Meritshot Tutorials
- Home
- »
- Denial of Service in Cyber Security
Cyber Security Tutorial
-
What is cybersecurity?What is cybersecurity?
-
Introduction to LinuxIntroduction to Linux
-
Text Processing using GREP, SED, and AWKText Processing using GREP, SED, and AWK
-
Introduction to Ethical HackingIntroduction to Ethical Hacking
-
Footprinting and ReconnaissanceFootprinting and Reconnaissance
-
Scanning NetworksScanning Networks
-
Enumeration in Cyber SecurityEnumeration in Cyber Security
-
Vulnerability AnalysisVulnerability Analysis
-
System HackingSystem Hacking
-
Malware ThreatsMalware Threats
-
SniffingSniffing
-
Social EngineeringSocial Engineering
-
Denial-of-ServiceDenial-of-Service
-
Evading IDS, Firewalls, and HoneypotsEvading IDS, Firewalls, and Honeypots
-
Hacking Web ServersHacking Web Servers
-
Hacking Web ApplicationsHacking Web Applications
-
SQL InjectionSQL Injection
-
Hacking Wireless NetworksHacking Wireless Networks
-
Hacking Web ApplicationsHacking Web Applications
-
Hacking Mobile PlatformsHacking Mobile Platforms
-
IoT HackingIoT Hacking
-
Cloud ComputingCloud Computing
-
CryptographyCryptography
Denial-of-Service
Traits of a Social Engineering Attack
A Denial-of-Service (DoS) attack is a malicious cyber-attack aimed at disrupting or completely shutting down the normal functioning of a targeted server, service, or network. The attack typically overwhelms the target with an excessive flood of illegitimate requests, causing it to crash, slow down, or become entirely unresponsive to legitimate users. This denial of access can render websites, online accounts, private data, emails, and other digital services inaccessible, preventing authorized users from retrieving their information or files.DoS attacks are typically launched using a single computer or a network of compromised machines, often called a botnet. These attacks can target a wide range of services and systems, creating significant disruptions. The impact of a successful DoS attack can be severe, including financial losses, reputational damage, and operational setbacks for businesses, government agencies, and individuals.
In essence, a DoS attack prevents legitimate users from accessing their data and services, exploiting vulnerabilities to cause harm, interrupt business operations, or disrupt critical infrastructure. The consequences can be long-lasting, affecting not only the immediate services but also leading to increased vulnerabilities that could be exploited in further attacks.
How Do Denial of Service Attacks Work?
A denial of Service attack is often achieved using TCP and UDP packets. In a DoS attack, the perpetrators flood the user’s system with illegal traffic or service requests to inundate its resources and stop it from executing intended tasks.
A DoS attack can target distinct computers or a whole network system. These attacks can be costly for a company, both in terms of finance and timewise, until their services and other affected resources are restored or become accessible.
Historical Context and Notable Incidents
In the early 2000s, the first major DoS attack targeted Yahoo!, a leading internet portal, rendering its services inaccessible for nearly an hour. This incident highlighted the vulnerability of even the most robust systems.
In 2016, the Mirai botnet DDoS attack exploited IoT devices, crippling major websites like Twitter and Netflix by flooding DNS provider Dyn with traffic. This attack underscored the growing threat posed by the proliferation of connected devices.
Another notable incident occurred in 2018 when GitHub faced a record-breaking 1.35 Tbps attack, leveraging Memcached servers to amplify traffic. These historical events illustrate the evolving tactics and increasing scale of DDoS attacks.
Each incident prompted advancements in defensive measures, from improved traffic filtering to deploying more sophisticated intrusion detection systems. Understanding these pivotal moments provides crucial insights into DoS threats’ persistent and adaptive nature, emphasizing the need for continuous innovation in cybersecurity defenses.
DoS vs DDoS Attacks
DoS attacks involve overwhelming a target with traffic from a single source, while distributed denial of service (DDoS) attacks involve multiple compromised systems flooding the target simultaneously.
The distribution of hosts that defines a DDoS provides the attacker multiple advantages:
- They can leverage the greater volume of machines to execute a more disruptive attack
- The location of the attack is difficult to detect due to the random distribution of attacking systems (often worldwide and from otherwise legitimate systems)
- It is more difficult to shut down multiple machines than one
- The true attacking party is challenging to identify, as they are disguised behind many (mostly compromised) systems
DDoS attacks are the most powerful internet attacks and also the most difficult to detect. The reason being that they are introduced from several locations to hide their
identities and prevent the victim from easily identifying the main source of the attack. As a result, it is unfeasible to distinguish between genuine and counterfeit network traffic.

