Meritshot Tutorials
- Home
- »
- Cryptography in Cyber Security
Cyber Security Tutorial
-
What is cybersecurity?What is cybersecurity?
-
Introduction to LinuxIntroduction to Linux
-
Text Processing using GREP, SED, and AWKText Processing using GREP, SED, and AWK
-
Introduction to Ethical HackingIntroduction to Ethical Hacking
-
Footprinting and ReconnaissanceFootprinting and Reconnaissance
-
Scanning NetworksScanning Networks
-
Enumeration in Cyber SecurityEnumeration in Cyber Security
-
Vulnerability AnalysisVulnerability Analysis
-
System HackingSystem Hacking
-
Malware ThreatsMalware Threats
-
SniffingSniffing
-
Social EngineeringSocial Engineering
-
Denial-of-ServiceDenial-of-Service
-
Evading IDS, Firewalls, and HoneypotsEvading IDS, Firewalls, and Honeypots
-
Hacking Web ServersHacking Web Servers
-
Hacking Web ApplicationsHacking Web Applications
-
SQL InjectionSQL Injection
-
Hacking Wireless NetworksHacking Wireless Networks
-
Hacking Web ApplicationsHacking Web Applications
-
Hacking Mobile PlatformsHacking Mobile Platforms
-
IoT HackingIoT Hacking
-
Cloud ComputingCloud Computing
-
CryptographyCryptography
Cryptography
Cryptography is the study of methods used to secure communication and data from unauthorized access or adversaries. It transforms data into an unreadable format to conceal its original meaning. This field focuses on designing and analyzing protocols to prevent malicious entities from intercepting or accessing data exchanged between parties. In cryptography, an adversary refers to a malicious actor attempting to exploit vulnerabilities to gain unauthorized access to information.
The four key principles of modern cryptography are as follows:
- Data Confidentiality: Ensures that access to data is limited to authorized individuals or locations, following established rules and
- Data Integrity: Focuses on preserving the accuracy and consistency of data throughout its lifecycle.
- Authentication: Confirms that the data being accessed or claimed truly belongs to the user.
- Non-repudiation: Guarantees that individuals involved in a transaction or contract cannot deny their participation or the authenticity of their signatures on the associated documents.
Evolution of Cryptography
Cryptography has its origins alongside the development of writing. As civilizations formed into groups, tribes, and kingdoms, they began to engage in battles, politics, and the pursuit of power, which highlighted the importance of maintaining data secrecy. This need for privacy and selective communication led to the continuous evolution of cryptographic methods.
During the European Renaissance, the Papal and Italian states significantly advanced cryptographic techniques. Various methods and tools were developed to create and decipher secret codes.
In the 15th century, the Vigenère cipher emerged as an improvement in coding techniques, introducing the concept of shifting letters in messages to enhance encryption.
By the 19th century, cryptography had transitioned from basic, ad hoc encryption methods to a more systematic and sophisticated approach to securing information.
The early 20th century brought a technological leap with the invention of mechanical and electromechanical devices like the Enigma machine, which revolutionized data encoding and efficiency.
Cryptography and cryptanalysis took on a highly mathematical focus during World War II, further advancing the field.
In 1975, the U.S. Federal Register introduced the Data Encryption Standard (DES), an algorithm designed to secure electronic communications in banking and financial systems. By 1977, it was rebranded as the Federal Information Processing Standard (FIPS).
In 2001, the Advanced Encryption Standard (AES) officially replaced DES and FIPS, although older encryption methods continued to see use in various contexts.
Cryptography Algorithms
Cryptography is the scientific discipline focused on securing data by transforming it in a reversible manner. It involves cryptographic algorithms that convert data from a readable form (plaintext) into a secure format (ciphertext) and back again. Encryption refers to the process of converting plaintext into ciphertext, while decryption is the process of reverting ciphertext back into plaintext.
Cryptographic algorithms can be broadly categorized into three main types:
1. Symmetric Key Cryptography (Private Key)
In symmetric key encryption, a single shared key is used for both the encryption and decryption of data. This approach is efficient and faster but requires the sender
and receiver to securely exchange the key. A widely known example of symmetric key cryptography is the Data Encryption Standard (DES).
