Meritshot Tutorials
- Home
- »
- Hacking Web Applications in Cyber Security
Cyber Security Tutorial
-
What is cybersecurity?What is cybersecurity?
-
Introduction to LinuxIntroduction to Linux
-
Text Processing using GREP, SED, and AWKText Processing using GREP, SED, and AWK
-
Introduction to Ethical HackingIntroduction to Ethical Hacking
-
Footprinting and ReconnaissanceFootprinting and Reconnaissance
-
Scanning NetworksScanning Networks
-
Enumeration in Cyber SecurityEnumeration in Cyber Security
-
Vulnerability AnalysisVulnerability Analysis
-
System HackingSystem Hacking
-
Malware ThreatsMalware Threats
-
SniffingSniffing
-
Social EngineeringSocial Engineering
-
Denial-of-ServiceDenial-of-Service
-
Evading IDS, Firewalls, and HoneypotsEvading IDS, Firewalls, and Honeypots
-
Hacking Web ServersHacking Web Servers
-
Hacking Web ApplicationsHacking Web Applications
-
SQL InjectionSQL Injection
-
Hacking Wireless NetworksHacking Wireless Networks
-
Hacking Web ApplicationsHacking Web Applications
-
Hacking Mobile PlatformsHacking Mobile Platforms
-
IoT HackingIoT Hacking
-
Cloud ComputingCloud Computing
-
CryptographyCryptography
Hacking Web Applications
A web application is a program or software that runs on a web browser to perform specific tasks. Any web application has several layers – web server, the content of the application that is hosted on the web server and the backend interface layer that integrates with other applications. Web application architecture is scalable and has components which have high availability.
- Web applications are software
- Multi-billion dollar software companies inadvertently create a massive number of vulnerabilities in their software.
- Your web developers have a lot less training and resources than software companies
- Development standards emphasize functionality, not security .
- C-Levels understand other topics better – IDS / IPS,
- Web App dev not approached as
Ethical Hacking is the process of the appropriating the web application from its actual user by tinkering in various ways. The web application hacker needs to have deep knowledge of the web application architecture to successfully hack it. To be a master, the hacker needs to practice, learn and also tinker with the application.
Web application hacking requires tenacity, focus, attention to detail, observation and interfacing. There are many types of web application hacking, and many defense mechanisms available to counter and to protect the application from being hacked.
Most Exposed and Least Protected
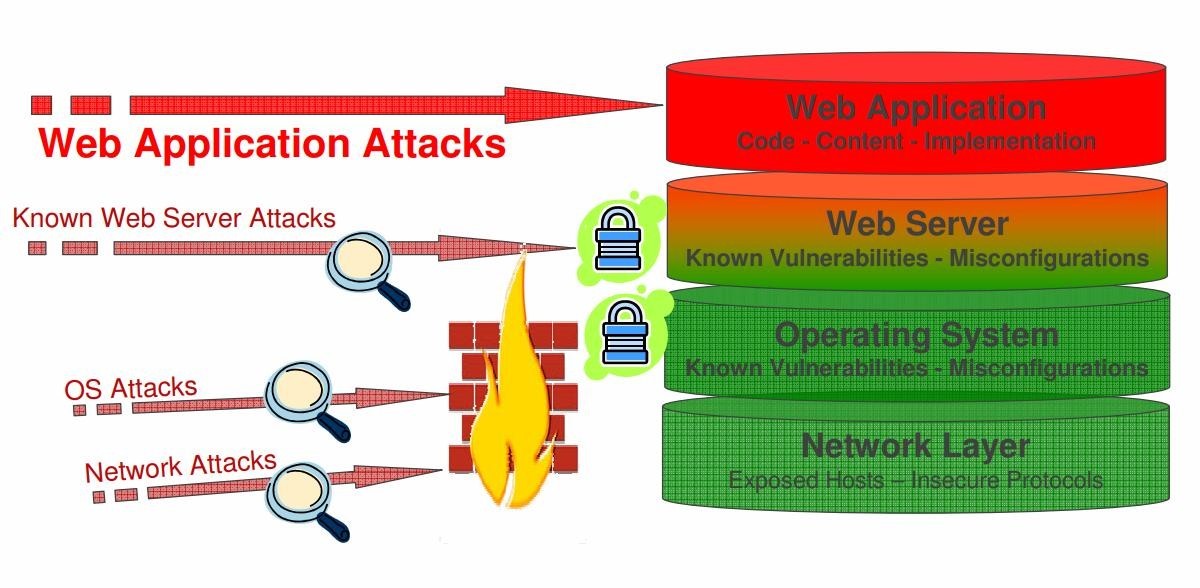
Core Defense Mechanisms for Web Application Security
To ensure robust protection of web applications, defenses can be categorized into four primary areas:
- User Access Handling
- User Input Validation
- Defensive and Offensive Measures Against Hackers
- Application Configuration for Intrusion Alerts
1. User Access Handling
Web applications often provide varying roles and permissions based on business requirements and user scenarios. Examples include:
- Digital Banking: Customers access account balances or transfer funds
- Linux Administration: Administrators assign privileges and rights to authorized
Security Mechanisms:
Authentication:
- Identifies users based on credentials (e.g., username and password).