Another difference between DDoS and DoS attacks lies in the volume of the attack being launched. While DDoS attacks give room for the cyber-attacker to introduce enormous volumes of traffic to the user’s computer or network, DoS cannot afford the attacker with such excesses. Additionally, you should also note that their mode of execution varies as well. While DoS attacks are executed using a script or DoS tool, such as Low Orbit Ion Cannon, DDoS attacks are usually launched using botnets or through the networks of the devices infiltrated by the attacker.
DDoS attacks are challenging to mitigate because blocking one source does not stop the attack. They require more sophisticated solutions, such as traffic analysis, rate limiting, and using content delivery networks (CDNs) to distribute and absorb the traffic load.
How to Tell if You are Experiencing a DoS Attack
The following are some pointers that you are experiencing a DoS attack:
- The incapability to load certain
- The extreme volume of spam
- Uncharacteristically slow network performance, including extended load times for files or websites.
- Prolonged failure to access specific
- A sudden loss of connectivity across devices on the same
Some of the symptoms of a DoS attack often appear as a non-malicious accessibility problem. The most effective method of identifying and detecting a DoS attack is through network traffic monitoring and testing. Network traffic can be scrutinized through an intrusion detection system or a firewall. The network manager or the owner of the device may even establish some instructions that create warnings when an irregular traffic load is detected and also recognize the source of the traffic or leaves network packets that match a certain criterion.
Detection and Identification of DoS Attacks
Early detection and response to a denial of service (DoS) attack by your security operations center (SOC) is critical to business operations. Attackers may attempt to perform a DoS attack via network exhaustion, abuse of cloud resources, or blocking the availability of targeted resources to users and services—all of which can and should be detected by your SOC via best-in-class tools and processes.
Common Indicators of DoS Attacks
Sudden spikes in traffic often signal a DoS attack, overwhelming network resources and causing service disruptions. Unusual patterns, such as repeated requests from a single IP address or a surge in incomplete connections, also indicate malicious activity. Degraded system performance, including slow response times and frequent crashes, further highlights potential threats.
Monitoring tools that analyze traffic in real time can identify these anomalies and provide critical insights. Machine learning algorithms enhance detection by recognizing deviations from normal behavior, enabling quicker responses. Accurate identification of these indicators is vital for mitigating the impact of DoS attacks and maintaining system integrity.
Traffic Analysis and Monitoring
Real-time traffic analysis helps detect DoS attacks by monitoring data packets for irregularities. Advanced systems use machine learning to differentiate between legitimate traffic and potential threats, with automated alerts for immediate response. Effective traffic analysis detects ongoing attacks and provides valuable data for strengthening defenses against future threats.
Differentiating Between Legitimate and Malicious Traffic
Machine learning algorithms analyze behavioral patterns to distinguish between normal and malicious user activity. Legitimate traffic displays consistent, predictable patterns, while malicious traffic often shows erratic spikes and unusual request types.
Deep packet inspection (DPI) scrutinizes data at a granular level to identify anomalies that signal potential threats. Whitelisting known IP addresses and employing rate limiting further refine traffic differentiation. Behavioral analytics track user interactions over time, creating a baseline for normal activity and flagging anomalies for further investigation. These advanced techniques enable networks to filter out malicious traffic and ensure seamless service continuity effectively.
Types of Denial of Service Attacks
Denial of service (DoS) attacks manifest in various forms, each designed to exploit specific vulnerabilities within a system. Understanding these attack vectors is vital for developing resilient cybersecurity strategies.
Buffer Overflow Attacks
A buffer overflow attack is one of the most common types of Denial of Service (DoS) attacks, involving the deliberate overflow of a system’s memory buffer by sending more data or traffic than the system can handle. This causes a variety of system issues, including crashes, unpredictable behavior, or the execution of malicious code.
In a buffer overflow attack, malicious actors exploit vulnerabilities in a program that fails to properly validate or limit the amount of input data, thereby overloading the buffer. This can lead to a range of system failures, including crashes and the potential for arbitrary code execution, which may allow attackers to gain unauthorized access and compromise sensitive information.