2. Asymmetric Key Cryptography (Public Key)
Asymmetric encryption uses a pair of keys—a public key for encryption and a private key for decryption. This eliminates the need for sharing a common key, making it more secure in environments where key exchange poses a challenge.
3. Hash Functions
Hash functions transform data into a fixed-length hash value through a one-way mathematical process. These functions are irreversible, meaning it is nearly impossible to retrieve the original data from the hash. Hash values are often used for verifying data integrity.
What is Cryptanalysis?
Cryptanalysis is the practice and science of deciphering ciphertext without access to the original encryption key. It is closely tied to cryptography, as both disciplines complement each other. Cryptanalysis focuses on studying cryptographic systems to identify vulnerabilities and break their encryption. It is also used to evaluate and strengthen the security of newly developed cryptographic methods.
By applying mathematical techniques and systematic analysis, cryptanalysis aims to uncover the plaintext or encryption keys from ciphertext. The effectiveness of cryptanalysis depends on factors such as time, computational power, and storage resources. Some of the most common cryptanalysis attacks include:
- Dictionary Attack: This method uses a predefined list of words (a wordlist) to guess and match either the plaintext or the key. It is frequently employed to crack encrypted passwords.
- Brute Force Attack: This approach systematically attempts all possible combinations of plaintext to match the ciphertext until the correct one is
- Rainbow Table Attack: This method uses precomputed hash values stored in a table and compares them to the ciphertext to identify matches.
Components of cryptosystems
The components of a cryptosystem include the following:
- Plaintext: This is the original, unaltered data that needs protection during
- Encryption Algorithm: A mathematical process that transforms plaintext into ciphertext using an encryption key.
- Ciphertext: The encrypted, scrambled version of the plaintext generated by the encryption algorithm. Ciphertext can be intercepted by anyone with access to the communication channel but cannot be understood without the decryption key.
- Decryption Algorithm: A mathematical process that converts ciphertext
back into plaintext using a decryption key. This algorithm ensures that a unique plaintext is retrieved for any given decryption key and ciphertext.
- Encryption Key: A specific value known to the sender, used as input along
with plaintext in the encryption algorithm to produce ciphertext.
- Decryption Key: A value known to the receiver that is related to, but distinct from, the encryption key. It is used as input in the decryption algorithm to convert ciphertext back into plaintext.
- Interceptor: An unauthorized entity attempting to access the plaintext. While they may have access to the ciphertext and even know the decryption algorithm, they lack the decryption key needed to retrieve the plaintext.
Types of encryption
Encryption can be categorized into two main types based on the method used for encryption and decryption. These are:
1. Symmetric Key Encryption
- Asymmetric Key Encryption Symmetric Key Encryption
Symmetric key encryption involves using the same key for both encrypting and decrypting data. This is also referred to as a secret key cryptosystem. Common
examples of symmetric encryption methods include DES (Digital Encryption Standard), BLOWFISH, Triple-DES, and IDEA.
In this method, both parties must share a common key to exchange data securely. To maintain security, the key must be updated frequently to prevent unauthorized access. A secure method is essential for distributing the shared key between communicating parties.
Symmetric encryption is known for its efficiency since the keys used are shorter, making the encryption and decryption processes faster. Additionally, this method demands less processing power compared to asymmetric encryption, making it suitable for systems with limited resources.
Asymmetric Key Encryption
Asymmetric key encryption uses two different keys for encryption and decryption. These keys are mathematically related but distinct, enabling the ciphertext to be decrypted to plaintext.
Each user has a pair of keys:
- Private Key: Kept secure by the
- Public Key: Shared openly in a public
When one key encrypts the data, only the other key can decrypt it. This encryption process is also known as Public Key Encryption. While the two keys are mathematically connected, it is computationally infeasible to derive one key from the other, ensuring strong security.
For instance, if Host1 wants to send data to Host2, it encrypts the data using Host2’s public key. Host2 can then decrypt the data using its private key.
Asymmetric encryption is more secure than symmetric encryption but requires longer keys, making the encryption and decryption processes slower. Additionally, it demands higher computational power to execute the encryption algorithms, making it better suited for scenarios where security is more critical than speed.
How do various algorithms work?