- Enhancements include multi-factor authentication (e.g., mobile OTP, biometrics).
Session Management:
- Ensures a seamless, secure user experience during active
- Tracks login events and session activities to prevent hijacking or timeout
Access Control:
- Protects HTTP requests by restricting access to authorized
- Acts as the final defense layer to prevent unauthorized data or resource
2. User Input Handling
All user inputs are inherently untrusted and must be validated to protect against malicious activities.
Mechanisms:
Input Validation:
- Reject harmful inputs using semantic checks (blacklisting known hacking- related keywords).
- Use safe data handling by creating rules to accept specific inputs (e.g., only numeric values for account numbers).
Multi-Step Validation:
- Apply layered input validation at every component level within the
Boundary Validation:
- Ensure external interfaces are thoroughly checked for malicious
3. Defensive and Offensive Measures Against Hackers
To thwart hacking attempts and quickly detect threats, implement the following:
Audit Logs:
- Maintain comprehensive records of user activities to monitor suspicious
IP Address Blocking:
- Block malicious or high-risk IPs identified from attack
Intrusion Detection Systems (IDS):
- Use IDS tools to detect and respond to potential breaches in real
Firewalls:
- Deploy application firewalls to block unauthorized access and filter malicious
4. Application Configuration for Intrusion Alerts
Proper configuration ensures that the application can alert administrators to potential threats:
Key Alert Systems:
- Implement critical alert notifications for unauthorized access
- Enable automatic notifications for breaches or suspicious
By implementing these defense mechanisms comprehensively, web applications can enhance their resilience against security threats, protect sensitive data, and provide a secure environment for users.
Web Application Technologies
Developers use a variety of technologies to build modern web applications, categorized into languages, frameworks, libraries, databases, data formats, and protocols. Emerging digital trends like AI and blockchain are also becoming integral. Below is a summary of each technology with brief explanations:
Languages
- HTML: The backbone of web pages, defining structure and layout through elements like headings, paragraphs, and links.
- CSS: Styles web pages by defining layouts, colors, fonts, and responsive
- JavaScript: Enables dynamic, interactive content like animations, form validations, and real-time updates.
- CoffeeScript: A simpler syntax alternative to JavaScript, improving code readability and reducing complexity.
- Python: Versatile programming language often used for web backends, machine learning, and APIs.
- Ruby: A developer-friendly language designed for simplicity, commonly used with Rails for web applications.
- PHP: Server-side scripting language, widely used for content management systems like WordPress.
- Go (Golang): A fast, statically typed language suitable for scalable web servers and cloud-native applications.
- Objective-C: Primary language for building macOS and older iOS
- Swift: The modern alternative to Objective-C for developing Apple iOS and macOS apps.
- Java: Widely used for building large-scale, secure, and platform-independent enterprise web applications.
Frameworks
- js: A runtime for building fast, scalable server-side applications using JavaScript.
- Ruby on Rails: Full-stack framework emphasizing convention over configuration for rapid development.
- Django: A high-level Python framework promoting clean and pragmatic
- Ionic: Framework for building cross-platform mobile apps using web technologies like HTML, CSS, and JavaScript.
- PhoneGap (Apache Cordova): Converts web apps into mobile apps for different
- Bootstrap: A CSS framework that simplifies responsive web design with pre- built components.
- Foundation: A responsive front-end framework with a focus on mobile-first
- WordPress: A PHP-based platform primarily for building blogs, websites, and e- commerce sites.
- Drupal: A robust content management system suitable for complex websites and
- .NET: A Microsoft framework for building secure, scalable web applications and
- AngularJS: JavaScript-based framework for building dynamic single-page
- js: An opinionated JavaScript framework for building ambitious web apps with rich functionality.
- js: A lightweight framework that provides structure to web applications with models and views.
Libraries
- jQuery: A JavaScript library that simplifies DOM manipulation, event handling, and animations.
- js: Provides utility functions for common programming tasks like object handling and array manipulation.
Databases
- MongoDB: A NoSQL database that stores data in flexible, JSON-like documents for modern applications.
- Redis: An in-memory key-value store ideal for caching, session management, and real-time analytics.
- PostgreSQL: A powerful open-source relational database known for its scalability and advanced features.