Types of attacks related to buffer overflow vulnerabilities include:
- ICMP Flood (Smurf Attack or Ping of Death): This attack involves sending a large number of ICMP (ping) requests to a network device, often using spoofed IP addresses. The target then replies to all the devices on the network, causing a flood of traffic that overwhelms the network.
- SYN Flood: In a SYN flood attack, a connection request is sent to a target server, but the three-way handshake (which establishes a TCP connection) is not completed. These half-open connections fill up the server’s available connections, preventing legitimate users from connecting.
Examples of well-known attacks leveraging buffer overflows include:
- The Morris Worm, which spread in 1988, exploiting buffer overflow vulnerabilities in UNIX systems.
- The Code Red Worm, which exploited buffer overflows in Microsoft IIS servers in 2001.
Mitigation Strategies:
To prevent buffer overflow attacks, several strategies can be employed, such as:
- Input validation: Ensuring that all data inputs are properly checked and sanitized to prevent the overflow of data into memory buffers.
- Regular updates: Keeping software and systems updated to patch known
Ø Security mechanisms:
- Data Execution Prevention (DEP): Prevents the execution of code from non- executable memory regions, blocking some types of attacks.
- Address Space Layout Randomization (ASLR): Randomizes the memory addresses used by system processes, making it more difficult for attackers to predict where their malicious code will be executed.
These measures, when implemented correctly, can significantly reduce the risk of buffer overflow attacks and enhance the overall security of a system.
Application Layer Attacks
Attackers exploit vulnerabilities in web applications, targeting features like login pages, search functions, or database queries. These attacks can overwhelm application resources, leading to slowdowns or crashes. Techniques include HTTP floods and Slowloris attacks.
Mitigation involves implementing web application firewalls (WAFs), optimizing high-traffic code, and employing rate limiting on critical endpoints. Regular security audits and patching of known vulnerabilities can significantly reduce the risk.
Protocol Attacks
Attackers exploit weaknesses in network protocols to disrupt services, often targeting TCP/IP layers:
- SYN flood attacks overwhelm servers and exhaust resources by sending numerous connection requests without completing the handshake.
- DNS amplification attacks leverage vulnerable DNS servers to amplify traffic, directing it to the target.
- Smurf attacks misuse ICMP by sending spoofed packets to a network’s broadcast address, causing all devices to flood the victim with responses.
Mitigation strategies include implementing SYN cookies, rate limiting, and configuring firewalls to block malicious traffic. Regularly updating and securing network infrastructure can significantly reduce the effectiveness of these protocol- based assaults.
Volumetric Attacks
Attackers inundate networks with massive volumes of traffic, overwhelming bandwidth and server capacity. Botnets, comprising thousands of compromised devices, generate this flood, challenging detection and mitigation.
Common tactics include UDP floods, which exploit the connectionless nature of the protocol, and ICMP floods, which bombard the target with echo requests. These attacks can peak at terabits per second, crippling even robust infrastructures.
Effective defenses involve deploying robust traffic filtering, leveraging content delivery networks (CDNs) to absorb excess traffic, and utilizing scrubbing centers to cleanse incoming data. Constant monitoring and adaptive rate limiting can enhance resilience against these high-volume onslaughts.
Cloud-Based Attacks
DoS attacks on cloud resources often focus on hypervisor and crypto-jacking.
Hypervisor DoS Attacks:
- How: These attacks exploit vulnerabilities in the hypervisor layer, which manages and allocates resources to virtual machines (VMs).
- Impact: If successful, the hypervisor can crash, rendering all VMs on that host
- Result: The entire cloud infrastructure becomes unavailable, affecting services and users.
Hypercall Attacks:
- How: Attackers send specially crafted requests to the cloud hypervisor, aiming to extract information or execute malicious code.
- Impact: If the hypervisor processes these malicious hypercalls, it can lead to resource exhaustion or system instability.
- Result: VMs may become unresponsive, causing service
Hyperjacking:
- How: An attacker installs a rogue hypervisor beneath the original The rogue hypervisor remains undetected, allowing the attacker to gain control of the target hypervisor and its resources.
- Impact: With control of the hypervisor, the attacker can manipulate the VM’s behavior, consume resources, or launch further attacks.
