Meritshot Tutorials
- Home
- »
- Hacking Mobile Platforms in Cyber Security
Cyber Security Tutorial
-
What is cybersecurity?What is cybersecurity?
-
Introduction to LinuxIntroduction to Linux
-
Text Processing using GREP, SED, and AWKText Processing using GREP, SED, and AWK
-
Introduction to Ethical HackingIntroduction to Ethical Hacking
-
Footprinting and ReconnaissanceFootprinting and Reconnaissance
-
Scanning NetworksScanning Networks
-
Enumeration in Cyber SecurityEnumeration in Cyber Security
-
Vulnerability AnalysisVulnerability Analysis
-
System HackingSystem Hacking
-
Malware ThreatsMalware Threats
-
SniffingSniffing
-
Social EngineeringSocial Engineering
-
Denial-of-ServiceDenial-of-Service
-
Evading IDS, Firewalls, and HoneypotsEvading IDS, Firewalls, and Honeypots
-
Hacking Web ServersHacking Web Servers
-
Hacking Web ApplicationsHacking Web Applications
-
SQL InjectionSQL Injection
-
Hacking Wireless NetworksHacking Wireless Networks
-
Hacking Web ApplicationsHacking Web Applications
-
Hacking Mobile PlatformsHacking Mobile Platforms
-
IoT HackingIoT Hacking
-
Cloud ComputingCloud Computing
-
CryptographyCryptography
Hacking Mobile Platforms
Hacking Mobile Platforms
Hacking mobile platforms involves exploiting vulnerabilities in mobile operating systems, applications, and devices to gain unauthorized access, disrupt services, or extract sensitive information. This is a critical area in cybersecurity due to the increasing reliance on mobile devices for personal and business operations. Below is an overview of key concepts, methods, tools, and mitigation strategies related to hacking mobile platforms.
Three Main Avenues of Attack Device Attacks
- Browser-based: Exploiting vulnerabilities in mobile
- SMS-based: Smishing, malicious
- Application-based: Malicious apps or excessive
- Rooted/Jailbroken Devices: Exploiting enhanced
Network Attacks
- DNS Cache Poisoning: Redirecting users to malicious
- Rogue Access Points (APs): Intercepting data on fake Wi-Fi
- Packet Sniffing: Capturing sensitive information in
Data Center (Cloud) Attacks
- Compromising databases, cloud-stored files, and
OWASP Top 10 Mobile Risks:
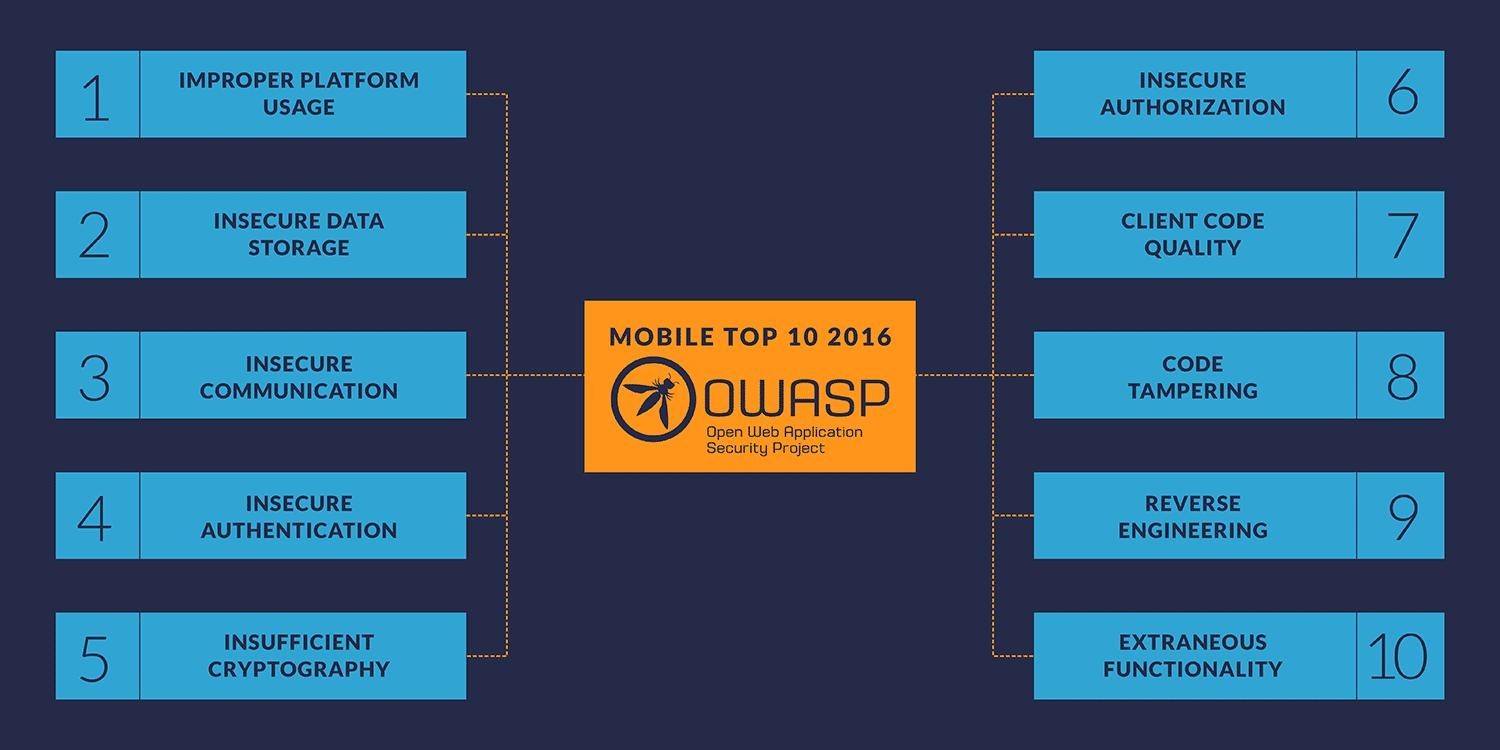
- Improper Platform Usage – Misuse of features or security controls (Android intents, TouchID, Keychain).
- Insecure Data Storage – Improperly stored data and data
- Insecure Communication – Poor handshaking, incorrect SSL, clear-text communication.
- Insecure Authentication – Authenticating end user or bad session management.
- Insufficient Cryptography – Code that applies cryptography to an asset, but is insufficient (does NOT include SSL/TLS).
