Meritshot Tutorials
- Home
- »
- Enumeration in Cyber Security
Cyber Security Tutorial
-
What is cybersecurity?What is cybersecurity?
-
Introduction to LinuxIntroduction to Linux
-
Text Processing using GREP, SED, and AWKText Processing using GREP, SED, and AWK
-
Introduction to Ethical HackingIntroduction to Ethical Hacking
-
Footprinting and ReconnaissanceFootprinting and Reconnaissance
-
Scanning NetworksScanning Networks
-
Enumeration in Cyber SecurityEnumeration in Cyber Security
-
Vulnerability AnalysisVulnerability Analysis
-
System HackingSystem Hacking
-
Malware ThreatsMalware Threats
-
SniffingSniffing
-
Social EngineeringSocial Engineering
-
Denial-of-ServiceDenial-of-Service
-
Evading IDS, Firewalls, and HoneypotsEvading IDS, Firewalls, and Honeypots
-
Hacking Web ServersHacking Web Servers
-
Hacking Web ApplicationsHacking Web Applications
-
SQL InjectionSQL Injection
-
Hacking Wireless NetworksHacking Wireless Networks
-
Hacking Web ApplicationsHacking Web Applications
-
Hacking Mobile PlatformsHacking Mobile Platforms
-
IoT HackingIoT Hacking
-
Cloud ComputingCloud Computing
-
CryptographyCryptography
Enumeration in Cyber Security
Introduction to Enumeration
what does enumeration mean in cybersecurity?
- In simple terms, enumeration is the process of identifying user names, system names, network resources, sharing roles, and other services of a system to exploit any potential vulnerabilities.
Enumeration in Ethical Hacking
Enumeration is the third step in a standard Ethical hacking methodology, preceded by reconnaissance and scanning. While these two steps identify potential ‘doors’ into a system or network, enumeration pries these doors open to reveal what lies behind.
enumeration refers to the process of systematically gathering detailed information about a target system or network. This step follows reconnaissance and scanning, which serve as preliminary stages in identifying vulnerabilities. Enumeration dives deeper, focusing on extracting specific data that can lead to potential security weaknesses.
- While reconnaissance and scanning help hackers discover basic information such as open ports or services running on a target system, enumeration is about identifying user names, network shares, system names, services, and other crucial elements that can reveal weaknesses or entry points. The goal is to gather detailed data that may provide attackers with the ability to manipulate or compromise a
Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. It is a key component of ethical hacking and penetration testing, as it can provide attackers with a wealth of information that can be used to exploit vulnerabilities. It can also be defined as collecting detailed information about the target systems, such as operating and network infrastructure details.
Enumeration can be used in both an offensive and defensive manner.
Enumeration is one of the most important steps in ethical hacking because it gives hackers the necessary information to launch an attack. For example, hackers who want to crack passwords need to know the usernames of valid users on that system. Enumerating the target system can extract this information.
Enumeration can be used to gather any of the following information: (Key Aspects of Enumeration)
- Usernames and Groups: Enumeration helps identify the usernames and groups present in a target system. This is important because weak or common usernames (such as “admin” or “guest”) can be exploited for unauthorized access, especially if paired with weak
- Open Ports and Services: Through enumeration, attackers can discover open ports and the services running on a target system. This data is crucial for understanding what services are vulnerable to specific types of attacks (e.g., web servers, FTP servers, etc.).
- Shared Resources: Many systems share resources like files, printers, or By identifying shared resources, attackers may gain access to sensitive data or network infrastructure.
- Operating System and Version: Enumeration can also help determine the operating system in use and its version, which is vital for discovering known vulnerabilities that could be
- Network Infrastructure: Enumerating the network infrastructure allows attackers to learn about the topology, connected devices, and configurations, which can assist in lateral movement if they gain access to part of the
- Active Directory Information: In corporate environments, an Active Directory (AD) can store valuable information like usernames, passwords, and access Enumerating an Active Directory environment can reveal weaknesses in user management or privilege escalation opportunities.
- Passwords (sometimes): In certain cases, through enumeration, attackers might gain access to password hashes or even plaintext passwords, especially if improper security practices like weak hashing algorithms or insecure storage are
Methods of Enumeration
There are several tools and techniques available for enumeration, ranging from command-line utilities to commercial solutions. The choice of method often depends on the attacker’s knowledge of the target system and the resources available.