The working process of various algorithms are as follows:
Symmetric Key Cryptography: Symmetric Key Cryptography is an encryption method in which the message of the sender and receiver share a common key that can be used to decrypt and encrypt the message. The most popular symmetric key system is the Data Encryption Standard (DES).
Transposition Ciphers: The transposition ciphers is a method of encryption by which the positions are held by the units of plaintext that are shifted as a regular system. Hence the ciphertext constitutes a permutation of the plaintext.
Example: Consider a Plaintext “SEE YOU SOON” and change their positions to the key used in th
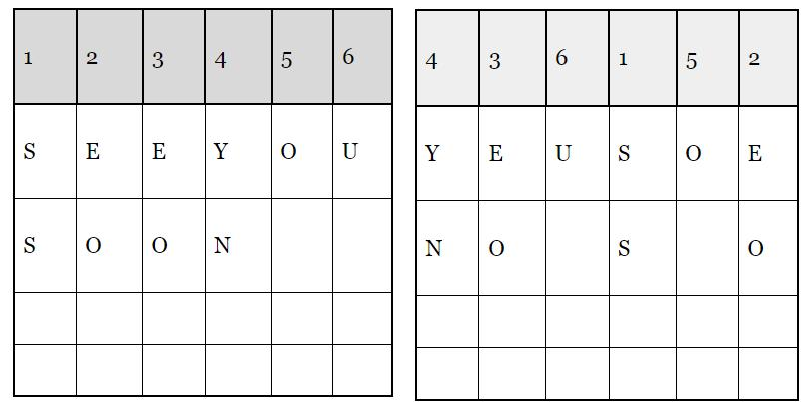
Ciphertext is YEUSOENOSO
Substitution Cipher
A substitution cipher is an encryption method where the elements of plaintext are replaced with ciphertext based on a predefined system. These elements can consist of single letters, pairs of letters, groups of three, or a mix of these.
Example:
Let’s take plaintext and encrypt it using a substitution cipher method.
- Plaintext Alphabet: ABCDEFGHIJKLMNOPQRSTUVWXYZ
- Keyword: MINDMAJIX
- Ciphertext Alphabet: MINDAJXBCEFGHKLOPQRSTUVWYZ
In this case, the letters in the keyword are prioritized in the ciphertext alphabet, and the remaining letters are added in order, excluding duplicates.
Stream Cipher
A stream cipher is a type of symmetric encryption where each digit of the plaintext is combined with a digit from a pseudorandom cipher digit stream, known as the keystream. Encryption is done one digit at a time, pairing each plaintext digit with its corresponding keystream digit to generate the ciphertext.
Block Cipher
A block cipher is an encryption method that processes a block of plaintext by applying an algorithm along with a symmetric key. Unlike stream ciphers, which encrypt one bit or digit at a time, block ciphers encrypt data in fixed-sized blocks.
RSA Algorithm
The RSA algorithm, named after its inventors Rivest, Shamir, and Adleman, is an asymmetric encryption technique widely used in modern cryptographic systems. It uses a pair of keys:
- A public key for
- A private key for
This algorithm ensures secure communication by generating key pairs that work together to encrypt and decrypt messages.
Advantages of Cryptography
Cryptography offers several key benefits, including:
- Data Integrity: Ensures that data remains unaltered during storage or
transmission between sender and receiver without unauthorized detection or interference.
- Authentication: Confirms the identity and origin of the data, making it easier to verify its It also safeguards data across various devices,
regardless of where it is stored or transferred.
- Non-repudiation: Prevents the sender or originator of the data from denying their actions related to its transmission.
- Data Protection: Cryptography’s primary goal is to secure sensitive data, ensuring its confidentiality and safety during communication or storage.
Limitations of Cryptography
While cryptography has significant advantages, it also has some limitations:
- System Vulnerabilities: Cryptography does not protect against weaknesses in system design, procedures, or protocols, which can still be exploited by attackers.
- Access Challenges: Strong encryption, authentication, and digital signatures can sometimes make it difficult for authorized users to access the information when urgent decisions need to be made.
- Awareness Issues: Users may underestimate the importance of cryptographic measures for selective access control and information
- Dependency on Computational Strength: The security of cryptographic
methods relies heavily on the computational complexity of the underlying mathematical problems.




