Meritshot Tutorials
- Home
- »
- Introduction to Linux in Cyber Security
Cyber Security Tutorial
-
What is cybersecurity?What is cybersecurity?
-
Introduction to LinuxIntroduction to Linux
-
Text Processing using GREP, SED, and AWKText Processing using GREP, SED, and AWK
-
Introduction to Ethical HackingIntroduction to Ethical Hacking
-
Footprinting and ReconnaissanceFootprinting and Reconnaissance
-
Scanning NetworksScanning Networks
-
Enumeration in Cyber SecurityEnumeration in Cyber Security
-
Vulnerability AnalysisVulnerability Analysis
-
System HackingSystem Hacking
-
Malware ThreatsMalware Threats
-
SniffingSniffing
-
Social EngineeringSocial Engineering
-
Denial-of-ServiceDenial-of-Service
-
Evading IDS, Firewalls, and HoneypotsEvading IDS, Firewalls, and Honeypots
-
Hacking Web ServersHacking Web Servers
-
Hacking Web ApplicationsHacking Web Applications
-
SQL InjectionSQL Injection
-
Hacking Wireless NetworksHacking Wireless Networks
-
Hacking Web ApplicationsHacking Web Applications
-
Hacking Mobile PlatformsHacking Mobile Platforms
-
IoT HackingIoT Hacking
-
Cloud ComputingCloud Computing
-
CryptographyCryptography
Introduction to Linux
Table of Contents
- Overview
- History & Evaluation of Linux
- Linux vs Other Operating Systems
- Difference between Linux and Unix
- Functions of Linux OS
- Popular Linux Distributions (Distros)
- Choosing the Right Distro For Your Needs
- Kernel and Its Functions
- Command Line and Shell
- File System Hierarchy
- Linux Daemons and Processes
- Basic Linux Commands
- Permissions and Ownership
Linux, a Unix-like operating system, is built on the Linux kernel. This kernel, the heart of the system, oversees the interaction between the computer and its hardware, ensuring smooth and efficient operations. However, the kernel itself is incomplete. To form a fully functional operating system, it must be paired with a suite of software packages and utilities, collectively known as Linux distributions. These distributions provide the necessary tools and applications for users to securely and effectively run their software and accomplish tasks on their computers. Linux distributions come in various forms, each catering to specific user needs and preferences.
History & Evaluation of Linux
This operating system is built upon the Linux kernel (the core of the operating system) which was first released in 1991 by Linus Torvalds, a student from the University of Helsinki, Finland. Initially, Linux was only developed as a hobby and was not intended for widespread use. However, with the development of the internet, the Linux developer community grew, and Linux became increasingly popular. In 1993, Slackware became
the first commercially released Linux distribution. Following that, several other Linux distributions emerged such as Debian, Red Hat, SUSE, and Ubuntu. Linux has become a very popular operating system among software developers due to its ability to be customized and modified to meet user needs. Additionally, Linux is also popular among server and end-user users, especially in business and government organizations. With the development of technology, Linux has also evolved to support mobile devices such as smartphones and tablets. One of the popular Linux distributions for mobile devices is Android, which is used on most smartphones worldwide.
Linux vs Other Operating Systems
Feature | Linux | Windows | macOS |
Source Code | Open-source | Closed-source | Closed-source |
Licensing | Free | Commercial | Commercial |
Development | Community-Driven | Commercial development | Commercial development |
User Interface | Command-line interface (CLI) and graphical user interface (GUI) | Graphical user interface (GUI) | Graphical user interface (GUI) |
Hardware Support | Wide range of hardware | Wide range of hardware | Primarily Apple hardware |
Security | Highly secure due to open-source nature and community scrutiny | Moderate security, often targeted by malware | High security, but less customizable |
Cost | Free | Commercial licensing fees | Commercial licensing fees (bundled with Apple hardware) |
Target Users | Home users, developers, | Home users, businesses | Creative professionals, |
| businesses |
| designers, developers |
Customization | Highly customizable | Moderately customizable | Limited customization |
Stability | Highly stable, especially server versions | Generally stable, but can be prone to updates | Very stable, but less flexible |
Gaming | Limited gaming support, but improving | Wide range of gaming support | Limited gaming support, but improving |
Difference between Linux and Unix
Feature | Linux | Unix |
Source code | Open-Source | Proprietary |
Licensing | Free to use and modify | Requires a license to use |
Development | Community – driven | Commercial development |
Kernel | Linux Kernel | Various kernels (e.g., UNIX System V, BSD) |
Distributions | Multiple distributions (e.g., Ubuntu, Fedora, Debian) | Fewer commercial distributions (e.g., Solaris, AIX, HP-UX) |
User Interface | Command-line interface (CLI) and graphical user interface (GUI) | Primarily command-line interface (CLI) |
Hardware Support | Wide range of hardware | More limited hardware support |
Security | Highly secure due to open- source nature and community scrutiny | Secure, but proprietary nature limits community scrutiny |
Cost | Free | Commercial licensing fees |
Target Users | Home users, developers, businesses | Primarily businesses and servers |
Functions of Linux OS
Server Operating System: Linux is widely used as a server operating system due to its reliability, scalability, and security. It efficiently manages network resources and servers, making it ideal for businesses and organizations. Its flexibility allows for customization to meet specific needs.
