
- Files are distributed across different
Virtual Hosting: This technique allows multiple websites to be hosted on a single server. Each site can have its own domain name and configuration, making efficient use of server resources.
Types:
- Name-based Virtual Hosting: Differentiates websites by domain name (e.g., site1.com and www.site2.com).
- IP-based Virtual Hosting: Assigns different IP addresses for each
Example: A single server hosting both blog.com and shop.com. Types of Web Servers
Open-source Web Server Architecture: The most common setup is the LAMP stack, which includes:
Linux: The operating system.
Apache: The web server software.
MySQL: The database management system.
PHP: The programming language used for server-side scripting.
Internet Information Services (IIS):
- Developed by Microsoft for Windows-based
Features:
- Supports protocols like HTTP, HTTPS, FTP,
- Integrates seamlessly with other Microsoft
Web Server Hacking Methodology
- Information Gathering
Information gathering is the first step in web server hacking, where the attacker collects as much information as possible about the target.
Robots.txt: This file, located in the root directory of a website, instructs search engine crawlers about which pages should not be indexed. By analyzing this file, attackers can discover hidden directories or files that may be vulnerable.
Internet Searches & WHOIS: Using search engines to find information about the target domain and WHOIS databases to gather registration details can provide insights into the organization and its infrastructure.
Testing HTTP Methods: Attackers can check which HTTP methods are enabled on the server (such as GET, POST, DELETE, etc.) to identify potential vulnerabilities. Some methods, like DELETE and PUT, can be risky if not properly secured.
- Tools like Nmap scan for enabled methods (e.g., GET, POST, DELETE).
Dangerous methods:
- PUT: Allows file uploads, potentially malicious
- DELETE: Allows file
Example Command:
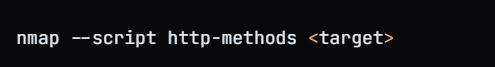
This command uses Nmap to scan the target server for supported HTTP methods.
1. Footprinting
Footprinting is a more detailed phase of information gathering, where attackers identify specific details about the web server.
Email Enumeration: Attackers may use scripts (like Nmap) to list email addresses associated with the target domain, which can be useful for phishing attacks or social engineering.
Web Application Enumeration: Tools can be used to identify common web applications running on the server (e.g., WordPress, Joomla, etc.), allowing attackers to look for known vulnerabilities.
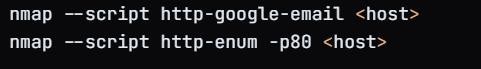
These commands help to enumerate email addresses and common web applications, respectively.
1. Website Mirroring
Website mirroring involves creating a local copy of a website to analyze its structure and content offline. This can help in understanding the layout, identifying vulnerabilities, or finding sensitive information.
Purpose: Create a local copy of the target website for offline analysis.
Tools for Mirroring:
Wget: A command-line utility that retrieves content from web servers.
HTTrack: A popular offline browser utility that allows users to download an entire website.
BlackWidow: A website downloading tool that also provides features for analyzing the structure of the site.
2. Vulnerability Scanning
Vulnerability scanning is the process of identifying security weaknesses in a web server.
Nikto: A web server scanner that focuses on identifying misconfigurations, outdated software, and known vulnerabilities. It is known for being noisy, meaning it can easily be detected by intrusion detection systems (IDS).
Metasploit: A penetration testing framework that can be used to find, exploit, and validate vulnerabilities. It has a large database of exploits and can automate many aspects of the testing process.
3. Session Hijacking & Password Cracking
Session Hijacking: This technique involves taking control of a user’s active session with a web application. Attackers can exploit vulnerabilities in the application or use
techniques like packet sniffing to capture session tokens. Once they have the session token, they can impersonate the user and gain unauthorized access.
Password Cracking: This involves using various methods to guess or recover passwords for web services. Tools like THC Hydra and Brutus can automate the process of trying multiple password combinations against a target service, such as FTP, HTTP, or SSH.
Common Web Server Attacks
- Denial of Service (DoS) and Distributed Denial of Service (DDoS)
DoS: A DoS attack aims to make a service unavailable by overwhelming it with traffic. This can be achieved by sending a flood of requests that the server cannot handle, leading to downtime.
DDoS: A DDoS attack is similar but involves multiple compromised systems (often part of a botnet) sending requests to the target server simultaneously, making it even harder to mitigate.
2. DNS Server Hijacking
This attack involves compromising a DNS server to redirect traffic from legitimate websites to malicious ones. Attackers can manipulate DNS records to point users to fake sites, often for phishing purposes. Countermeasures include implementing DNSSEC (Domain Name System Security Extensions) and using secure DNS servers.
3. Directory Traversal Attacks
Directory traversal attacks exploit vulnerabilities in web applications to access files and directories that are outside the web root folder. By manipulating the URL, attackers can gain access to sensitive files, such as configuration files or user data.
4. Man-in-the-Middle (MITM) Attacks
In a MITM attack, the attacker intercepts communication between the user and the web server. This can be done by tricking the user into connecting to a malicious proxy or by exploiting vulnerabilities in the network. The attacker can then eavesdrop on the communication or alter the data being transmitted.
