Introduction:
While Data Science is a domain which lets you to study vast sets of data to extract meaningful information, insights by using specialized tools. Technologies like Artificial Intelligence and Machine Learning have made data processing way faster and more efficient. This lets you discover unknown transformative patterns, innovate new products, provide solution, and allow real-time optimization. On the other hand, Cybersecurity is a domain which provides security to your systems, network, programs, devices and data from cyber-attacks. In today’s rapidly growing digital landscape, hacking and breaking into systems of people and organization has caused a major concern worldwide. Attackers frequently invent new and complicated methods to compromise a system and steal valuable information and data. The World Economic Forum’s ‘Global Risk Report 2023’ states that Finance & Insurance, Health-care Sector will continue to be at the risk, and Cyber Security will remain a persistent issue. In fact, the target spectrum has expanded and other industries like Government & Public Sector, Manufacturing, Retail, and Energy & Utility will also pose a significant threat.
The intersection of data science and cyber security can prove to be a game changer. While, data science lets to you analyze vast data to derive insights, recognize trends and patterns. When applied to cyber security, these analytical capabilities will help in forming a proactive and robust defensive strategies to predict and stop threats before they cause severe harm. This combination enhances an organization’s security structure and can prove to be unbeatable. In the early days, an organizations security measures and predictions were dependent on hypothesis and assumptions. This changed when, data science entered the picture. Organizations and Business now recognize the importance of data-driven approach. Data science predictions are more accurate and fact-based which helps cyber security analysts to develop more effective security models and strategies.
Data Science Application in Cyber Security:
The aim of Cyber Security is to detect and stop threats like malware, intrusion, attacks, and fraud. With the help of data science, organizations can analyze large number of data sets to identify anomalies and unusual patterns in network traffic, system logs, and user behavior in early detection of cyber threats. Anomaly detection is an important process in machine learning as it helps to identify unusual patterns in datasets. The process lets you automatically detect unusual and potentially critical event that may get hidden in the large sets of data. While processing large amount of datasets, anomaly detection flags irregularities that may indicate fraud, system failures or malwares.
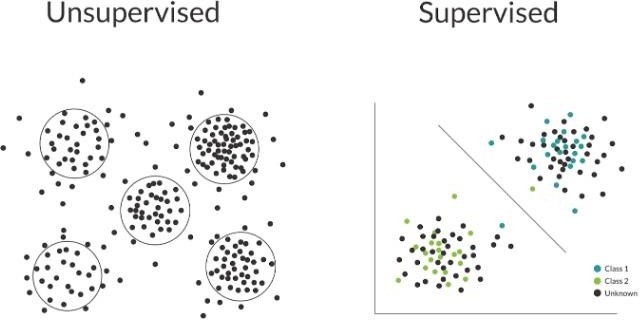
Anomalies can be detected with 3 ways using Machine Learning:
Supervised Learning:
In this method, ML Engineers use training dataset. Items in this dataset fall into two types of categories: Normal and Abnormal. The ML Model will then use these samples to extract patterns and detect previously unseen anomalies in the data. The quality of the training dataset matters a lot in the Supervised Learning. Supervised Learning Models can provide higher detection rate of anomalies. Logistic Regression, Linear Regression, Random Forest, K-nearest Algorithm, Decision Trees, Supervised Neural Network, and Support Vector Machine are some of the examples of models than uses supervised learning.
Unsupervised Learning:
Unsupervised Learning method uses datasets in which no parts are labelled or marked as nominal or anomalous. This setting requires other tools to organize unstructured data. The main purpose of unstructured data is to create clusters from data. Neural Network Algorithms are example of models that use unsupervised learning method.
Semi-Supervised Learning:
Semi-Supervised Learning is a method which falls between supervised and unsupervised learning. This method uses small amount of labeled data and large amount of unlabeled date to train a model. The goal of semi-supervised learning method is to learn a function which can predict the output accurately. Text Classifier, Image Classifier and Anomaly Detection are some examples of semi-supervised learning.