Desktop Operating System: While not as popular as Windows, Linux distributions like Ubuntu and Mint offer user-friendly desktop environments. They can be used for various tasks, including browsing the web, creating documents, and even video editing.
Software Development Platform: Linux provides a powerful and flexible environment for software development. Its open-source nature allows developers to access and modify source code, fostering innovation and collaboration.
Embedded Systems: Linux’s lightweight kernel and modular design make it suitable for embedded systems, such as routers, smart TVs, and IoT devices. It offers a robust and efficient platform for these devices.
Open-Source Philosophy: Linux’s open-source nature empowers users and developers. It allows for customization, sharing, and community-driven development, leading to a diverse ecosystem of software and tools.
Overall, Linux’s versatility and flexibility make it a compelling choice for a wide range of users and applications. Its open-source nature encourages innovation and community- driven development, ensuring its continued growth and evolution.
Popular Linux Distributions (Distros)
Linux, a versatile operating system, is available in numerous distributions, each offering unique features and catering to different user needs. Here are some of the most popular Linux distributions:
1. Ubuntu
- User-Friendly: Known for its user-friendly interface and extensive software repository, Ubuntu is a popular choice for both beginners and experienced
- Regular Updates: Ubuntu releases new versions every six months, ensuring access to the latest features and security patches.
- Diverse Applications: It comes pre-installed with a wide range of applications, including office suites, web browsers, and media players.
2. Linux Mint
- Elegant Design: Linux Mint is renowned for its elegant and customizable desktop environments, such as Cinnamon and MATE.
- Easy Installation: The installation process is straightforward, making it accessible to users of all levels.
- Multimedia Support: It includes multimedia codecs out of the box, eliminating the need for additional installations.
3. Debian
- Stable and Reliable: Debian is known for its stability and long-term
- Security-Focused: It prioritizes security and undergoes rigorous testing before
- Customizable: Debian offers a high degree of customization, allowing users to tailor it to their specific needs.
4. Red Hat Enterprise Linux (RHEL)
- Enterprise-Grade: RHEL is a popular choice for businesses due to its stability, security, and long-term support.
- Performance and Reliability: It is optimized for performance and reliability, making it suitable for mission-critical applications.
- Robust Security: RHEL incorporates robust security features to protect against cyber threats.
5. Fedora
- Cutting-Edge Technology: Fedora is a cutting-edge distribution that often includes the latest software and features.
- Community-Driven: It is driven by a vibrant community of developers, contributing to its continuous improvement.
- Open-Source Philosophy: Fedora adheres to open-source principles, promoting transparency and collaboration.
Choosing Right Distro For Your Needs
Selecting the optimal Linux distribution hinges on a clear understanding of your specific requirements. Here are key factors to consider:
1. Experience Level
- New Users:
- Ubuntu: Offers a user-friendly interface, extensive software repositories, and a strong community.
- Linux Mint: Known for its elegant desktop environments (Cinnamon and MATE) and ease of use.
➢ Intermediate Users:
- Fedora: Provides cutting-edge software and a focus on
- Debian: Offers stability, security, and a high degree of
➢ Advanced Users:
- Arch Linux: A highly customizable distribution that requires technical
- Gentoo Linux: Offers ultimate flexibility but demands significant technical
2. Hardware Considerations
- Older Hardware: Lightweight distributions like Lubuntu or Xubuntu are ideal for older machines due to their low system resource requirements.
- Modern Hardware: Most modern distributions, including Ubuntu, Fedora, and Pop!_OS, work well on newer hardware.