- Insecure Authorization – Failures in authorization (access rights).
- Client Code Quality – Catchall for code-level implementation
- Code Tampering – Binary patching, resource modification, dynamic memory modification.
- Reverse Engineering – Reversing core binaries to find problems and
- Extraneous Functionality – Catchall for backdoors that were inadvertently placed by coders.
Mobile Platforms
1. Android
Android is an open-source operating system developed by Google, widely used in smartphones, tablets, and IoT devices. Its flexibility allows users to modify the system but also opens the door to potential security risks.
l Rooting:
- Rooting is the process of gaining “superuser” or administrative access to an Android device.
- With root access, users can bypass system restrictions, customize the OS, install apps requiring advanced privileges, or even replace the stock ROM with a custom
- Risks: Rooting voids warranties, weakens security, and makes the device susceptible to malware and hacking.
Popular Rooting Tools:
- KingoRoot: A user-friendly, one-click rooting
- TunesGo: A phone management app with rooting
- OneClickRoot: Simplifies the rooting process with minimal user
- MTK Droid: Designed for devices with MediaTek processors to provide root access and backups.
iOS
iOS is Apple’s proprietary operating system known for its high security and tightly controlled ecosystem. While secure by default, users often jailbreak iOS to bypass restrictions.
Jailbreaking:
- Jailbreaking removes Apple’s software restrictions, enabling users to install unauthorized apps, customize the interface, or access system files.
- It allows flexibility but compromises security, making the device vulnerable to
Levels of Jailbreaking:
- Untethered: The jailbreak remains functional even after the device is No additional actions are needed to reapply the patches.
- Semi-Tethered: After a reboot, jailbreak features are disabled until the user re- enables them with software installed on the device.
- Tethered: Every reboot removes the jailbreak, requiring a connection to a computer to restore Without this, the device may enter a “boot loop.”
Popular Jailbreaking Tools:
- evasi0n7 and Pangu: Support untethered jailbreaks for specific iOS
- Redsn0w: A classic tool for older versions of
- Absinthe: Known for its simplicity in performing untethered
- Cydia: A package manager used to install apps and tweaks on jailbroken
Exploitation Techniques:
- Userland Exploit: Exploits vulnerabilities in the operating system itself. Provides root access but not administrative These can be easily patched by Apple.