5. Phishing Attacks
Phishing involves tricking users into providing sensitive information by masquerading as a trustworthy entity. Attackers often create fake websites that look legitimate to capture login credentials or personal information.
6. Website Defacement
Website defacement is the act of altering the visual appearance of a website, often to display a message or propaganda. This can be achieved through various means, including exploiting vulnerabilities in the web application or server.
7. Web Server Misconfiguration
Misconfigurations can lead to vulnerabilities that attackers can exploit. Common issues include default passwords, unnecessary services running, and improper permissions on files and directories. Regular audits and adherence to security best practices can help mitigate these risks.
8. HTTP Response Splitting
This attack occurs when an application includes user input in HTTP response headers without proper validation. Attackers can inject malicious data, leading to various attacks such as XSS (Cross-Site Scripting) or cache poisoning.
9. Web Cache Poisoning
Web cache poisoning involves injecting malicious content into a web cache, which is then served to users. This can be done through HTTP response splitting or by exploiting caching mechanisms in web applications.
10. SSH Brute Force Attacks
SSH brute force attacks involve attempting to gain unauthorized access to SSH servers by guessing login credentials. Attackers can use tools like Hydra or custom scripts to automate the process of trying multiple username and password combinations.
Web Server Security Best Practices:
Regular Maintenance
Patch and Update: Regularly update the web server software and apply security patches to protect against known vulnerabilities. This includes the operating system, web server software, and any applications running on the server.
Encrypt Traffic: Use HTTPS to encrypt data transmitted between the client and server, protecting against eavesdropping and man-in-the-middle attacks.
Security Policies
Access Control: Implement strict access controls to limit who can access sensitive areas of the web server. Use role-based access control (RBAC) to ensure users have only the permissions they need.
Log Monitoring: Regularly monitor server logs for unusual activity, such as failed login attempts or unexpected changes to files. Implement alerting mechanisms to notify administrators of potential security incidents.
Network Security
DMZ Architecture: Place web servers in a Demilitarized Zone (DMZ) to isolate them from the internal network. This adds an additional layer of security, as attackers would need to breach the DMZ to access internal resources.
Firewalls: Use firewalls to filter incoming and outgoing traffic. Configure rules to allow only necessary traffic and block potentially harmful requests.
Configuration Management
Secure Default Configurations: Change default passwords and disable unused accounts and services. Ensure that only necessary services are running on the server to minimize potential attack vectors.
Audit Ports: Regularly audit open ports on the server and disable any that are unnecessary. This reduces the number of entry points available to attackers.
Use of Certificates
SSL/TLS Certificates: Ensure that SSL/TLS certificates are valid, properly configured, and regularly updated. This helps to secure communications and build trust with users.
Understanding web servers, their architecture, and the various methodologies for hacking and securing them is crucial for both attackers and defenders. By implementing best practices in security and regularly updating systems, organizations can significantly reduce their risk of falling victim to web server attacks. Continuous education and awareness of emerging threats are essential in maintaining a robust security posture. ## Understanding Web Servers
Quick Summary of Web Servers and Hacking Definition:
A system that stores and delivers web pages via HTTP.
Functions:
- Store Content: Holds files like HTML, CSS, and
- Process Requests: Resolves domain names and serves
- Host Applications: Supports dynamic web applications interacting with
Key Concepts
Document Root:
Main directory for web files (e.g., /var/www/html).
Server Root:
Contains configuration and log files; not web-accessible.
Virtual Hosting:
Multiple sites on one server, either:
- Name-Based: Differentiates websites by domain
- IP-Based: Uses unique IP addresses for each
Types of Web Servers LAMP Stack:
- Linux, Apache, MySQL,
IIS:
- Microsoft’s web server for
Web Server Hacking Methodology Information Gathering:
Tools:
- txt: Discover restricted directories.
- WHOIS: Collect domain ownership
- HTTP Methods Testing: Test with tools like
Footprinting:
- Email Enumeration: Gather target emails for phishing or
- Application Identification: Detect applications and services with tools like
Website Mirroring:
Clone websites for offline analysis using tools like:
Ø Wget
- HTTrack Vulnerability Scanning: Use tools such as:
- Nikto: Identify web server
- Metasploit: Exploit identified
Session Hijacking & Password Cracking:
- Session Hijacking: Steal session
- Password Cracking: Use brute-force tools to guess
Common Web Server Attacks
- DoS/DDoS: Overload the server with
- DNS Hijacking: Redirect users to malicious
- Directory Traversal: Access restricted files by manipulating
- MITM Attacks: Intercept communication between users and
- Phishing: Trick users into providing sensitive
- Website Defacement: Alter the appearance of a
- Misconfiguration: Exploit weak or default server
- HTTP Response Splitting: Inject malicious data into HTTP
- Web Cache Poisoning: Serve malicious cached
- SSH Brute Force: Guess SSH credentials using brute-force
Security Best Practices:
Maintenance:
- Apply regular
- Use HTTPS for secure
Policies:
- Implement access
- Monitor logs for suspicious
Network Security:
- Use a DMZ to isolate
- Configure firewalls to block unnecessary
Configuration Management:
- Use secure
- Audit and close unused
Certificates:
- Ensure SSL/TLS certificates are valid and up-to-