3. Specific Use Cases
- Daily Driver:
- Ubuntu: Well-rounded and suitable for everyday
- Linux Mint: Elegant and customizable desktop
➢ Gaming:
- Pop!_OS: Optimized for gaming
- Manjaro Linux: User-friendly Arch-based distribution with gaming
➢ Server:
- Ubuntu Server: Popular for web servers, file servers, and
- Debian Server: A stable and secure server
➢ Development:
- Fedora: Offers a cutting-edge development
- Ubuntu: Provides a wide range of developer tools and
4. Additional Factors
- Community Support: A strong and active community can provide valuable
- Software Availability: Ensure your preferred software is available in the distribution’s repositories.
- Long-Term Support (LTS): Consider LTS versions for stability and
Tips for Choosing a Distro:
- Research and Community: Explore online forums and communities to gather
- Consider Your Workflow: Choose a distribution that aligns with your work habits and preferences.
Kernel and Its Functions
If we think of the Linux operating system in terms of layers, the kernel is the lowest layer. It interfaces directly with the computer hardware and is responsible for allocating and managing the resources available to programs. It allocates processor time and memory to each program and determines when each program will run. The kernel also provides an interface to programs whereby they may access files, the network, and devices.
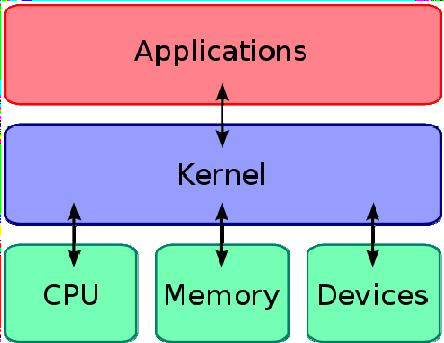
Key Functions of the Kernel:
- Resource Management:
- Memory Management: The kernel allocates and deallocates memory to different processes, ensuring efficient utilization of system RAM.
- Device Management: It manages the input/output operations of various hardware devices, such as disk drives, printers, and network interfaces.
- CPU Scheduling: The kernel determines which process gets CPU time, optimizing system performance and ensuring fairness among different
2. System Call Handling:
- When a user application needs to perform a system-level operation (e.g., reading a file, opening a network connection), it makes a system call to the
- The kernel handles these system calls, executes the requested operation, and returns the result to the application.
3. Security:
- The kernel enforces security policies to protect system resources from unauthorized access.
- It controls user access to files and devices, preventing unauthorized
4. Inter-Process Communication:
- The kernel facilitates communication between different processes, enabling them to exchange data and synchronize their activities.
Command Line and Shell
Command Line
- Interface: A text-based interface where you input commands
- Functionality: Provides a way to interact with the operating system and execute
- Examples: The black screen with a blinking cursor you see in Linux or the Command Prompt in Windows.
Shell
- Program: A program that interprets and executes commands entered at the command line.
- Functionality: Acts as a bridge between the user and the operating
- Examples: Bash (Bourne Again Shell), Zsh (Z shell), and
In essence:
- Command Line is the interface through which you
- Shell is the program that processes those
Analogy: Think of the command line as a keyboard, and the shell as the software that processes the keystrokes to perform specific actions.
File System Hierarchy
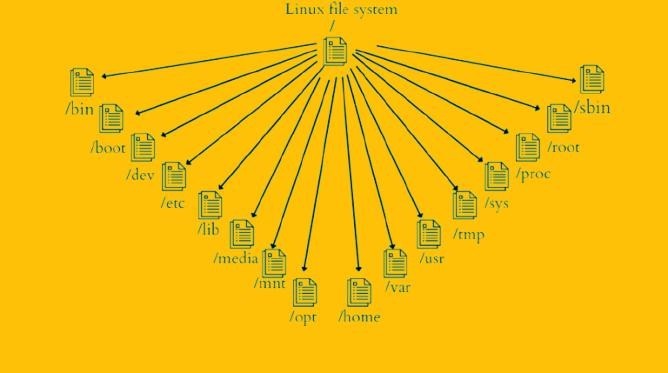
The Linux file system is organized in a hierarchical structure, with the root directory / at the top. This structure, known as the Filesystem Hierarchy Standard (FHS), provides a consistent and standardized way to organize files and directories across different Linux distributions.
Here’s a breakdown of the primary directories:
Root Directory (/)
- The starting point of the entire file system
Essential Directories:
- /bin: Contains essential binaries (executable programs) that are needed in single- user mode.