Threat Detection:
Cyber Security professionals use the insights generated by the Data Analysts to develop and implement security measures. The process can include updating of intrusion detection system, creating firewalls, establishing behavior analytics to monitor users and their activities. AI/ ML is at the center of cyber security decision making. Although, AI/ ML powered threat detection models prove to be highly effective in mitigating cyber-attacks, cyber criminals still constantly evolve and change their attacking methods/ strategies to evade the systems. Developing a threat detection AI/ ML Model is a complex task which requires expertise in threats and machine learning. To ensure, efficiency and accuracy of the final system, there is a process which is followed. Here’s a simplified overview of steps involved:
- Define the problem and decide what kind of threats the model should
- Collect and prepare data: Gather data related those threats, clean the data for
- Select
- Choose the right AI Model which suits the
- Train the model: After the data is gathered and clean, teach the model to detect
- Test and improve: Test the model’s performance, make adjustments and improve the
- Implementing and Updating: Put the model in real-time use, and keep updating it with new data to stay effective.
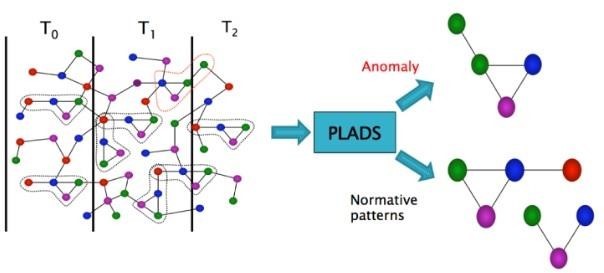
Diagram of Anomaly Detection.
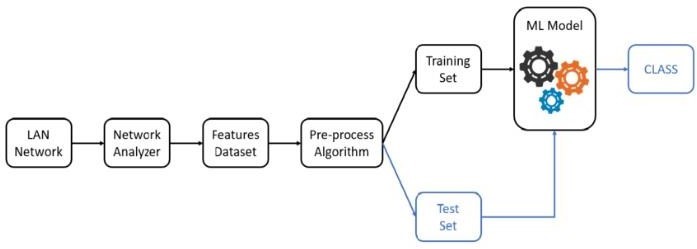
Machine Learning workflow in Intrusion Detection.
Predictive Analysis for identifying potential security breaches:
Cybersecurity has always been a battle between attackers and defenders. While the hackers constantly evolve and develop more sophisticated attacks, the cyber security professionals also must constantly evolve their approach of mitigating threats and stay ahead of the game. The main element of predictive analysis is machine learning. The process involves collecting data, analyzing and applying techniques to anticipate potential cyber security threats and prevent it.
Predictive Analysis can also help to assess threat severity. The advantages of using predictive analysis in cyber security are as follows:
- Early Detection and Prevention: Analyzing anomalies helps the models to detect threats at the earliest stages. This allows to effectively prevent breach
- Optimizing Resource: Predictive Analysis allows the security team to focus its efforts and resources where it’s most required. Prioritizing high risk areas.
- Improved Incident Response: Predictive Analysis can model various attack scenarios hence improving incident response.
- Demonstrating Compliance: Predictive Analysis helps organizations in regulated industries to meet compliance by demonstrating how to take proactive measures to secure their data and prevent security breaches.
Predictive AI in Cyber Security.
Big Data Analytics in Cyber Security:
Big Data Analytics in Cyber Security involves the ability to gather huge amount of digital information to analyze, visualize and draw insights for prediction and stop cyber-attacks. Big Data is large and complex compared to Traditional Data Set. The traditional dataset processing applications are inadequate or unable to deal with these complex and large dataset. The major difference between a traditional and big data set is the volume, velocity and variation. The volume is the amount of data generated, velocity is the speed at which the data gets generated, variation means type of structured and non-structured data. Real-time monitoring is network activity tracking which allows users to analyze traffic patterns and performance and user behavior. Benefits of Big Data Security are as follows:
- Reduced Risk of Data
- Improved Decision
- Increased Customer
- Improved Decision
- Competitive
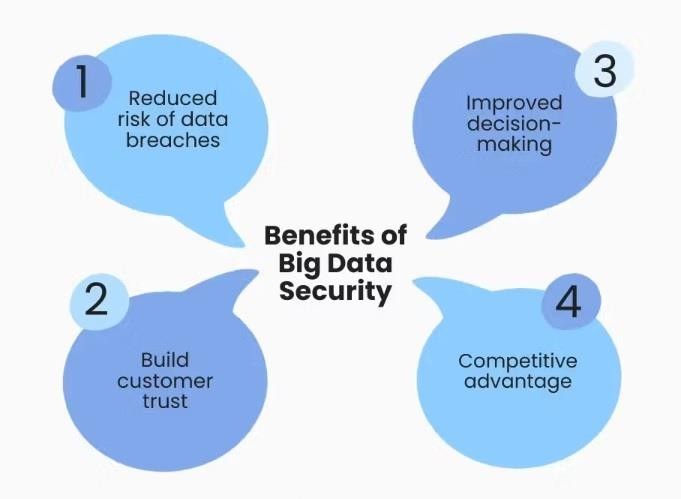
Benefits of Big Data Security Chart.