1. Command-Line Tools
- Netstat: A basic tool used to identify active connections and open ports on a
- Nmap: A widely used network scanner that can detect open ports, services, and potential
- Nslookup: A tool to query DNS records and gather information about the target
- Netcat (nc): A powerful tool for connecting to open ports and sending/receiving
- NBTScan: Used for scanning networks for NetBIOS information (names, shares, ), commonly used in Windows environments.
2. Specialized Enumeration Tools
- Enum4linux: A Linux tool used to enumerate information from Windows systems, including user lists, shares, and system
- Hydra: A tool used for password brute-forcing and enumeration of login
- SMBclient: A command-line tool to access and enumerate resources shared over the SMB (Server Message Block)
- LDAP Enumeration: Lightweight Directory Access Protocol (LDAP) is commonly used for querying and modifying directory services. Enumeration of an LDAP server can reveal a lot of information about users, groups, and network
3. Network Protocols for Enumeration
- SMB (Server Message Block): SMB is a file-sharing protocol used by Windows Enumerating SMB shares can provide access to valuable data or further insight into a system.
- DNS (Domain Name System): By enumerating DNS records, attackers can gather information about domain names, subdomains, mail servers, and other key
- SNMP (Simple Network Management Protocol): SNMP can be used to enumerate network devices such as routers, switches, and printers. Misconfigured SNMP services might leak sensitive
- Telnet/SSH: These protocols can be used to remotely connect to devices. Enumeration can involve identifying open Telnet/SSH ports and attempting to gain unauthorized access.
Why is Enumeration Important in Ethical Hacking?
- Enumeration is a vital step in ethical hacking, allowing attackers to gain an in- depth understanding of a target system or network. It helps identify devices, their locations, the services they offer, and potential vulnerabilities that could be By conducting an enumeration scan, attackers can determine open ports on devices, discover which services are accessible, and uncover the type of data being transmitted. This detailed information forms the foundation for identifying weaknesses that could be leveraged for unauthorized access.
- Though enumeration requires both time and patience, it is an essential part of the hacking process. It can be carried out manually or with automated tools, depending on the scale of the target and the specific needs of the assessment. Regardless of the method used, thoroughness is key. A comprehensive scan maximizes the amount of intelligence gathered, making it easier to pinpoint potential attack vectors.
- In essence, enumeration acts as a “blueprint” of a target system, outlining its structure and available resources. This insight allows ethical hackers to detect weak spots and vulnerabilities that could be exploited. Without enumeration, attempting to break into a system would be akin to trying to infiltrate a house without knowing its layout or where the entry points are. Once an attacker gains information such as usernames, shared resources, and open ports, they can attempt techniques like brute-force attacks, exploit service vulnerabilities, or escalate privileges to gain unauthorized access.
- For ethical hackers, enumeration is a critical stage in identifying and addressing vulnerabilities before malicious actors can exploit them, thereby enhancing the security of systems and
Details discussion on various types of Enumerations.
- NetBIOS(Network Basic Input Output System) Enumeration
- NetBIOS name is an exceptional 16 ASCII character string used to distinguish the organization gadgets over TCP/IP, 15 characters are utilized for the gadget name and the sixteenth character is saved for the administration or name record
- Programmers utilize the NetBIOS enumeration to get a rundown of PCs that have a place with a specific domain, a rundown of offers on the individual hosts in the organization, and strategies and passwords.
- NetBIOS name goal isn’t supported by Microsoft for Internet Protocol Version
- The initial phase in specifying a Windows framework is to exploit the NetBIOS It was initially an Application Programming Interface(API) for custom programming to get to LAN assets. Windows utilizes NetBIOS for document and printer sharing.