- /boot: Stores the kernel and boot loader files required to start the
- /dev: Contains device files that represent hardware
- /etc: Stores system configuration
- /home: Contains home directories for individual
- /lib: Contains shared libraries used by
- /mnt: Mount point for temporary file systems, like USB drives or network
- /opt: Optional application software
- /root: The home directory of the root
- /sbin: Contains essential system binaries, typically only accessible to the root
- /tmp: Temporary
- /usr: Contains most user programs and
- /var: Stores variable data, such as log files, mail spools, and temporary
- /media: This directory is a mount point for removable media devices, such as USB drives, external hard drives, and SD cards.
- /sys: This is a virtual filesystem that provides information about system hardware and kernel parameters.
- /proc: Another virtual filesystem, /proc provides information about the current state of the system, including running processes, memory usage, and network
Linux Daemons and Processes
Daemons
A daemon is a type of program on UNIX-like operating systems that runs unobtrusively in the background rather than being directly invoked by a user. It operates passively, waiting for specific conditions or events to trigger its execution.
UNIX-like systems typically run numerous daemons to handle various tasks, such as responding to network service requests, monitoring hardware activity, or interacting with other software. Examples of conditions or events that might activate a daemon include a scheduled date or time, the passage of a defined time interval, the receipt of a web or email request, or the arrival of a file in a designated directory.
Daemons operate independently of the user who triggers the associated condition or event. While the user initiating the action may not be aware of the daemon’s presence, some programs are explicitly designed to perform actions that implicitly trigger daemons.
Daemons, also referred to as background processes, typically have names ending with the letter “d.” For instance, sshd handles SSH remote access connections, and httpd manages the Apache web server. Many daemons are initialized during system startup.
On Linux systems, shell scripts located in the /etc/init.d directory are commonly used
to start, stop, or manage daemons. These scripts enable administrators to control the behavior of background processes as needed.
Processes
Daemons in Linux are typically implemented as processes, which are instances of programs in execution. These processes are managed by the kernel—the core of the operating system—which assigns each one a unique process identification number (PID).
In Linux, there are three main types of processes:
1. Batch Processes
These are submitted to a process queue and operate independently of the command line. Batch processes are well-suited for repetitive tasks, especially during periods of low system usage.
2. Interactive Processes
These are initiated directly by a user via the command line and are executed interactively.
3. Daemon Processes
These are background processes distinguished by the fact that their parent process has a PID of 1. This indicates that the init process is their parent. The init process is the first process launched when the system boots and remains active until the system shuts down.
The init process also adopts orphaned processes—that is, processes whose parent has terminated—ensuring they can continue running without disruption.
A common technique for creating a daemon involves forking the process (often once or twice) and allowing the parent process to terminate. This ensures the child process runs independently in the background, performing its intended function without direct association with the user or terminal session.
Basic Linux Commands
Here are some basic Linux commands with brief descriptions:
File and Directory Management
1 ls
Lists files and directories in the current directory. Example: ls -l displays detailed information.
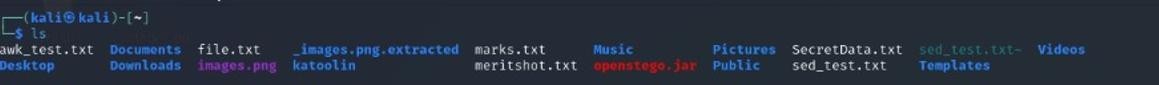
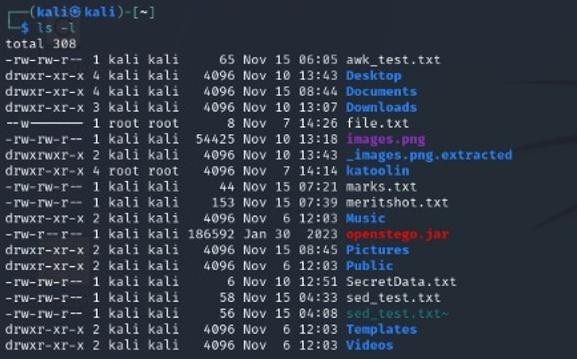
2. cd
Changes the current working directory.
Example: cd Documents navigates to Documents.

3. pwd
Displays the current working directory.

4. mkdir
Creates a new directory.
Example: mkdir meritshot creates a directory named meritshot.