- iBoot Exploit: Targets the bootloader (iBoot) to disable code signing, enabling semi-tethered jailbreaks. This type of exploit can be patched by Apple through
- BootROM Exploit: Targets the first bootloader in hardware, making it unpatchable via software This provides deep access to the file system and system operations.
Threats to Mobile Devices
App Store Attacks:
- App stores, especially third-party ones, often lack stringent security measures, enabling malicious apps to bypass detection.
- These apps can:
- Steal sensitive
- Spy on
- Install backdoors for future
Phishing Attacks:
- Mobile devices are frequently used for communication, making them prime targets for phishing.
- Attackers exploit:
- Fake apps mimicking legitimate
- Malicious links sent via SMS or
- Impersonation of trusted entities to trick users into revealing
Device Administration & Management Android Device Administration API:
- Provides APIs for apps to implement security measures like password enforcement, remote wiping, and device encryption.
- Commonly used in enterprise environments to manage employee devices
Bring Your Own Device (BYOD):
- A policy where employees use personal devices for While convenient, BYOD poses significant security risks:
- Personal devices often lack corporate-level security
- Data leakage can occur if a device is lost or
- Organizations cannot fully enforce security policies on personal
Mobile Device Management (MDM):
- MDM solutions help enterprises secure and manage devices
- Features include:
- Enforcing security policies (e.g., strong passwords, encryption).
- Deploying and managing
- Remote wiping of lost or stolen
Popular MDM Solutions:
- XenMobile: Offers endpoint management for mobile and desktop
- IBM MaaS360: Includes advanced threat management and application
- AirWatch: VMware’s MDM solution for
- MobiControl: A solution focusing on remote control and
Bluetooth Security Bluetooth Attacks:
- Bluetooth vulnerabilities can allow attackers to gain unauthorized access to a device. Common attack types include:
- Bluejacking: Sending unsolicited messages to nearby Bluetooth
- Bluesnarfing: Accessing and stealing data from a device without the user’s
- Bluebugging: Exploiting a vulnerability to gain control of the
Modes of Bluetooth Operation:
Discovery Mode: How the device responds to inquiries:
- Discoverable: Fully visible to other devices and responds to all connection
- Limited Discoverable: Restricts visibility to certain devices or for a limited
- Nondiscoverable: Ignores all inquiries, making the device
- Pairing Mode: How the device handles pairing requests:
- Pairable: Accepts all requests, which can be
- Nonpairable: Rejects all pairing requests, enhancing
Mobile Attacks
Mobile devices are susceptible to a wide range of attacks, many of which are adaptations of traditional cybersecurity threats seen on desktops. The unique features of mobile platforms, such as reliance on SMS, Bluetooth, NFC, and mobile-specific apps, provide additional attack vectors. Key concerns include vulnerabilities in
communication protocols, excessive permissions granted to apps, and user behaviors such as clicking on malicious links in texts or emails.
Common Mobile Attack Types
Session Hijacking:
- Exploiting insecure session cookies to take over a user’s
- Mobile apps often maintain persistent sessions, making them prime
Browser Vulnerabilities:
- Mobile browsers can be exploited through unpatched vulnerabilities or malicious
- Includes attacks like Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF).
Excessive Permissions:
- Mobile apps may request unnecessary permissions, leading to potential misuse, such as accessing sensitive data or tracking user behavior.
OS/App Bugs:
- Mobile operating systems and apps may contain vulnerabilities that attackers can exploit to gain unauthorized access or control.
Mobile-Specific Attacks SMS Phishing (Smishing)
- Smishing involves sending fake SMS messages with malicious links or
l Why it works:
- SMS messages are often perceived as more trustworthy because they are less frequent than emails.
- Shortened URLs in texts make it harder for users to identify malicious
Trojan Applications
- Trojans disguise themselves as legitimate apps to trick users into installing Once installed, they can steal data, monitor activities, or take control of the device.
- Common Trojan examples:
- Obad: Exploits Android vulnerabilities to execute commands or install additional
- Fakedefender: Pretends to be an antivirus app, locks the device, and demands payment for unlocking.
- TRAMPS: Monitors user activities and exfiltrates sensitive
- ZitMo (Zeus-in-the-Mobile): Intercepts SMS messages, often targeting two- factor authentication codes.
Spyware
- Spyware is software that secretly monitors and records user It is often used for malicious purposes like stealing credentials or eavesdropping.