- Result: Service degradation or complete unavailability, depending on the compromised VM’s role.
Crypto-jacking:
- How: An attacker compromises cloud resources and installs crypto-mining software to mine crypto-currency
- Impact: Crypto-jacking depletes available resources, such as CPU, RAM, and Network bandwidth, making a VM unresponsive
- Result: Overloaded systems become unresponsive, service degradation or complete unavailability
Teardrop Attack :
In a teardrop attack, the malicious hacker distributes fragments of an IP address packet to a targeted network. In turn, the network tries to reassemble these fragments to its initial packets. The method of assembling all these fragments to their initial packets wears out the system and as a result, it collapses. The system collapse or breakdown is due to the fact that the fields are created to obscure the system to the point where it is unable to assemble them together.
What Is Distributed denial of service (DDoS) Attack With Example?
Distributed denial of service (DDoS) attack is a malicious effort to render an online service or website inaccessible to users, typically by momentarily disrupting or appending the services of the host server. A Distributed denial of service attack naturally comprises of above 3 to 5 nodes on diverse networks, anything lesser may serve as a denial of service attack.
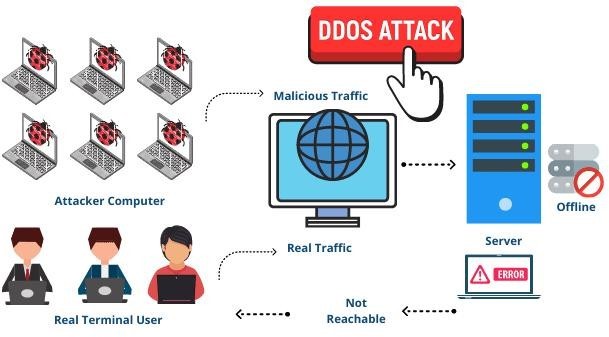
The aim of this attack is to make the website or online service impracticable. The traffic can involve fake packets, incoming mails, or requests for connections.
Sometimes the target is compromised at a low level or threatened with a DDoS attack. This may be joined with blackmail and threats of more overwhelming attacks except the organization meets the set ransom. DDoS typically uses botnets to execute these malicious tasks.
Mechanisms and Tools Used in DoS Attacks
Denial of service (DoS) attacks utilize various mechanisms and tools that can significantly disrupt services. Still, they can also be mitigated with appropriate security measures, such as firewalls, intrusion detection systems, rate limiting, and anti-DDoS services. These mechanisms and tools, when combined, create formidable challenges for cybersecurity defenses, necessitating advanced detection and mitigation strategies to protect against the relentless onslaught of DoS attacks.
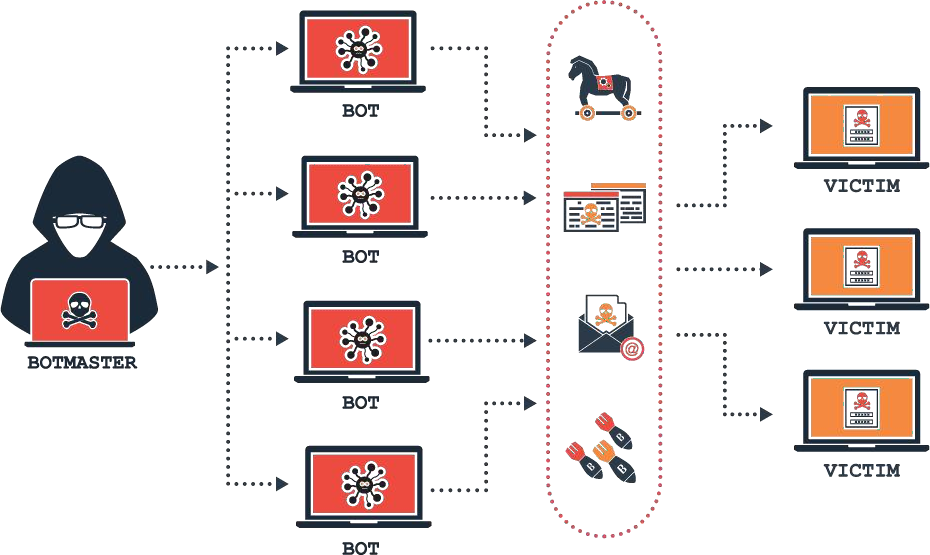
Botnets and Malware
Cybercriminals use botnets, networks of compromised devices, for large-scale DDoS attacks. Infected devices bombard targets with overwhelming traffic without their owners knowing. Malware infiltrates devices through phishing emails, malicious downloads, or unpatched software. Compromised devices become part of a botnet,
controlled remotely by the attacker. Mirai, a notorious botnet, has taken down major websites with massive traffic floods.