Machine Learning for Cyber Threat Intelligence:
In the era of rapid technological growth, the cyber security domain as well as the world faces unparalleled challenges. In this digital world, large amount of data generated becomes a boon as well as a bane for digital world. Traditional ways of threat detection in today’s date proves to be incompetent against the evolving tactics of cyber-attacks. NLP (Natural Processing Language) which is a subfield of A.I (Artificial Intelligence) holds a power to reshape the landscape of cyber-security. Application of NLP in Cyber Security are as follows:
- Threat Intelligence and Monitoring: NLP comes handy in threat intelligence. By analyzing vast amount of text data from various sources, NLP helps identifying patterns and extract relevant information. This enhances monitoring of potential threats and provides insights.
- Anomaly Detection and Linguistic Analysis: Traditional Anomaly Detection suffers from problem of false So Linguistic Analysis through NLP, allows the system to differentiate between a genuine threat and a harmless pattern.
- Phishing Detection & Email Security: NLP helps in detecting phishing attempts by analyzing the language used in It can identify suspicious patterns, such as unusual request or copied/ imitated writing style or suspicious link, thereby strengthening
organization’s email security measures.
- Incident Response and Forensics: When the system security encounters a threat, time is of the utmost NLP will accelerate forensic analysis process by analyzing through logs, incident reports, and communication transcripts. NLP will quickly identify critical information enables a faster and more effective response.
ML uses supervised and unsupervised techniques for classifying and prioritizing threats. Supervised learning contains ML Algorithm that need to be trained using labeled datasets. Unsupervised learning contains ML algorithm that learns from entirely unlabeled datasets.
Automated Threat Hunting using AI/ ML:
Cyber Security is a constant battleground. Businesses and Organizations face constant challenges of protecting themselves against emerging threats. So Businesses and Organization turn towards innovative techniques like Automated Threat Hunting. This strategy uses AI/ML to proactively detect and stop potential security breaches before they can cause security damage. AI/ ML algorithms analyze vast volumes of data in real-time to hunt for threats. They identify unusual activity patterns and potential threats based on historical information. This will allow security team to act quickly and reduces the risk of data breaches and operational disruption.
Benefits of ATH:
- Improved Detection: Advanced Algorithm can analyze complex data with remarkable precision, enhancing the accuracy of threat identification and detection.
- Faster Response: Automated systems can quickly detect and address threats in real
- Cost-Effectiveness: Organizations can optimize their resources and lower operational expenses by automating repetitive tasks.
Cyber Security Challenges addressed by Data Science:
An Advanced Persistent Threat (ATP) is a prolonged and targeted cyber threat attack in which intruders gain access to network and remain undetected for a prolonged period of time. These types of attacks are initiated to steal highly sensitive data rather than cause any damage to
organization’s network. The goal of APT is to achieve and maintain ongoing access to the targeted network rather than breach and get out as quickly as possible. Going deeper into the types of attack: one of the type are Zero Day Attacks. This type of attack exploits a previously unknown vulnerability in a system or a software, which leaves no time for the vendors or developers to fix the problem. Hence Zero Day Attack. Zero Day are considered as one of the most dangerous types of attacks as they are difficult to detect and can cause significant damage to a system or a network. These attacks are carried out by advanced APT groups who have in-
depth knowledge of a system or software’s vulnerabilities. They will exploit these vulnerabilities to gain access to the system and steal sensitive data.
Companies today face wide range of potential threats to digital security. From cyber-attacks to internal threats from negligent employees. To add to the situation, many organization now use hybrid work model, in which some employees may use personal devices for work purpose and it’s difficult to establish ironclad security policies and incident response plans. So organizations must contend with data exfiltration attacks from insiders as well as external hackers. Data exfiltration is movement of company data outside the company. Beyond control server and proper security and protection protocols, attackers may pick on this loophole. Every company has confidential and a sensitive proprietary information, from client data, employee data to sales strategies and more. Companies want to protect this essential data. External Attackers may use phishing or ransomware attacks to steal this data. While Data Exfiltration is an Insider Attack type. There are many types of insider attacks and data exfiltration methods.