- Common spyware tools:
- Mobile Spy: Logs calls, SMS messages, and GPS
- Spyera: Tracks activities, records conversations, and even enables remote camera
Mobile Tracking Features
- Features like Find My iPhone and Android device tracking are intended to help users locate lost devices. However, these features can be exploited to locate or surveil individuals.
- Attackers use stolen credentials or phishing tactics to access these tracking
Mobile Attack Platforms
Mobile attack platforms are tools that allow attackers to perform network reconnaissance, spoofing, or attacks directly from their phones. Common tools include:
Network Spoofer:
- Used for network-based attacks like spoofing or man-in-the-middle
- Attackers manipulate network traffic to redirect users or steal
DroidSheep:
- Focuses on session hijacking by sniffing unencrypted session
- Particularly effective on unsecured Wi-Fi
Nmap:
- A versatile network scanner that helps attackers identify vulnerable devices or services on a network.
- Available as a mobile version (e.g., Nmap for Android).
Bluetooth Attacks
Bluetooth provides a convenient way for devices to connect wirelessly, but it also opens the door to several vulnerabilities. The following are common Bluetooth-based attacks:
Types of Bluetooth Attacks Bluesmacking:
- A Denial of Service (DoS) attack targeting Bluetooth devices, causing them to crash or become unresponsive.
- Exploits Bluetooth protocol vulnerabilities to overwhelm
Bluejacking:
- Sending unsolicited messages to Bluetooth-enabled devices within
- Generally harmless but can be used for phishing or spreading
Bluesniffing:
- Attempts to discover Bluetooth-enabled devices and identify their
- Can lead to further exploitation like
Bluebugging:
- Gaining remote control of a Bluetooth device to exploit its
- Attackers can send texts, make calls, or even listen to
Bluesnarfing:
- Stealing data (e.g., contacts, messages, files) from a device via Bluetooth without the user’s consent.
- Exploits poorly secured or misconfigured
Blueprinting:
- Gathering detailed information about a Bluetooth device, such as its make, model, and firmware version.
- Helps attackers identify potential vulnerabilities for
Bluetooth Attack Tools BlueScanner:
- Scans for Bluetooth devices in the
- Provides basic information about discoverable
BT Browser:
- Enumerates detailed information about Bluetooth devices, such as supported
Bluesniff and btCrawler:
- Sniffing tools with graphical interfaces for finding devices and their
Bloover:
- Focuses on performing Bluebugging
- Can take control of vulnerable devices
PhoneSnoop:
- Spyware specifically designed for BlackBerry
- Allows attackers to eavesdrop on calls and monitor user
Super Bluetooth Hack:
- A multifunctional tool that combines capabilities like Bluesnarfing, Bluebugging, and data theft.
- Requires physical proximity but is a potent all-in-one
General Mobile Security Concerns
Vulnerabilities in Wireless Connections Wi-Fi:
- Unsecured or poorly secured networks can be exploited for eavesdropping or man-in-the-middle (MITM) attacks.
- Rogue access points mimic legitimate networks to steal user
NFC (Near-Field Communication):
- Can be exploited to steal sensitive data from devices in close
- Often targeted in contactless payment
Encryption:
- Weak or improperly implemented encryption protocols can expose sensitive data to attackers.
- This includes data stored on the device and data transmitted over
Improving Mobile Security
To mitigate mobile device threats, users and organizations must adopt proactive strategies and security practices. Here’s a detailed explanation of the methods:
1. Keep Operating Systems and Apps Up to Date Why It Matters:
- Regular updates patch vulnerabilities in the operating system (OS) and
- Updates include security fixes for newly discovered
Best Practices:
- Enable automatic updates for the OS and apps to ensure devices are always running the latest versions.
- Monitor critical security advisories for urgent
2. Implement Screen Locks and Strong Passwords Why It Matters:
- Prevents unauthorized access to the device if it is lost or
- Protects sensitive information stored on the
Best Practices:
- Use complex passwords or PINs (e.g., at least 6 digits).
- Enable biometric authentication (e.g., fingerprint, Face ID) as an additional
- Configure the device to lock automatically after a short period of
3. Secure Wireless Communication Why It Matters:
- Data transmitted over public networks (Wi-Fi, Bluetooth, ) is vulnerable to eavesdropping and man-in-the-middle (MITM) attacks.
Best Practices:
- Avoid public or unsecured Wi-Fi networks unless using a VPN (Virtual Private Network).