- A hacker who finds a Windows OS with port 139 open, can verify what assets can be gotten to or seen on the far off framework. In any case, to count the NetBIOS names, the distant framework probably empowered document and printer sharing. This sort of enumeration may empower the programmer to peruse or keep in touch with the distant PC framework, contingent upon the accessibility of offers, or dispatch a
- NetBIOS name list:
Name | NetBIOS Code | Type |
<host name> | <00> | UNIQUE |
<domain> | <00> | GROUP |
<host name> | <03> | UNIQUE |
<username> | <03> | UNIQUE |
<host name> | <20> | UNIQUE |
<domain> | <1D> | GROUP |
<domain> | <1B> | UNIQUE |
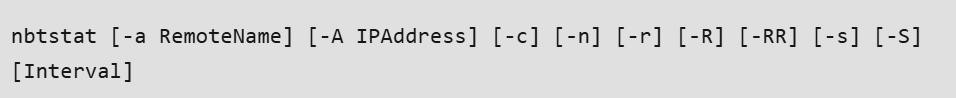
Nbtstat Utility: In Windows, it shows NetBIOS over TCP/IP (NetBT) convention insights, NetBIOS name tables for both the neighborhood and distant PCs, and the NetBIOS name reserve. This utility allows a resuscitate of the NetBIOS name cache and the names selected with Windows Internet Name Service. The sentence structure for Nbtstat:
Mitigation:
- Disable SMB and
- Use firewalls to restrict
- Disable file and printer
2. SNMP (Simple Network Management Protocol) Enumeration
Description: SNMP is used to manage and monitor network devices. Default community strings like “public” (read-only) and “private” (read/write) can be exploited by attackers to gather information.
Tools: NetScanTools Pro, SNMP Informant.
Mitigation:
- Disable SNMP or change default community
- Upgrade to SNMPv3 for better
- Apply strict access
3. LDAP (Lightweight Directory Access Protocol) Enumeration
Description: LDAP is used for accessing directory services. Attackers can query LDAP servers to gather sensitive information such as usernames, addresses, and organizational structure.
Tools: LDAP Admin Tool, Active Directory Explorer.
Mitigation:
- Use SSL/TLS for encrypted
- Enable account lockouts and ensure strong
4. NTP (Network Time Protocol) Enumeration
Description: NTP synchronizes the time between networked systems. Attackers can gather information about connected hosts, internal IPs, and operating systems from misconfigured NTP servers.
Mitigation:
- Implement NTP
- Configure MD5
- Upgrade NTP versions to more secure
5. SMTP (Simple Mail Transfer Protocol) Enumeration
Description: SMTP is used for sending emails. Attackers can use commands like VRFY, EXPN, and RCPT TO to list valid email addresses on a server.
Tools: Telnet, Metasploit, Nmap.
Mitigation:
- Disable open
- Ignore emails to unknown
- Limit the number of connections from the same
6. DNS Enumeration using Zone Transfer
Description: A DNS zone transfer allows attackers to gather a complete list of DNS records for a domain, revealing hostnames, IP addresses, and other sensitive data.
Mitigation:
- Disable DNS zone transfers to untrusted
- Hide private IP addresses in DNS
Use premium DNS services to secure records
7. IPsec Enumeration
Description: IPsec is used to secure VPN communications. Attackers can gather sensitive data related to cryptographic algorithms and key exchanges from vulnerable IPsec configurations.
Mitigation:
- Use advanced certificates and two-factor
- Limit VPN access to specific IP
- Use modern IPsec encryption
8. VoIP (Voice over IP) Enumeration
Description: VoIP systems, using protocols like SIP, can be enumerated to gather information about VoIP gateways, servers, user extensions, and protocols, which can be exploited for attacks.
Mitigation:
- Use SIP over TLS (SIPS) and implement proper
- Use digest authentication to protect VoIP
9. RPC (Remote Procedure Call) Enumeration
Description: RPC allows communication between clients and servers. Attackers can enumerate available RPC services to identify vulnerabilities and perform attacks.
Mitigation:
- Disable unnecessary RPC
- Patch RPC-related
- Filter traffic to minimize exposure to the public
10. Unix/Linux User Enumeration
Description: Linux/Unix systems can be enumerated for user information, which attackers can exploit to gain unauthorized access.
Mitigation:
- Regularly update the kernel and patch
- Avoid running services as root unless
- Restrict access to critical
11. SMB (Server Message Block) Enumeration
Description: SMB is a protocol used for sharing files and resources. Attackers can enumerate SMB shares to identify accessible resources and services, potentially leading to unauthorized access.