Data Exfiltration can happen due to malicious insider threats carrying out exfiltration or may happen due to employee negligence. Here are some examples:
- Unintentional Exfiltration by
- Intentional Malicious
- Hackers gaining access to Target Machines
- Cloud Apps and
- Exfiltration through Removable Storage
- Email Data
Data Exfiltration can be prevent using following steps:
- User Activity
- Using Data Loss Prevention
- Implementing Insider Threat Detection
- Endpoint Detection and Response
- Access Management and
- Continuous Monitoring and Incident
Vulnerability Management and Patch-Prioritization:
Vulnerability-management is the process of identifying, scanning, and prioritizing the vulnerabilities for remediation. Many organizations manage vulnerabilities on a case-by-case approach. Only minimum work is required to keep the network and system protected. On the other hand, Patch-management is the operational process where patches are applied to vulnerable system. The life-cycle of vulnerability management is as follows:
Approach to manage vulnerabilities, which includes the patch management life cycle:
- Assess vulnerabilities and their levels of risk to the
- Prioritize patches and patching the
- Review and assess the
- Continues monitoring and reporting on
Data Privacy and Ethical Consideration:
Law and ethics are directly related to privacy, trust, and security. Trust is essential for both security measures and privacy protection. Privacy violations are dangerous and pose a threat to security. When ethics cannot give a remedy, law can. Ethics provide context. In addition to undermining confidence and increasing the possibility of security being compromised, privacy violations are also a disdain for the law and moral standards.
The legal right of the data subject to access, use, and collection is what is meant by data privacy, often known as information privacy or data protection. This alludes to:
- Freedom from illegal access to personal information,
- Misuse of the data,
- Accuracy and comprehensiveness while using technology to gather information about an individual or individuals (including companies),
- Accessibility of data content and the legal entitlement of data subjects to access it; ownership,
- The rights to review, update, or amend these
It is true that maintaining data privacy is difficult and urgent. The pervasiveness of the information-intensive and technology-driven environment makes this protection essential. Modern corporations typically conduct information-intensive and technology-driven corporate activities. Among the advantages of this trend are increased market transparency, improved consumer education, and more equitable trading practices. The drawbacks include the emergence of new avenues for organized and skilled cybercriminals to prey on, as well as socio-techno risk, which stems from both technology and human users (e.g., identity theft, information warfare, phishing schemes, cyberterrorism, extortion). Information protection rises to the top of the company management agenda as a result of this danger.
The multidirectional demand makes data privacy protection even more urgently needed. To guarantee that data privacy rules, standards, guidelines, and processes are suitably improved, communicated, and adhered with, as well as that effective mitigation mechanisms are put in place, information protection becomes a crucial information security role. Since many of the issues that arise after implementation and contract signing are of a technical and ethical nature and information security decisions become more complex and difficult, the policies or standards must be technically efficient, economically/financially sound, legally justifiable, ethically consistent, and socially acceptable.
The approach is built on a framework that was first intended to give decision-makers a new perspective. It is based on the following three main instruments:
- The International Data Privacy Principles (IDPPs) are guidelines for creating and upholding o operating standards, mitigation strategies, and data privacy policies.
- The Personal Data Protection Principles (DPPs) of Hong Kong for upholding those rules, regulations, and policies
- The operationalization framework of hexa-dimension metrics for enforcing rules, regulations, and recommendations.
Compliance with regulations such as GDPR and CCPA:
The General Data Protection Regulation, or GDPR, is a set of laws inside the European Union aimed at protecting citizens’ rights to privacy and data protection. On the other hand, the California Consumer Privacy Act, or CCPA for short, is a state law that was passed in the US to protect the rights of Californians to their privacy and data.
5 Differences between GDPR and CCPA are as follows:
GDPR:
- The GDPR law applies to all companies and their organizations (websites and mobile applications) that process personal data of individuals within the European Union (EU). This covers e-commerce enterprises as well as nonprofit organizations.
Every Data Subject (user) in the EU is subject to GDPR compliance, regardless of their nationality, kind of residence, or anything else.
- The GDPR is more stringent than the CCPA, which is reflected in its definition of protected data and its exclusions.