- MySQL: A popular open-source relational database widely used in web
- Oracle: An enterprise-grade relational database with advanced performance and security features.
- SQL Server: Microsoft’s relational database offering robust tools for enterprise applications.
Data Formats
- JSON: Lightweight and human-readable data-interchange format widely used for
- XML: A markup language for structured data, often used in legacy
- CSV: A simple text format for storing tabular data, frequently used in data
Protocols
- HTTP: The primary protocol for transferring web data between servers and
- DDP: A real-time protocol for syncing data between clients and servers, often used with Meteor.js.
- REST: An architectural style for designing APIs using HTTP methods like GET, POST, and PUT.
Emerging Digital Technologies for Web Applications
- WebAssembly: A low-level language like JavaScript for running high- performance applications in browsers.
- Motion UI Design: Enhances user experience with animations and smooth
- Chatbots: AI-powered conversational interfaces for customer support and
- Artificial Intelligence: Enables intelligent features like recommendation engines and data-driven insights.
- Dynamic Web Applications (PWA): Combines the best features of web and mobile apps for a seamless user experience.
- Blockchain: Provides secure, decentralized data storage for web applications like payments and identity management.
- Single Page Applications (SPA): Enables faster navigation and updates without reloading the entire page.
- AMP (Accelerated Mobile Pages): Optimized for ultra-fast loading speeds on mobile devices.
- VR and AR: Immersive technologies that bring virtual and augmented experiences to web applications.
- Symfony: A PHP framework for building scalable, high-performance web
- Laravel: A developer-friendly PHP framework offering powerful tools for building robust applications.
Bypassing Client-Side Controls
In web applications, data exchange between the client and server is a routine process. While developers often assume that clients will not alter the data, this assumption is risky. Hackers can exploit client-side data manipulation because modifying data on the client side is typically easier than on the server side. Avoiding reliance on client- stored data not only enhances security but also improves performance.
Methods of Bypassing Client-Side Controls
Client-side controls are bypassed when:
- Applications rely on client-side validation to restrict user input, making the controls vulnerable to tampering.
- Applications use client-side methods to control data but fail to enforce proper server-side validation.
Below are techniques commonly used to bypass such controls:
1. HTML Form Features
Hackers can manipulate HTML forms by:
- Altering input fields using browser developer tools to bypass restrictions like max length or input type.
- Modifying hidden form fields to submit unauthorized or unexpected
2. Client-Side Scripts
- Client-side scripts, such as JavaScript, are easily accessible and Attackers can:
- Disable or alter validation
- Use custom scripts to inject malicious data directly into the
3. Thick Client Technologies
Applications using thick client technologies like Flash or Java applets may store sensitive data or enforce validation on the client side. Hackers can:
- Decompile these applications to analyze and modify their
- Use tools to intercept and manipulate the data transmitted to the
Authentication and Authorization in Web Applications
Authentication and authorization are two foundational security concepts essential for protecting web applications. They work together to ensure that users accessing the system are legitimate and only have access to resources they are authorized to use.
Authentication
Authentication is the process of verifying the identity of a user or system. It ensures that an individual or automated system is who or what it claims to be. This is typically achieved using unique credentials such as:
- Username and Password: A standard combination used for identity
- Multi-Factor Authentication (MFA): Enhances security by requiring additional verification, such as a one-time code or biometrics.
- Authentication Standards: Protocols like OpenID, OAuth, and SAML provide secure mechanisms for user identity validation across multiple platforms.
Authentication processes are reliant on secure protocols like HTTP/HTTPS to protect data in transit and prevent credential interception.
Authorization
Authorization is the process of granting or denying access to resources or actions based on the user’s identity and assigned privileges. It ensures that users can only access resources they are permitted to use. Key elements include:
- Access Control: Policies and permissions are defined to restrict or allow user access based on business requirements.
- Privilege Management: Actions requiring elevated privileges (e.g., administrative tasks) are logged for auditing.
- Session Management: Invalid sessions must be terminated promptly to prevent unauthorized access.
Best Practices for Strong Authentication and Authorization Authentication:
- Use strong and unique passwords combined with
- Implement secure authentication protocols to protect sensitive
Authorization:
- Enforce strict role-based access control (RBAC) to limit user access to only necessary resources.
- Log all privileged actions for accountability and
- Automatically terminate expired or invalid
- By implementing robust controls for both authentication and authorization, web applications can significantly reduce vulnerabilities and enhance security against unauthorized access or exploitation.
XSS – Cross-Site Scripting
Cross-Site Scripting (XSS) is an injection attack where malicious scripts are inserted into trusted websites. Attackers exploit web applications to execute browser-side scripts that steal sensitive information like cookies or session tokens and can even manipulate page content.