The term “botnet” refers to a group of hijacked internet-connected devices that are operated remotely from a Command & Control Center (C&C) by a malicious attacker. A botnet is a combination of the word network and robot and each compromised computer is referred to as a bot. These attacks characteristically comprise of unsecured IoT devices, PCs, smartphones, and sometimes resources from public cloud services.
A botnet is designed by a malicious hacker to achieve malicious tasks or execute illegal actions, such as stealing data, sending spam, fraudulently clicking on ads, ransomware, or Distributed denial of service (DDoS) attacks. Botnets work by allowing attackers to execute DDoS attacks by seizing the control of several computers and disrupting the traffic source of the traffic. It is often hard for security teams and other security applications to identify a DDoS attack until it is too late.
Malicious hackers use malware and other methods to infect a device, rendering it into a “zombie” in the perpetrator’s botnet. Although some malware may have an immediate effect on the device or network owners, DDoS botnet malware can have diverse stages of visibility. Some of this malware is intended to run mutely as a background while mutely awaiting commands from the “bot herder” or attacker.
Other malware is intended to take absolute control of the device or network.
Self-circulating botnets engage other bots through a number of different pathways including Trojan horse malware, the exploitation of website weaknesses, and cracking scrawny verification to obtain remote admission. The moment access has been gained, all these infection techniques lead to the installation of malware on the aimed device. This grants the botnet operator a remote control of the device.
Attack Tools and Scripts
Hackers employ a variety of sophisticated tools and scripts to launch DoS attacks. LOIC (Low Orbit Ion Cannon) and HOIC (High Orbit Ion Cannon) are popular open- source tools that enable users to flood targets with HTTP, TCP, or UDP requests.
Script kiddies often use these tools due to their ease of use.
Advanced attackers might deploy custom Python or Perl scripts to exploit specific vulnerabilities. These scripts can automate the process, launching highly targeted attacks that bypass traditional defenses. Tools like Metasploit also provide modules for DoS attacks, allowing attackers to integrate them into broader exploitation frameworks.
Amplification Techniques
Attackers exploit amplification techniques to magnify the volume of traffic directed at a target, overwhelming its resources. By leveraging protocols like DNS, NTP, and SSDP, they send small requests with spoofed IP addresses, causing servers to respond with significantly larger replies to the victim.
This method, known as reflection, can exponentially increase the attack’s impact. For example, a 1-byte request can generate a 100-byte response, creating a 100:1 amplification ratio. Attackers often combine multiple amplification vectors, making it challenging for defenders to mitigate the flood of malicious traffic effectively.
What Causes Denial of service attacks and Distributed denial of service attacks?
DDoS attacks are fast becoming the most threatening attacks in the Cybersecurity industry. In recent years, DDoS attacks have grown in volume and number, exceeding a terabit per second in 2016. Whether it’s a DDoS or a DoS, there are different malicious reasons why cybercriminals execute DoS and DDoS attacks. Businesses, individuals, and even nation-states have different motivations for these cybercrimes. However, the most common include:
Extorsion or Ransom
The most popular motivation for DDoS and DoS attacks is to extort money. The cyber-attacker demands a ransom after sending a crippling DDoS attack. Then, the attacker will promise to halt the attack and restore back the network once a certain amount has been paid. This type of attack is facilitated by the presence of booter services and stresser.
More than a few well-known online software companies have fallen victim to these DDoS attacks, including Vimeo, MeetUp, Basecamp, and Bitly. Some even went temporarily offline, declining the requests of the extortioner.
Hacktivism
This is used by an ideological movement or group to launch personal and political attacks. Hacktivists use DDoS attacks to express their criticisms for everything, ranging from politics to current events. When these groups dislike your ideology, they take down your site. It isn’t unheard of for hacktivists to put the websites of political organizations or businesses they disagree with offline to stress their antagonism. One of the popular hacktivist groups is anonymous. Anonymous is accountable for
the cyber-attack against ISIS that occurred in 2015. Also, they are responsible for the attack against the Brazilian government and World Cup promoters that occurred in 2014.