Regardless of the purpose or method of processing, all forms of data processing are covered by GDPR. There are just two exclusions:
- When non-automated means (i.e., no electronic technologies) are employed to process the data.
- When people use data to further their own
- According to GDPR, “processing” refers to actions including obtaining consent for data processing, telling users of the purpose of data collection and how it will be used, informing users of their data rights, and erasing or removing data.
CCPA:
- Legal inhabitants of the California region are the only ones who can use the
Only companies that satisfy at least one of the following three requirements are subject to the CCPA:
Companies with a gross yearly revenue higher than $25 million gathers, purchases, or distributes more than 50,000 users’ data The sale of said user data generates half (50%) of the money.
These are the conditional qualifiers; nevertheless, in order for a business to be subject to CCPA regulation, it must also meet two other requirements.
They are active throughout the California Area.
They have disclosed the reason and methods for their data processing operations, and they gather user data in California.
- The CCPA does not cover:
Any user information already accessible,
Medical data safeguarded by CMIA and HIPAA certification,
User information protected by the Department of Public Policy and Administration’s (DPPA) CCPA,
Additional data sets that are safeguarded by oversight bodies.
- Three parts comprise the stages of data gathering and processing as outlined by Gathering information from consumers, suppliers, and outside data providers is referred to as collection.
Processing is the process by which a corporation obtains data and begins utilizing it to generate profits.
When the gathered data is sold, it gets moved to a different company.
Future Trends and Innovation:
AI in Cyber-Attack:
Artificial Intelligence is at the vanguard of this transformation, leading to increasingly sophisticated cybersecurity threats. The global average cost of a data breach has risen to a record high of $4.45 million, a 15% increase over three years, according to the IBM Security Cost of a Data Breach Report 2023. This increase can be partially due to the rise of AI-powered attacks, which are getting more complex and difficult to identify.
- These days, phishing assaults use artificial intelligence (AI) to produce incredibly realistic emails and messages that alarmingly closely resemble reliable Imagine getting an email requesting confidential information that appears to be from your boss. That is how AI can be used in phishing.
- In 2019, a sophisticated AI-powered attack targeted an energy company in the United Kingdom. Cybercriminals instructed a finance officer to deposit $243,000 to a bogus account by imitating the CEO’s voice with artificial intelligence (AI). The potential of AI in social engineering is demonstrated by this attack.
- Malware driven by AI can adapt to avoid detection and target the most important resources within an These viruses are not your typical ones; they are intelligent, flexible, and getting worse all the time.
AI in Cyber-Defense:
- Advanced Threat Detection and Prevention: Artificial intelligence (AI) algorithms examine enormous volumes of data to find patterns suggestive of cyber threats. They frequently reveal abnormalities that human analysts would not be able to immediately notice. Example: A large U.S. bank’s AI-powered threat detection system recently stopped a sophisticated attack by spotting odd patterns in what appeared to be typical network traffic, averting a possible $50 million loss.
- Automated Incident Response: Within minutes of identifying a danger, AI-driven security orchestration, automation, and response (SOAR) platforms can start implementing Case Study: By using an AI-powered SOAR solution, a worldwide e-commerce platform was able to drastically reduce the potential damage from assaults by cutting down on typical incident reaction times from three hours to seven minutes.
- Predictive analytics: AI can anticipate future attack vectors and vulnerabilities by evaluating past data and present trends. This enables enterprises to proactively fortify their MIT’s Computer Science and Artificial Intelligence Laboratory recently conducted a study that revealed the ability of AI-driven predictive models to precisely predict 85% of cyber-attacks up to two weeks ahead of time.
- User and Entity Behavior Analytics (UEBA): Through the creation of baseline behavior profiles for people and entities, AI-powered UEBA solutions identify abnormalities that can point to insider threats or compromised accounts. Impact in the real world: An international company attributes the discovery of a persistent insider threat that had eluded conventional security measures for more than a year to their AI-driven UEBA system.
- Network Traffic Analysis: Artificial intelligence systems are able to analyze network traffic in real-time, spotting and stopping harmful activity before it has a chance to do any
Integration of AI/ ML with traditional cyber security tools and processes:
Because AI and ML technologies enable automated responses, predictive analytics, and real-time threat identification, they are revolutionizing the cyber security sector. These cutting-edge instruments examine enormous volumes of data to find trends and abnormalities that might point to a security breech. AI and ML, in contrast to conventional techniques, have the capacity to learn and adapt over time, increasing their efficacy and accuracy in spotting possible dangers.