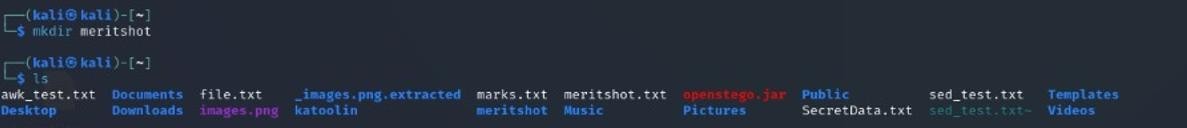
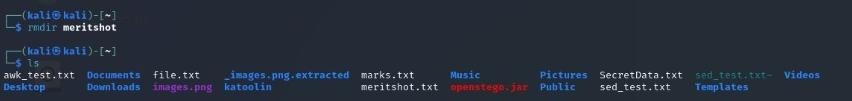
5. rmdir
Removes an empty directory. Example: rmdir old_folder.
6. rm
Deletes files or directories.
Example: rm file.txt removes a file, rm -r folder_name removes a directory and its contents.
7. cp
Copies files or directories.
Example: cp source.txt destination.txt duplicates a file.
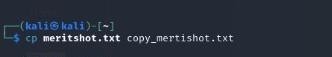

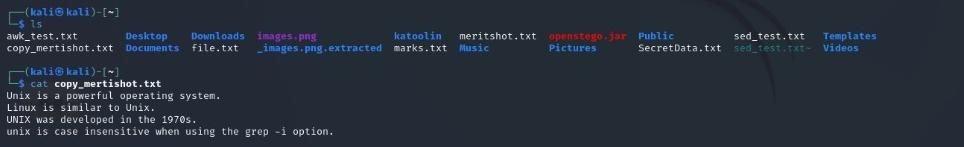
8. mv
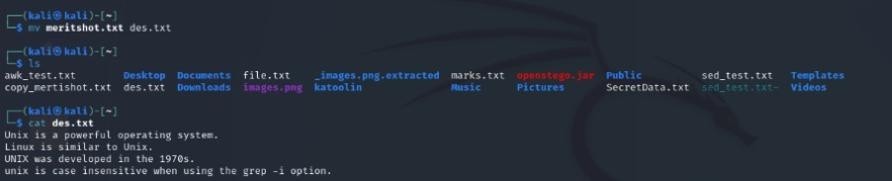
Moves or renames files or directories. Example: mv meritshot.txt des.txt.
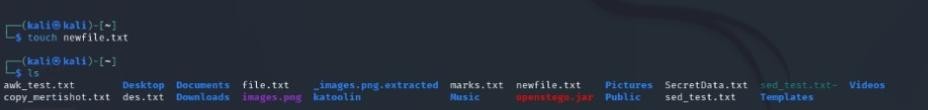
9. touch
Creates an empty file or updates the timestamp of an existing file. Example: touch newfile.txt.
1. find
Searches for files and directories.
Example: find / -name file.txt searches for file.txt starting from the root.
File Content
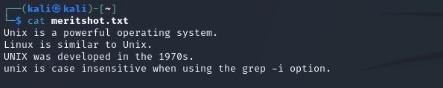
- cat
Displays the contents of a file. Example: cat meritshot.txt.
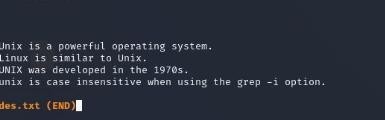
2. less
Views file content one screen at a time. Example: less des.txt.
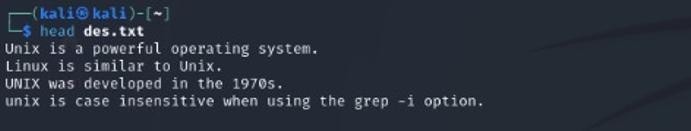
3. head
Shows the first few lines of a file. Example: head des.txt.
4. tail
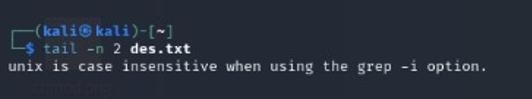
Displays the last few lines of a file.
Example: tail -n 2 file.txt shows the last 5 lines.
5. grep
Searches for patterns in a file. Example: grep “UNIX” des.txt.
Permissions and Ownership
whoami
Prints the current user.

id
Displays user ID and group ID information.
chmod
Changes file permissions.
Example: chmod 755 script.sh.
chown
Changes file ownership. Example: chown user:group file.txt.
sudo
Executes a command with superuser privileges.
Example: sudo apt update.