Dissatisfied Worker
A Dissatisfied worker can launch a DDoS attack against their former employers particularly if they perceive they have been unjustly laid off, unpaid, or if there’s a breach of contract. Although some employees handle these objections more sensibly, others resort to cyber-attacks to take down the organization.
Cyber Warfare
Government sanctioned DDoS attacks can be exploited to cripple the infrastructure of a rival nation and to bring down the websites of an opposition group. These attacks are well funded and orchestrated by the government of a country. The aim of this type of attack is, to silent some internal antagonists and other government criticizers. It also serves as a means to upset serious health, economic, and organizational services in their rival countries.
Business Feuds
Businesses are now using these tools to settle business feuds. Sometimes these attacks are launched to keep a competitor from partaking in a significant business venture.
Whereas, other attacks are introduced to completely cripple a business and keep them offline indefinitely.
The motivation for this is to keep the competitor out of service so that their consumers would rush to the opposition. While this is taking place the reputation of the company would be tampered with and they will also encounter huge financial losses.
Business motivated attacks are often well-sponsored and accomplished by experts in the fields. These hackers perform timely investigation and exploit proprietary applications as well as resources to endure tremendously destructive and tenacious DDoS attacks.
How Can Denial of Service (DoS) Affect You
Distributed denial of service and Denial of service attacks are two of the most frightening threats faced by modern-day organizations. Only a few types of attacks can have such detrimental financial impacts as that of a successfully executed DDoS and DoS attack. A recent survey suggested that the average cost of a DDoS attack ranges between 20,000 dollars to 40,000 dollars per hour.
Not only will you be put out of action for a considerable period of time, but a successful DDoS attack can also cause some of your systems to start acting up. With each day you are unable to access your computer and other devices, you begin to incur costs you would otherwise have been spared. This is why you need a Certified Ethical Hacker to safeguard your systems and networks.
How to Stop DDoS and DoS attacks
You can’t prevent a DDoS attack and you can’t completely keep cyber-attackers from launching an attack. However, recognizing how to detect and mitigate a DDoS and DoS attack can be the difference between your company flourishing or going out of business. The impact of a successful attack can be so detrimental to the point that your business may be obliterated from the internet and your consumers inaccessible.
Monitor Your Traffic
You need to keep an eye on your traffic for signs of abnormalities, such as a mysterious spike in traffic and suspicious IP address and geolocation visits. If you are the administrator of your own servers, it is important that you are able to identify when an attack is happening. The more you know about your inbound traffic, the easier it is to spot an attack.
Nearly all DDoS attacks begin with sharp traffic spikes. All these could be symptoms of hackers executing “dry runs” to test your defenses before launching a full-sized attack. So, it would be helpful if you’re able to differentiate between an abrupt surge of genuine visitors and the beginning of a DDoS attack.
Even though your overprovision attempt may not necessarily avert an attack, it will give you some extra time to take deliberate actions before your website become completely saturated.
Make more Bandwidth Available
It is often advisable to make provisions for more bandwidths to your server than you would normally exhaust. By making overprovision bandwidth for your web servers, you can easily handle rapid and unanticipated surges in traffic that could arise due to a special offer, advertising crusade, or a mention of your organization in the media.

Monitor your Social media Pages and Public Waste Bins
It is vital for you to monitor your social media pages, particularly your Twitter account, and other public waste bins, including Pastebin.com for conversations, surges, and threats that may indicate a possible inbound attack. You should consider using third-party DDoS testing, to imitate possible DDoS assaults against your IT infrastructure. This way your incident responder or IRT can be prepared to tackle any level of assault.

Consult a Cybersecurity Expert
You need to consult a cybersecurity expert, particularly one that specializes in DDoS attacks. For large attacks, the ability to get your business back online may depend on a Cybersecurity expert. When you consult a cybersecurity expert, particularly
a Certified Ethical Hacker, they test a wide range of assaults and not only those with which you are acquainted.
Consult a Cybersecurity Expert
You need to consult a cybersecurity expert, particularly one that specializes in DDoS attacks. For large attacks, the ability to get your business back online may depend on a Cybersecurity expert. When you consult a cybersecurity expert, particularly
a Certified Ethical Hacker, they test a wide range of assaults and not only those with which you are acquainted.