Mitigation:
- Implement strong passwords and authentication for SMB
- Disable SMBv1 and use SMBv2 or
- Regularly audit SMB shares for
Techniques for Enumeration
When it comes to network security, enumeration is key. By enumerating a system, you can gain a better understanding of that system and how it works. This knowledge can then be used to exploit vulnerabilities and gain access to sensitive data.
Several techniques can be used for enumeration, and your method will depend on the type of system you are targeting. The most common methods include email IDs and usernames, default passwords, and DNS zone transfer.
- Using email IDs and usernames is a great way to gather information about a You can use this information to brute force passwords or gain access to sensitive data. Default passwords are another common method of enumeration.
- By using default passwords, you can gain access to systems that have not been properly
- DNS zone transfer is a technique that can be used to expose topological This information can be used to identify potential targets for attack.
- Understanding the techniques available for enumeration can better protect your systems from attack.
How to Protect Against Enumeration?
Understanding how enumeration works can help you implement strategies to defend against it. Some key protections include:
- Firewalls: Implement network-level protections to block unnecessary ports and
- Access Control: Use strong password policies, two-factor authentication, and user privilege
- Intrusion Detection Systems (IDS): Deploy IDS to detect suspicious scanning or probing activity.
- Network Segmentation: Divide your network into segments to limit the exposure of sensitive
- Encryption: Use encryption to protect sensitive data, including passwords and network
Services and Ports to Enumerate
When conducting a penetration test or simply enumerating services on a target machine, knowing which ports are associated with it is often useful. This can be accomplished using a port scanner such as Nmap to scan for open ports on the target machine. Once you have a list of open ports, you can use a port lookup tool to determine which service runs on each port. This information can be extremely helpful when trying to identify potential attack vectors.
The following are some of the most commonly used services and their associated ports :
- FTP – 21
- SSH – 22
- HTTP – 80
- HTTPS – 443
- SMTP – 25
- POP3 – 110
- IMAP – 143
- SNMP – 161
As you can see, various services can run on any given port. Knowing which service runs on which port when enumerating a target machine is helpful.
The Enumeration Step of Security Testing
In security testing especially in penetration testing enumeration is an important phase that follows reconnaissance. In this phase, which often involves whistle blowing, testers escalate their function and seek to obtain as much information about the target system as they can. The end product is to look for the blind spots that can be exploited by a malicious user in order to compromise the system.
Key activities in the enumeration phase include:
Identifying User Accounts: Finding legitimate usernames and if possible, the passwords to go with them.
Mapping Network Resources: Identifying hidden resources, services and device on the network.
Extracting Configuration Data: They involve collecting information on the settings of the system, established security policies as well as the security measures in place.
Detecting Running Services: Gleaning service running and open ports which are potential gateway for an attack.
Summary
Enumeration plays a dual role in cybersecurity. For a cyber attacker, it is a means to gather information about potential system vulnerabilities, exploit them and gain unauthorized access. For an ethical hacker or network administrator, it helps identify these vulnerabilities first-hand, thereby providing valuable insights into hardening network security. Thus, understanding what enumeration means in cybersecurity is the first line of defense against the vast digital threats in today’s connected world.
Enumeration involves identifying user names, system names, network resources, and services in a system to exploit vulnerabilities.
Role in Ethical Hacking
As the third step after reconnaissance and scanning, enumeration provides detailed insights into the target system, aiding in potential exploitation.
Key Aspects
- Usernames and Groups: Identifies weak credentials for unauthorized
- Open Ports and Services: Detects possible attack entry points.
- Shared Resources: Exposes sensitive files, printers, or
- Operating System and Version: Helps discover OS-specific
- Network Infrastructure: Maps the network and connected devices for lateral
- Active Directory: Reveals user management weaknesses in corporate
- Passwords: May uncover password hashes or plaintext
Methods
- Command-Line Tools: Netstat, Nmap, Nslookup for basic data
- Specialized Tools: Enum4linux, Hydra for targeted
- Network Protocols: Leverage SMB, DNS, and SNMP for sensitive
Importance
Enumeration provides a detailed understanding of a target system, revealing exploitable vulnerabilities and forming the foundation for further attacks.