- Disable Bluetooth and NFC when not in
- Use only encrypted communication protocols like HTTPS and
4. Avoid Jailbreaking or Rooting Devices Why It Matters:
- Jailbreaking (iOS) or rooting (Android) removes built-in security controls, exposing the device to malware and unauthorized apps.
- It voids warranties and prevents access to official
Best Practices:
- Use devices with stock firmware to ensure manufacturer security features remain intact.
- Educate users about the risks of jailbreaking or
5. Don’t Store Sensitive Information on Mobile Devices Why It Matters:
- Devices are at risk of being lost, stolen, or
- Storing sensitive data increases the risk of data
Best Practices:
- Use secure storage solutions for confidential files (e.g., encrypted cloud storage).
- Avoid saving sensitive information like company credentials or financial data on mobile devices.
- Encrypt local storage if sensitive data must be stored
6. Use Remote Desktop Solutions (e.g., Citrix) Why It Matters:
- Remote desktop solutions allow secure access to corporate systems without storing sensitive information locally on mobile devices.
Best Practices:
- Configure remote access solutions with multi-factor authentication (MFA).
- Limit access to only authorized devices and
- Monitor and log remote sessions for unusual
7. Use Only Official App Stores Why It Matters:
- Third-party app stores are not always vetted, increasing the risk of downloading malicious apps.
- Official app stores (e.g., Google Play, Apple App Store) implement security measures to detect and remove harmful apps.
Best Practices:
- Avoid sideloading apps or using APK files from unknown
- Use mobile device management (MDM) solutions to whitelist approved apps for
- Regularly review and audit installed apps for unnecessary
8. Use Antivirus Software Why It Matters:
- Antivirus software protects devices against malware, spyware, and other
- It provides real-time scanning and alerts users to suspicious
Best Practices:
- Install reputable mobile antivirus
- Keep antivirus software updated to recognize the latest
9. Enable Remote Wipe Options Why It Matters:
- A remote wipe allows users or IT administrators to erase all data from a device if it is lost or stolen.
- Protects sensitive information from falling into the wrong
Best Practices:
- Enable remote wipe functionality through the device’s built-in features (e.g., Find My iPhone, Android Device Manager).
- Test the feature periodically to ensure it works as
10. Implement Remote Management Why It Matters:
- Remote management allows IT administrators to monitor, manage, and secure devices used by employees.
- Essential for managing Bring Your Own Device (BYOD) policies in
Best Practices:
- Use Mobile Device Management (MDM) solutions to enforce security policies
- Monitor devices for compliance and revoke access for non-compliant
11. Enable Remote Tracking Why It Matters:
- Remote tracking helps locate lost or stolen
- Reduces the likelihood of data exposure by recovering the device
Best Practices:
- Enable device tracking features (e.g., GPS-based tracking).
- Use built-in tracking tools like Find My Device (Android) or Find My iPhone (iOS).
12. Mobile Device Management (MDM) Policies for Organizations Why It Matters:
- MDM solutions help organizations enforce security policies, manage app deployments, and secure employee devices.
- Critical for protecting sensitive corporate data in BYOD
Key Features of MDM Solutions:
- Device Enrollment: Automatically enrolls devices into the organization’s security policies.
- App Management: Allows IT to deploy approved apps and restrict access to unapproved ones.
- Data Encryption: Ensures data on devices is encrypted at rest and in
- Remote Wipe and Lock: Enables administrators to remotely lock or wipe devices in case of loss or theft.
- Compliance Monitoring: Monitors devices for security compliance and generates alerts for non-compliance.
Popular MDM Solutions:
- XenMobile
- IBM MaaS360
- VMware AirWatch
- SOTI MobiControl
Additional Tips for Mobile Security
- Use Multi-Factor Authentication (MFA):
- Adds an extra layer of security for app and system
Educate Users:
- Conduct regular training on mobile security best
- Warn users against clicking on suspicious links or downloading unverified
Encrypt Backups:
- Ensure backups (local or cloud-based) are encrypted to prevent unauthorized
Monitor Network Connections:
- Avoid connecting to unknown or untrusted
- Use firewalls and intrusion detection/prevention systems (IDS/IPS).
Mobile platform hacking presents significant risks like unauthorized access, data breaches, and device manipulation. Common attack vectors include device exploitation, network vulnerabilities, malicious apps, and phishing. To protect mobile platforms, users and developers should implement best practices such as keeping software updated, using strong authentication, encrypting communications, and regularly auditing security. These proactive measures can mitigate most mobile security threats.