Types of XSS:
- Stored XSS: Malicious scripts are permanently stored on a server (e.g., in a database), affecting all users who access the page.
- Reflected XSS: Scripts are injected via malicious links and executed immediately, targeting individual users.
- DOM-based XSS: The attack manipulates the browser’s DOM environment, altering client-side scripts without involving the server.
Bypassing Blacklists and Whitelists
- Blacklist: Blocks specific IPs, URLs, or However, blacklists can be bypassed through techniques like encoding or redirection.
- Whitelist: Allows only pre-approved URLs or inputs, making it more secure. Hackers try to bypass whitelists using techniques like DNS spoofing or mixed encoding (hex, octal, URL).
CSRF – Cross-Site Request Forgery
Cross-Site Request Forgery (CSRF) tricks authenticated users into performing unintended actions on web applications. Hackers send links via email or chat to execute unauthorized commands. If successful, a CSRF attack on an admin can compromise the entire application.
Unvalidated Redirects
Unvalidated redirects occur when web applications accept and redirect untrusted inputs. Hackers exploit this to redirect users to malicious sites for phishing or privilege escalation. To prevent this, map short names or IDs to server-validated URLs.
SQL Injection (SQLi)
SQL Injection involves inserting malicious SQL queries into a web application’s input fields. Attackers use this to manipulate databases, retrieve sensitive data, and issue commands that can compromise the application or operating system.
File Upload Vulnerabilities
File upload vulnerabilities allow hackers to upload malicious files (e.g., scripts or executables) through a web application. By exploiting poor validation, attackers gain control over the system and execute unauthorized code.
Attacks on Application Servers
- XSS (Cross-Site Scripting): Executes malicious scripts to steal sensitive
- SQL Injection (SQLi): Manipulates the database using malicious SQL
- File Upload Attacks: Exploits improper file validation to execute unauthorized
- Local File Inclusion (LFI): Allows unauthorized access to server-side
- Distributed Denial of Service (DDoS): Overloads servers with traffic, causing service disruption.
Web Application Hacker’s Toolkit
- Intercepting Web Proxy: Tools like Burp Suite intercept and modify HTTP traffic between browsers and web applications for analysis or exploitation.
- Web Application Scanner: Tools like Nikto scan applications to find
Common Tools:
- Kali Linux: An advanced penetration testing
- Burp Suite: Used for testing and intercepting web app
- Metasploit: A framework for finding and exploiting
- Angry IP Scanner: Scans networks for live hosts and open
- Cain & Abel: Performs password recovery and network
- Ettercap: A tool for network sniffing and MITM (Man-In-The-Middle)
- John the Ripper: A password-cracking
Web Application Hacker’s Methodology
Hackers typically follow a systematic approach that includes information gathering, vulnerability analysis, exploiting weaknesses, and maintaining access to compromised systems.
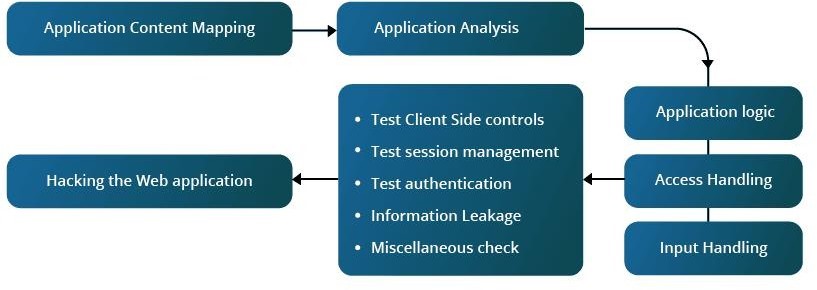
Quick Summary: Hacking Web Applications
Web Application Overview
- Web applications run in browsers, combining web servers, content, and backend
- Security is often overlooked during development, leading to
Ethical Hacking
- Tests for weaknesses in web applications with deep architectural
Core Security Defenses User Access Handling
- Authentication: Confirms user identity (e.g., passwords, multi-factor).
- Session Management: Prevents session
- Access Control: Limits actions based on
User Input Handling
- Validation: Blocks harmful inputs and enforces safe data
Defensive Measures
- Audit Logs: Monitor user
- IP Blocking: Deny malicious
- Firewalls & IDS: Block and detect
Common Vulnerabilities
- XSS: Injects malicious
- CSRF: Forces unintended user
- SQL Injection: Manipulates databases with malicious
- File Uploads: Exploits insecure file
- Unvalidated Redirects: Leads users to harmful
Hacker’s Toolkit
- Tools: Burp Suite, Metasploit, Kali Linux,
- Method: Gather info, analyze vulnerabilities, exploit, and maintain