Cyber dangers are always changing, and so should our defenses. The sophistication of assaults is outpacing the effectiveness of traditional cybersecurity measures.
The capacity of AI and ML to recognize unknown dangers and zero-day assaults is one of its main advantages in the field of cyber security. These technologies are able to detect and eliminate dangers before they have a substantial impact because they do not merely rely on recognized threat signs. Instead, they analyze behavioral patterns. This kind of proactive strategy is critical in a world where cybercriminals are always coming up with new strategies.
AI-powered security systems may also automate reactions to threats that are discovered, which shortens the time it takes to neutralize attacks and lessens their possible impact. This improves an organization’s overall security posture and frees up security professionals to work on more intricate and important projects.
AI and ML will become more and more important in protecting our digital world as they develop. Businesses that use these technologies will be more capable of safeguarding their resources, upholding client confidence, and preventing new online threats.
Case Studies and Examples:
Within the rapidly evolving field of cybersecurity, data scientists are essential in safeguarding enterprises from online attacks. They find hidden patterns and abnormalities that can point to possible cyberattacks or vulnerabilities by applying their knowledge in machine learning techniques and data analysis.
Predictive analytics is one example of how to find anomalous user activity on a network. Through the examination of vast amounts of network traffic data, data scientists are able to create models that are capable of detecting anomalies in typical activity patterns. In order to prevent damage from happening, this assists businesses in proactively identifying possible insider threats or compromised accounts.
Using anomaly detection methods to find malicious activity within a system is another real- world use. Data scientists examine different kinds of log files, such firewall or web server logs, to identify unusual activity that might signal to a continuous attack. These methods provide early identification and prompt action to stop additional infiltration.
Threat intelligence greatly benefits from the application of data science. Through the collection and analysis of extensive external threat data from a variety of sources, such as hacker networks or dark web forums, data scientists can offer invaluable insights into new patterns and developing attack methodologies. By using this information proactively, firms may implement the appropriate security measures and stay one step ahead of the competition.
Malware identification and prevention are achieved through the use of machine learning techniques. These algorithms are trained by data scientists using large datasets that contain known malware samples. This allows the algorithms to accurately and automatically categorize new files as harmful or benign.
Here are some examples of Case Studies:
- The Equifax Data Breach: Among the most notorious cyberattacks in recent memory was the Equifax data leak that occurred in 2017. Over 147 million people’s personal information was compromised in this incident. A weakness in their web application framework caused the incident. This case emphasizes the necessity of strong security protocols, frequent software upgrades, and thorough penetration testing to find and fix any vulnerabilities before malevolent actors take advantage of them.
- The NotPetya Ransomware Attack: The NotPetya ransomware attack of 2017 affected organizations all around the world and resulted in damages worth billions of dollars. Through a hacked software update, the malware entered Numerous businesses experienced significant operational disruptions, notably the pharmaceutical major Merck and the massive shipping company Maersk. The significance of supply chain security and confirming the integrity of software upgrades prior to implementation is highlighted by this example.
- Target Corporation’s Point-of-Sale Breach: Over 40 million customers of Target Corporation were impacted by a serious data breach that occurred in 2013. By using a third-party HVAC contractor to get access to the retailer’s network, cybercriminals took advantage of lax access safeguards. This event emphasizes how crucial third-party risk management is and how crucial it is to continuously assess and strengthen access restrictions in order to protect sensitive data.
- The WannaCry Ransomware: Thousands of organizations worldwide were the target of the 2017 WannaCry ransomware assault, which encrypted data and demanded ransom payments. It took use of a flaw in out-of-date Windows systems. This illustration highlights how important it is to implement strong cyber security procedures and regular software updates in order to stop and lessen large-scale attacks.
Conclusion:
We discussed the application of Data Science in Cyber-Security using AI/ML technologies and methods. Different types of threats, future trends and innovations, regulations. Businesses need to be on the lookout for emerging trends in cyber security to safeguard their brand and clientele from harm. Gaining knowledge from case studies and real-world examples can help you understand how cybercriminals constantly adapt their strategies. Businesses can protect themselves from cyber-attacks by putting in place robust security measures, regularly assessing vulnerabilities, and encouraging a cyber-aware culture among staff members. By adopting proactive measures to safeguard their digital assets, organizations can prosper in a more secure and safe work environment.