A vital part of your incidence response plan is to have a plan for how to communicate you’re the attack to your consumers. Since these attacks can last for up to 24 hours, having a good communication plan would minimize the cost to your business. When you are prepared for an attack, including having an updated incident response plan, this will boost the trust of your customers.
Prevention and Mitigation Strategies
Effective prevention and mitigation strategies must be in place to defend against DoS attacks and strengthen and protect systems from the constantly evolving threat landscape of DoS attacks.
Creating a comprehensive security strategy against DoS attacks requires having both network and application layer defenses in place. By combining these approaches, organizations can improve their resilience against various attack vectors.
Here are some key defense measures for network and application layers:
- Use deep packet inspection (DPI) to analyze data packets for malicious signatures and anomalies.
- Implement web application firewalls (WAFs) to filter and monitor HTTP traffic, blocking harmful requests before they reach the server.
- Utilize intrusion detection systems (IDS) and intrusion prevention systems (IPS) to detect and prevent suspicious activities in real time.
- Employ Secure Sockets Layer (SSL) encryption to protect data integrity and confidentiality, making it harder for attackers to intercept and manipulate
- Integrate machine learning algorithms and artificial intelligence (AI) to identify and adapt to new attack patterns, enhancing the strength of your defenses against sophisticated threats.
Rate Limiting and Traffic Filtering
Set rate limits to throttle incoming requests to prevent overwhelming your servers. This approach helps manage a user’s requests within a specific timeframe, effectively mitigating potential denial of service (DoS) attacks.
Implement traffic filtering to distinguish between legitimate and malicious traffic, using criteria such as IP reputation and request patterns. By employing these measures, you can ensure genuine users maintain access while blocking harmful traffic. Real- time monitoring tools can adjust rate limits and filtering rules dynamically, providing an adaptive defense mechanism against evolving threats.
Use of Anycast Networks
Deploy anycast networks to distribute traffic across multiple servers, reducing the risk of a single point of failure. By routing requests to the nearest or least congested server, anycast enhances load balancing and minimizes latency. This strategy improves user experience and mitigates the impact of DoS attacks by dispersing malicious traffic.
For example, anycast can reroute traffic to unaffected servers during an attack, maintaining service availability. Cloud providers often utilize anycast to bolster their resilience, ensuring services remain operational and responsive even under duress.
This decentralized approach provides a robust layer of defense against targeted disruptions.
Incident Response and Recovery Plans
Organizations must establish vigorous incident response and recovery plans to counteract and recover from DoS attacks swiftly. Rapid identification of attack vectors and immediate isolation of affected systems are crucial.
Employ automated real-time monitoring and alerting tools to ensure swift detection and response. Develop a comprehensive recovery strategy that includes data backups, system redundancies, and predefined communication protocols. Regularly update and test these plans to adapt to evolving threats.
Organizations can minimize downtime, protect critical assets, and ensure business continuity despite persistent and sophisticated DoS attacks by maintaining a well- prepared incident response framework.
Quick Summary of Denial-of-Service (DoS) Attacks
Definition: A DoS attack disrupts or shuts down a target system by overwhelming it with excessive traffic, making it unresponsive to legitimate users.
Types of DoS Attacks:
- DoS DDoS: DoS originates from a single source; DDoS comes from multiple compromised systems (botnets).
- Buffer Overflow: Overloading a system’s memory buffer with excessive
- Application Layer: Targeting vulnerabilities in web apps to exhaust
- Protocol Attacks: Exploiting network protocol weaknesses (e.g., SYN flood, DNS amplification).
- Volumetric Attacks: Flooding networks with massive
- Cloud-Based: Attacking cloud infrastructure to disrupt
Indicators:
- Slow websites or network
- Sudden traffic spikes or abnormal
- Loss of
Causes: Motivations include extortion, hacktivism, business rivalry, and cyber warfare.
Impact: Financial losses, reputational damage, and operational disruptions.
Prevention:
- Traffic Monitoring: Watch for
- Increase Bandwidth: Handle traffic
- Security Measures: Use firewalls, IDS, and rate
- Incident Response: Have plans for quick
- By adopting these strategies, organizations can improve their resilience against DoS and DDoS attacks.




